Google Security Operations SIEM (Google Chronicle)
Integrate your Google Security Operations SIEM (Google Chronicle) tenant with Query Federated Search to dispatch parallelized searches without needing to write any UDM, all results are returned in OCSF format.
TL;DRTo integrate Google SecOps SIEM with Query:
- Create a Service Account with the Chronicle API Admin Role and generate a JSON Key.
- Retrieve the Project ID (or Number), Location Name, and Customer ID of your Google SecOps tenant.
- Retrieve the name(s) of the Feed(s) you wish to onboard and use the no-code Configure Schema workflow to map from UDM to the Query Data Model (QDM).
- Use Query Federated Search to support Incident Response, Investigations, Threat Hunting, Audit, and other security & observability tasks across normalized data from your Google SecOps SIEM.
Overview
Google Security Operations (SecOps) - formerly known as Google Chronicle - is a “cloud service, built as a specialized layer on top of core Google infrastructure that enables security teams to store and analyze their security data in one place and to detect, investigate, and respond to threats”. Google SecOps boasts an impressive catalog of ingestion from all native Google Cloud logging, Google Cloud Security Command Center, agent-based and collector-based ingestion, and several 100 pre-built “feeds” which are ingested into the SecOps platform and automatically enriched and grouped.
This grouping is achieved by normalizing all data into the Unified Data Model (UDM) which also doubles as a dot-notation typed query language - that way the results and the queries are all in the same formats. In a way, UDM is not unlike OCSF, but the schema rules and normalization are contrasting.
The Google SecOps Connector for Query Federated Search enables customers to federate querying of any data in their Google SecOps SIEM instance. Query handles parsing the specific Log Type from any given Feed, retrieving the UDM schema for it, and fetching sample data so customers can map the UDM data into the Query Data Model (based on the Open Cybersecurity Schema Framework) using our Configure Schema no-code workflow.
Once the data is onboarded into your Connector(s), you can describe your searches in QDM/OCSF terms such as with Entities (Observables) and Event Classes, and specific Attributes. Query Federated Search handles query translation and optimization into UDM, it transforms all UDM data into OCSF data as per your mappings from Configure Schema, and parallelizes all searches across different Feeds to get you answers quicker. Google SecOps normalization into UDM is a boon for in-place enrichment of data with important Open Source Intelligence (OSINT) data, Query Federated Search unlocks the value in that data without needing to become an UDM expert.
For instance, you can map several normalized UDM fields into specific Entities and Attributes within the QDM/OCSF schema, such as accounting for the various ways that an IP Address, Hostname, or Process Name can be expressed in UDM. QDM/OCSF defines nearly 3 dozen Entities that are not supported in UDM to enable different use case searching and parallelizing searches of like-data points without needing to use computationally expensive compound UDM queries or remembering what UDM attribute and depth describes a severity, an indicator, a behavior, an intrusion set, or otherwise.
Prerequisites
To integrate Query Federated Search with Google SecOps SIEM, ensure that you have fully setup your Google SecOps instance according to Google's documentation - this includes setting up the Google Cloud Platform (GCP) Project, configuring your identity provider, and setting up your first Ingestion.
The following steps will walk you through what information you need to retrieve to configure your Query Federated Search Connector for Google SecOps.
-
Navigate to your GCP Project and from the home screen, copy either the Project number OR Project ID for the GCP Project associated with your SecOps instance as shown below (FIG. 1).
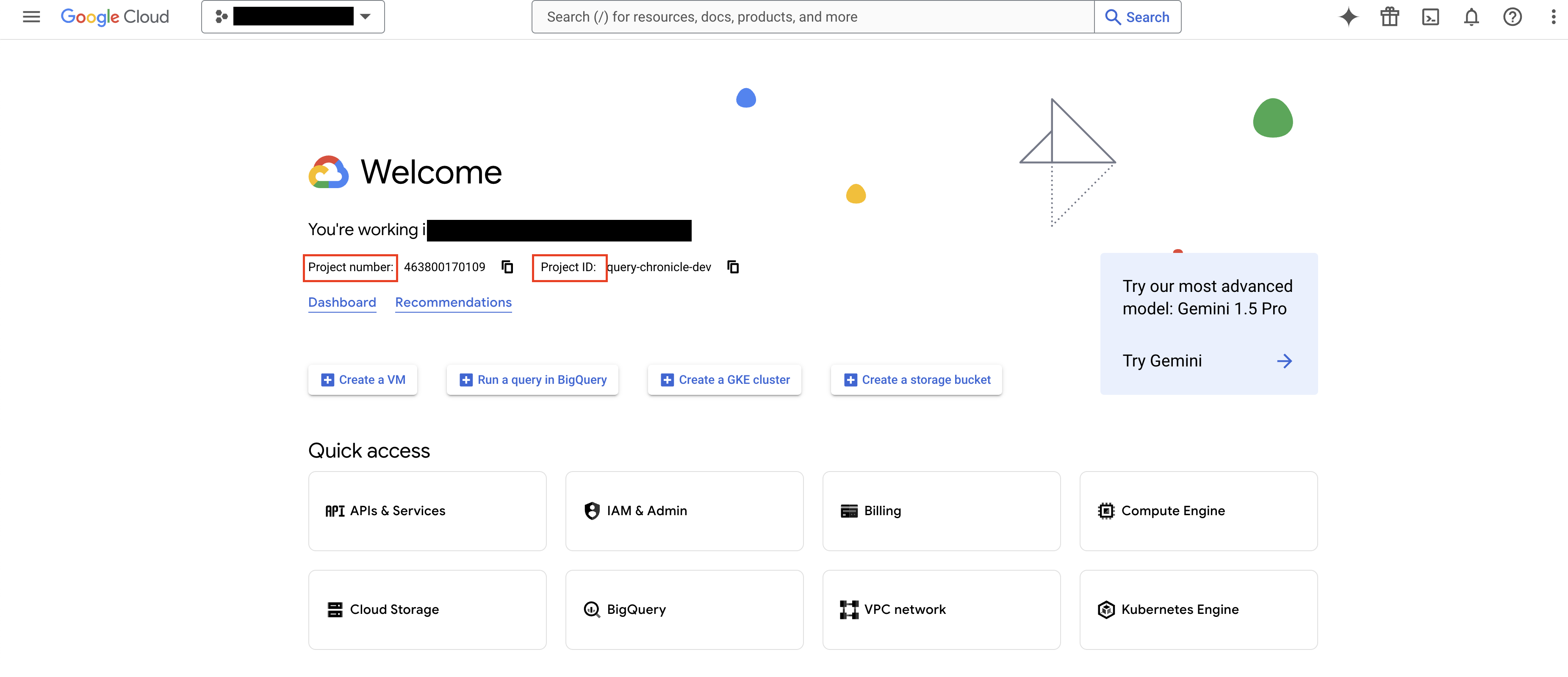
FIG. 1 - Retrieving the GCP Project number or Project ID
-
In the navigation menu on the top-left of the console, navigate to IAM & Admin --> Service Accounts and select + Create Service Account from the top-left of the console as shown below (FIG. 2).
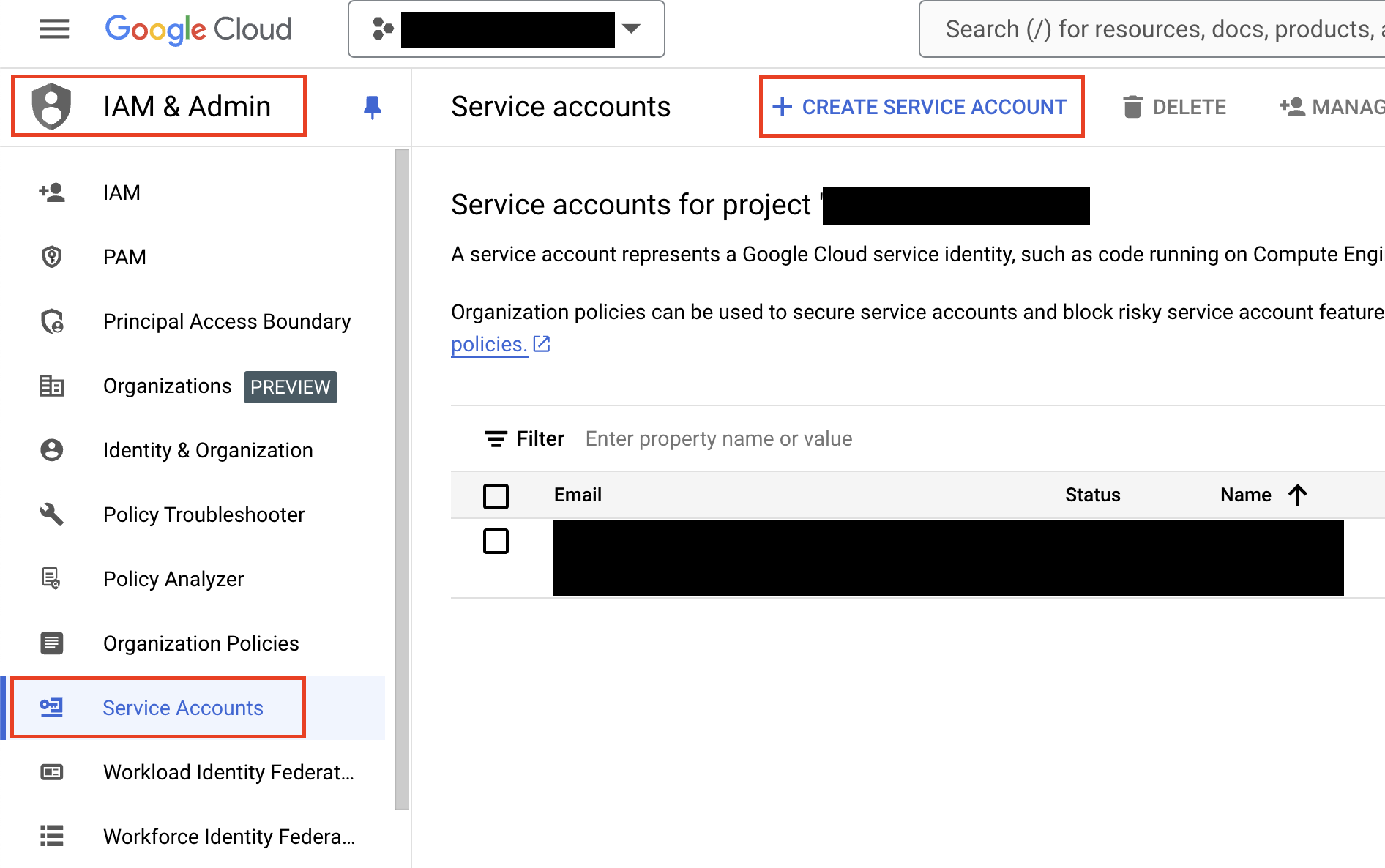
FIG. 2 - Creating a Service Account in the GCP Console
-
In the Service account details section provide a Service account name and an optional Service account description and select Create and Continue. In the next section, select the Chronicle API Admin Role as shown below (FIG. 3) and then select Done.
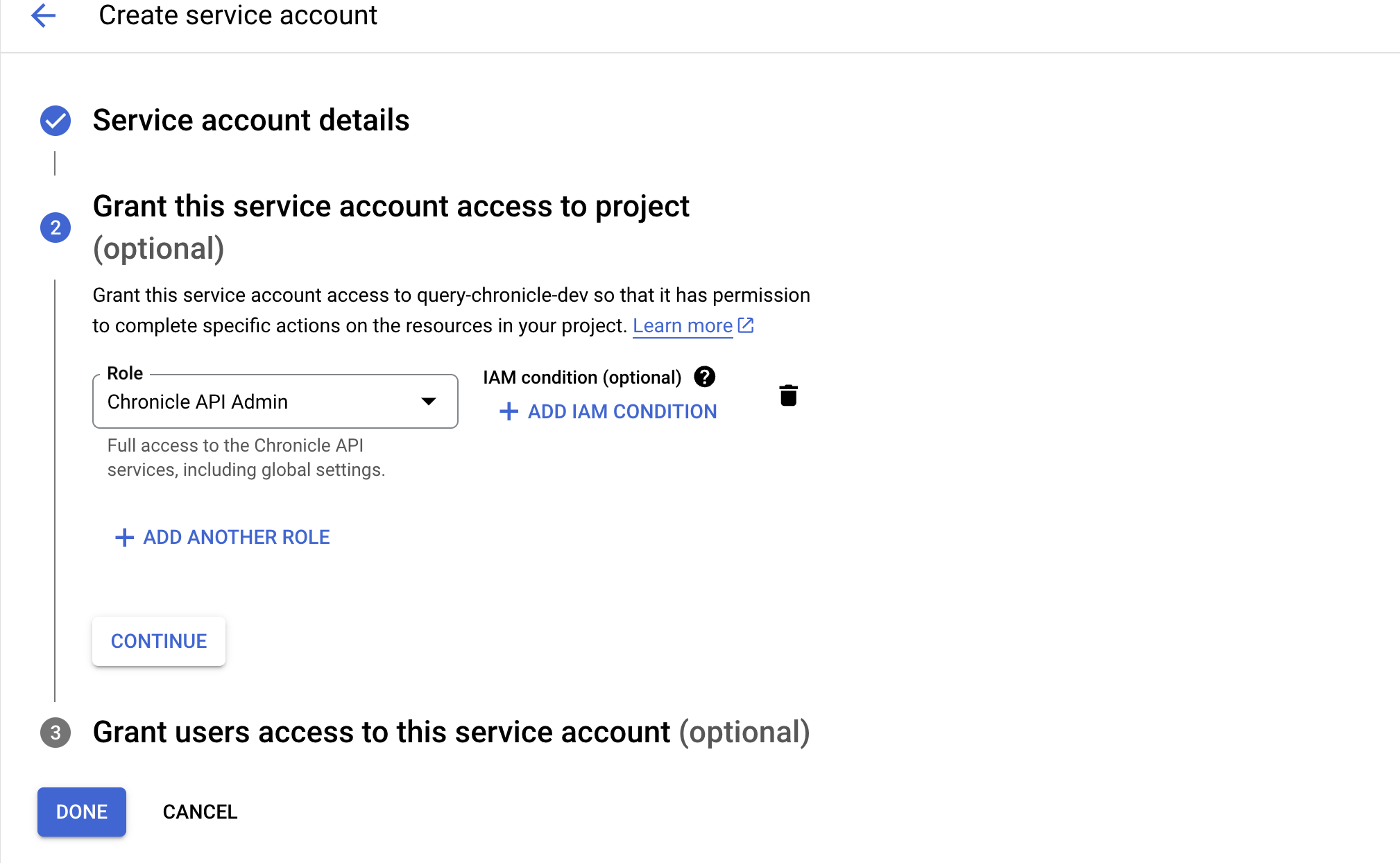
FIG. 3 - Adding the IAM Role to the Service Account
-
Once complete, select your Service Account, navigate to the Keys tab, select Add Key --> Create new key as shown below (FIG. 4).
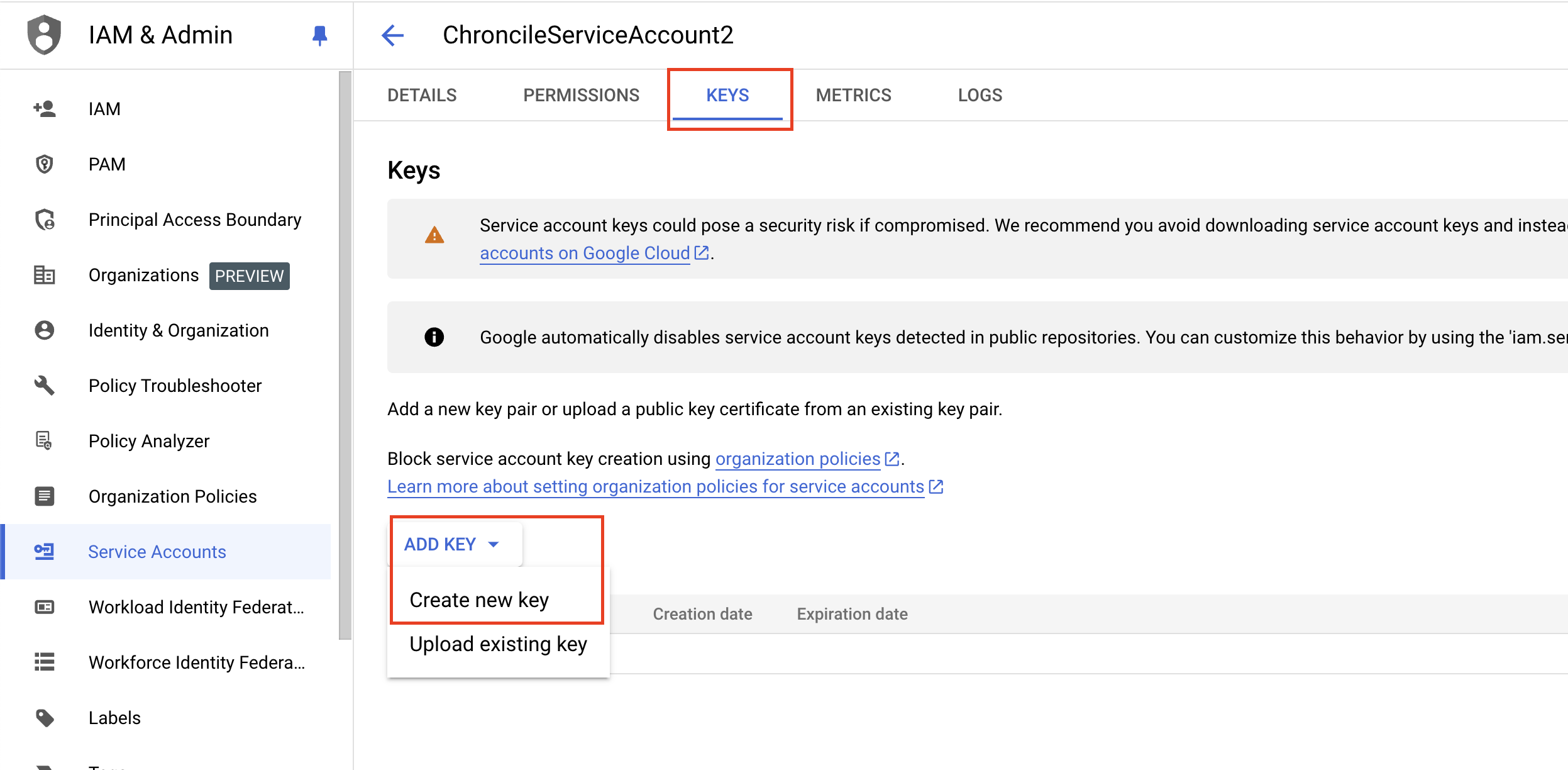
FIG. 4 - Creating a new key for your Service Account
-
Ensure that you select JSON for your Key type and select Create. The key will automatically be saved to your local filesystem, you will need to paste the contents of the Service Account key into your Query Federated Search Connector for Google SecOps.
-
Next, login to your Google SecOps console and in the navigation pane in the left-hand side select Settings --> SIEM Settings --> Profile. Copy the value of the Customer ID and double check your Project number or Project ID as shown below (FIG. 5).
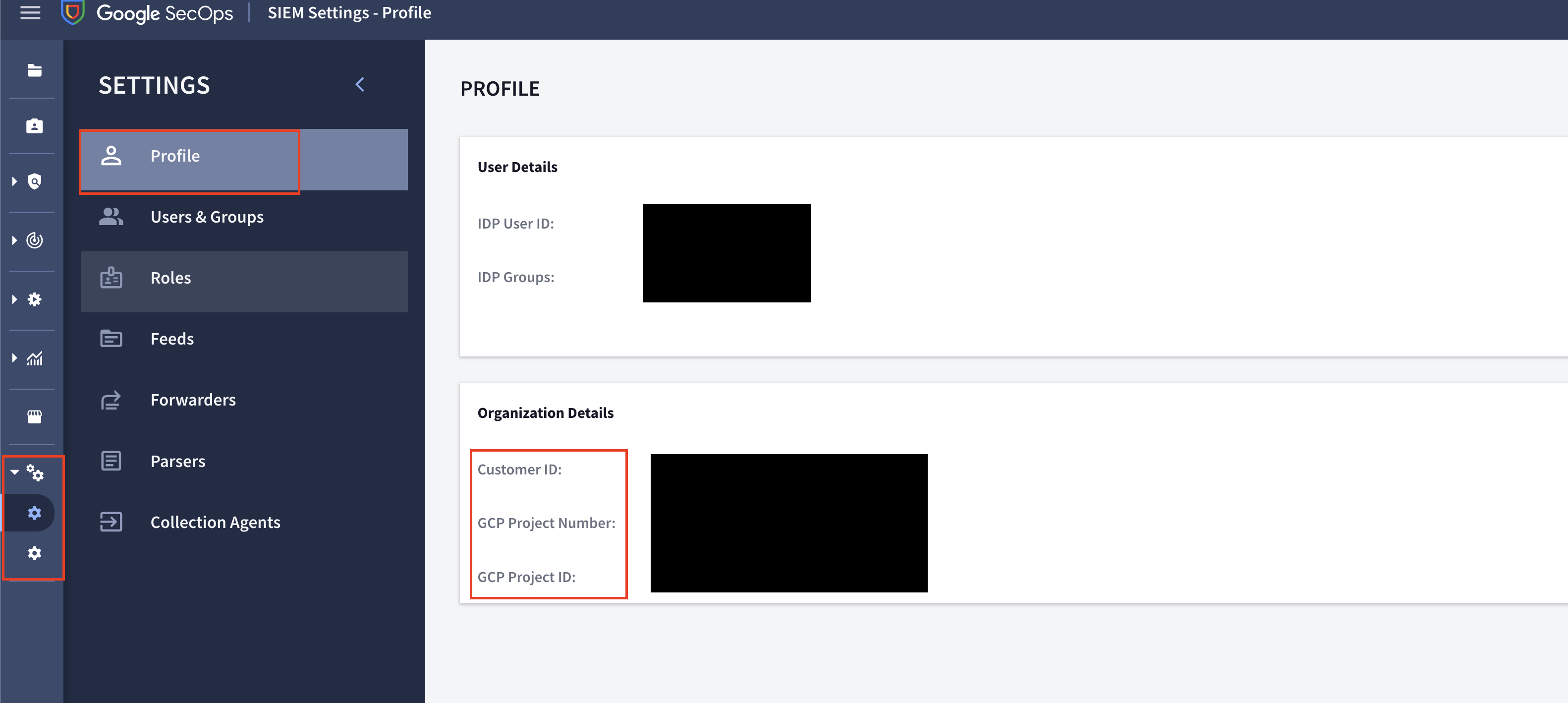
FIG. 5 - Retrieve the Customer ID from Google SecOps
-
Finally, navigate to the Feeds submenu and copy one or more Feed Name(s). Query discovers the UDM
metadata.log_typefrom the name of the Feed to be able to retrieve the appropriate UDM schema for any given Feed. The Log Type shown in the console does not match the syntax of the API.
Proceed to the next section to learn how to configure your Query Federated Search Connector for Google SecOps.
On NHI securityNHI - or, Non-Human Identities - such as your GCP Service Account JSON Key is extremely sensitive. Query securely stores the Client Secret in a dedicated AWS Secrets Manager Secret per Connector per Tenant.
Every Secret is stored as securely as each other with minimum necessary permissions that only allows the specific piece of serverless infrastructure to retrieve the secret, it is never cached or persisted outside of the Secret.
Configure the Google SecOps (Google Chronicle) Connector
Use the following steps to create a new Query Federated Search Connector for Google SecOps.
-
Navigate to the Connectors page, select Add Connector, and selectGoogle SecOps (Chronicle) from the SIEM and Log Management category as shown below (FIG. 6). Alternatively you can use the search bar to find the Connector.

FIG. 6 - Locating the Query Federated Search Connector for Google SecOps
-
In the Configure Connector section, add the following detail as shown below (FIG. 7):
-
Connector Alias Name: The human-readable name you want to give to this connector, you can provide the name of the feeds or another descriptive name such as a specific tenant or location, especially if you are a MDR/MSSP.
-
Default Login: Leave the default value:
Default Login. -
Google Cloud Project ID: The Project Number or Project ID of the GCP Project associated with your Google SecOps tenant, copied in Step 1 of the Prerequisites section.
-
Google SecOps Location Name: The region code of your Google SecOps tenant, for North American tenants this is typically
us, for tenants in the European Union this is typicallyeu. For all other locations, ask your Google Account Team for the specific regional code. -
Google SecOps Instance (Customer) ID: The Customer ID (sometimes call the Instance ID) of your Google SecOps tenant. Copied in Step 6 of the Prerequisites section.
-
GCP Service Account JSON: The contents of the JSON Key from the GCP Service Account you created to provide access to your Google SecOps APIs in Steps 2-5 of the Prerequisites section.
-
Feed Name: The name of your Google SecOps SIEM Feed you want to onboard into Query Federated Search, Copied in Step 7 of the Prerequisites section.
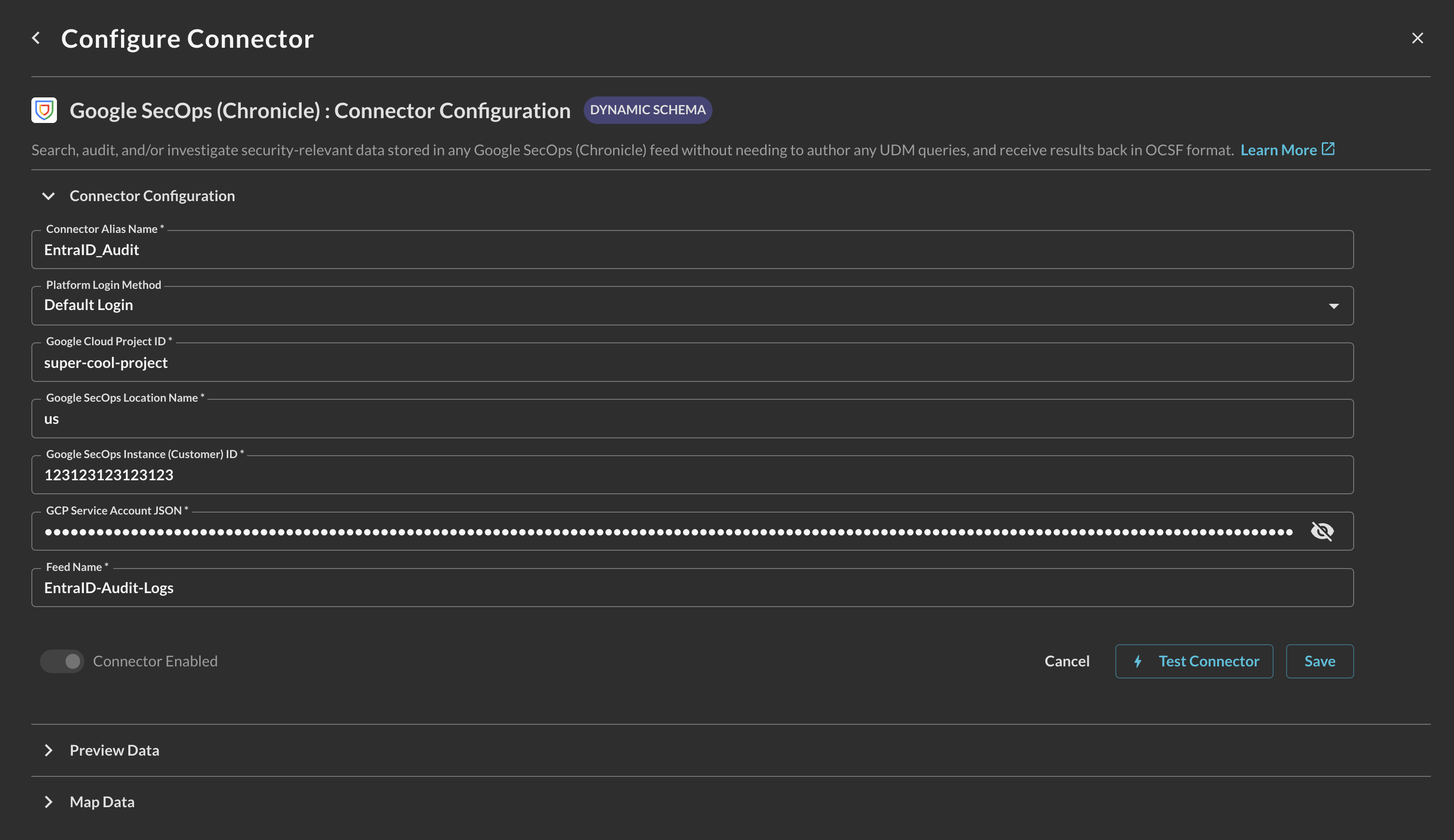
FIG. 7 - Configuring the parameters for the Query Federated Search Connector for Google SecOps
-
-
Select Save to save and activate the Connector.
-
Select Test Connection from the bottom-right of the connection pane to ensure that your API Credential Client ID and Client Secret are valid, that your Dataset is valid, and that Query can successfully dispatch a search against it.
-
Finally, proceed to the Preview Data section to begin the Configure Schema process. Refer to the hyperlink to learn how to use the Configure Schema no-code workflow, it is HIGHLY recommended for first time users.
You will now see Google SecOps (Chronicle) added as an available Connector within the Query Search and Query Summary Insights UI.
Querying Google SecOps (Google Chronicle) Connectors
Within the Query Search UI, all Connectors are enabled by default. To check that your specified Connector(s) for Cribl Search are enabled, navigate to the SIEM and Log Management section of the Selected Connectors dropdown and ensure that your specified Google SecOps (Chronicle) Connector(s) are are selected (denoted by a checkbox) before running your searches as shown below (FIG. 8).
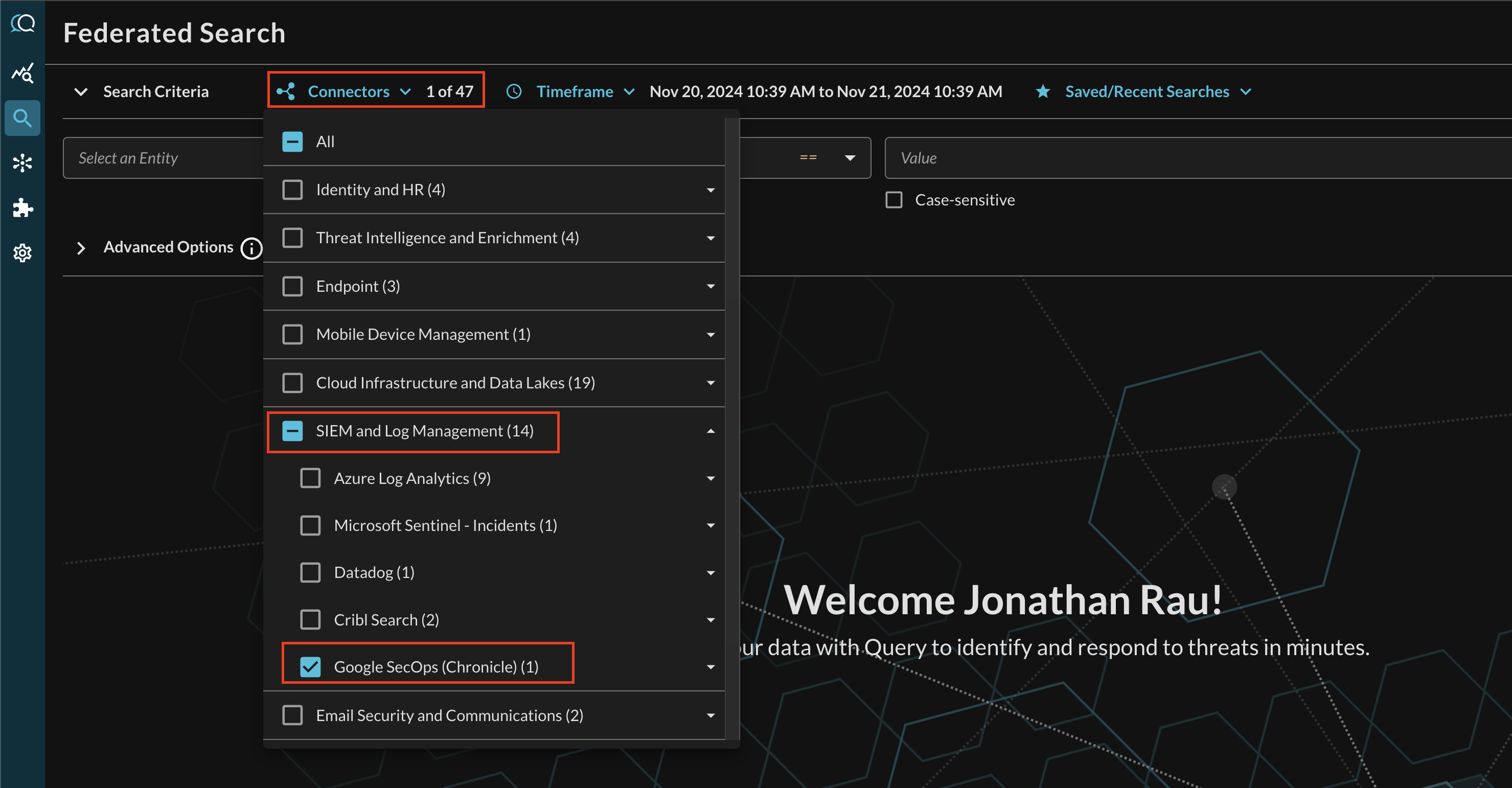
FIG. 8 - Selecting Google SecOps from the Connectors menu
The Entities (Observables) and Events you will be able to search determine on how you mapped your data in Configure Schema against a given Google SecOps Feed (metadata.log_type). For more information about the QDM/OCSF schema itself refer to the About the Query Data Model section of the Query docs, you can also view the Categories, Events, and Objects themselves.
Entity-based Search
To conduct an Entity-based search, ensure that all of the data points you will be searching for are mapped within the Configure Schema wizard as demonstrated in the previous section.
In the Federated Search console, select the search dropdown, ensure the Entities radio button is selected and search for your desired Entity as shown below (FIG. 9). For instance, you can search for an IP Address across various Google SecOps SIEM Feeds, these can be further correlated against other Feeds and different Query Connectors such as data in Google BigQuery, Google Workspace, the Gmail API, or other systems.
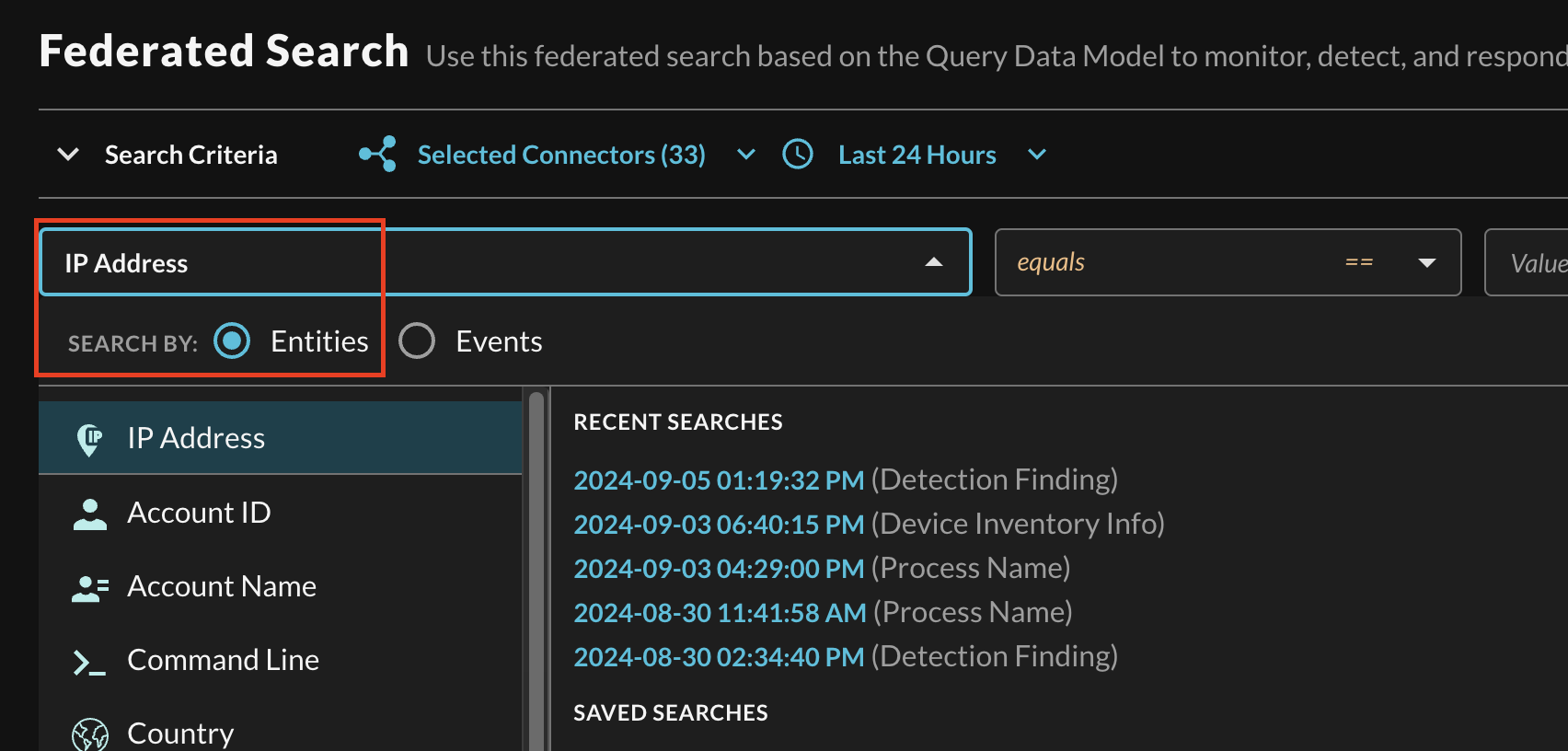
FIG 9. - Selecting a specific Entity from the search dropdown
After selecting an Entity, most allow you to specify an Operator. This allows you to perform simple equality searches or to perform more generalized searches using Contains, Starts With, or Ends With Operators. These are mapped against its appropriate UDM operator.
When you search for multiple values that may be present across different tables, the Query Federated Search query planner inspects the Configure Schema metadata to ensure searches are sent to the appropriate Feeds (using metadata.log_type) - as well as other applicable Query Connectors.
Additionally, you can specify case-sensitivity for the entire search criteria. An example of a multi-value "Hostname contains" search is shown below (FIG. 10).
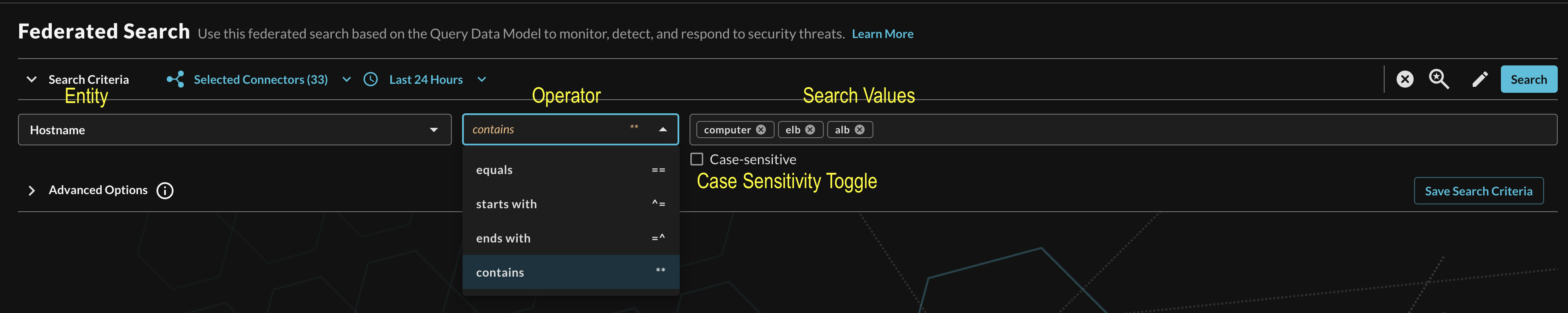
FIG. 10 - Orientation for Entity-based search in Query
Event-based Search
To conduct an Event-based search, ensure that all of the data points you will be searching for are mapped within the Configure Schema wizard as demonstrated in the mapping section. Within the Federated Search console, only mapped Events per the Select Connectors are populated, unlike Entities which has every potential value shown in the list.
In the Federated Search console, select the search dropdown, ensure the Events radio button is selected and search for your desired Event as shown below (FIG. 11). For instance, you can search for all API Activity events which you can normalize against several built-in Google SecOps Feeds such as Entra ID Audit Logs or Okta API Logs, in addition you can also search across all Connectors normalized to API Activity such as AWS CloudTrail Management Events stored in AWS Security Lake, System Event logs in Okta, and Audit Events in Microsoft Intune.
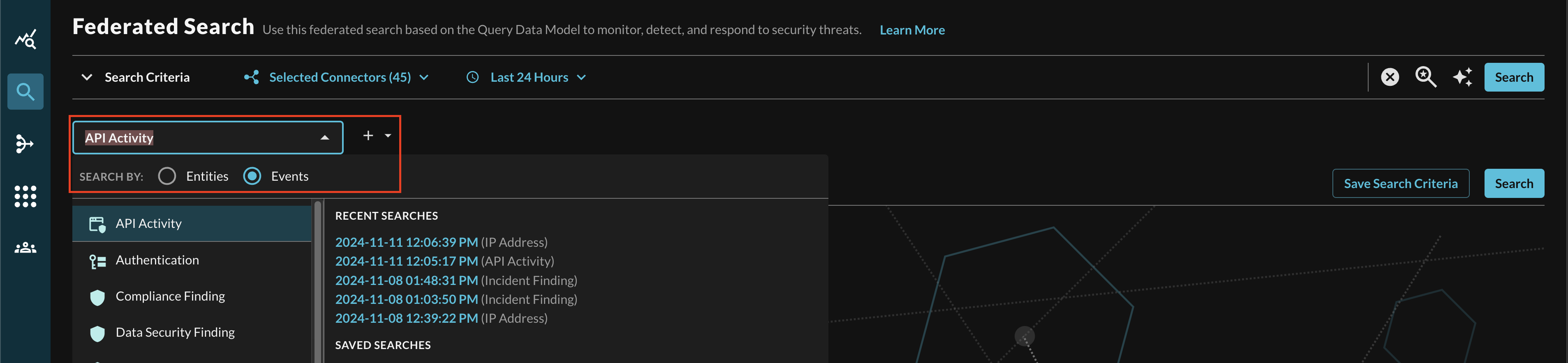
FIG. 11 - Searching for API Activity events with Query Federated Search
Searching from the Event will pull a sample (up to 1000) of all matching events per Connectors that are mapped to it. For more specific filtering within an Event, you can choose one or more conditions to refine a search. Selecting the plus-sign (+) dropdown next to the Event menu allows you to choose from any specific OCSF/QDM attribute in the event.
For instance, when searching for API Activity events, you can specify a specific Username by filtering for Actor --> User --> Name (which is mapped in Configure Schema as actor.user.name) as shown below (FIG. 12).
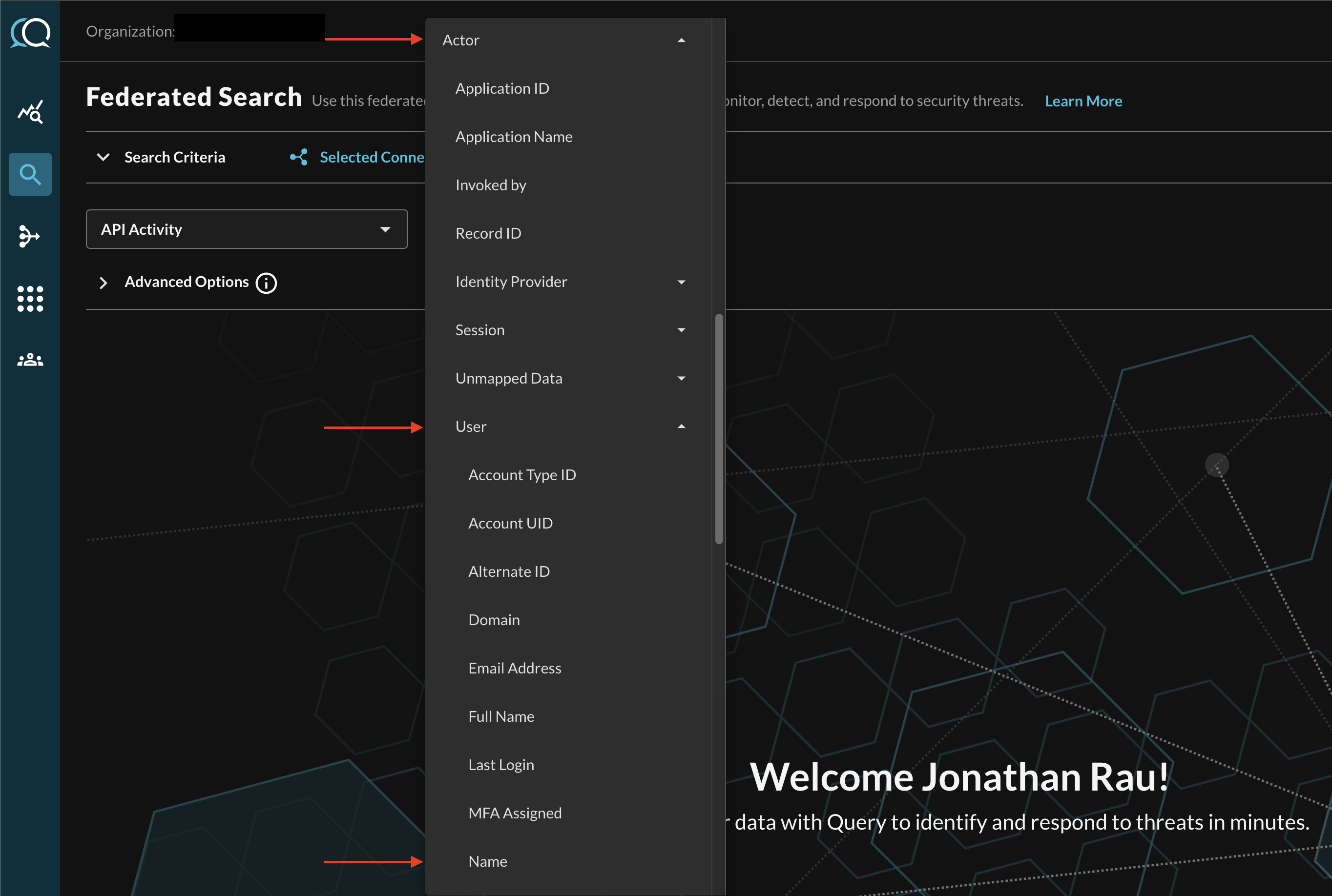
FIG. 12 - Filtering for specific Attributes within an Event Class
When adding two or more Conditions, you can further change the behavior by specifying ANY or ALL quantifiers over the filters for greater levels of specificity or more narrow-but-generalized searches, respectively, as shown below (FIG. 13).
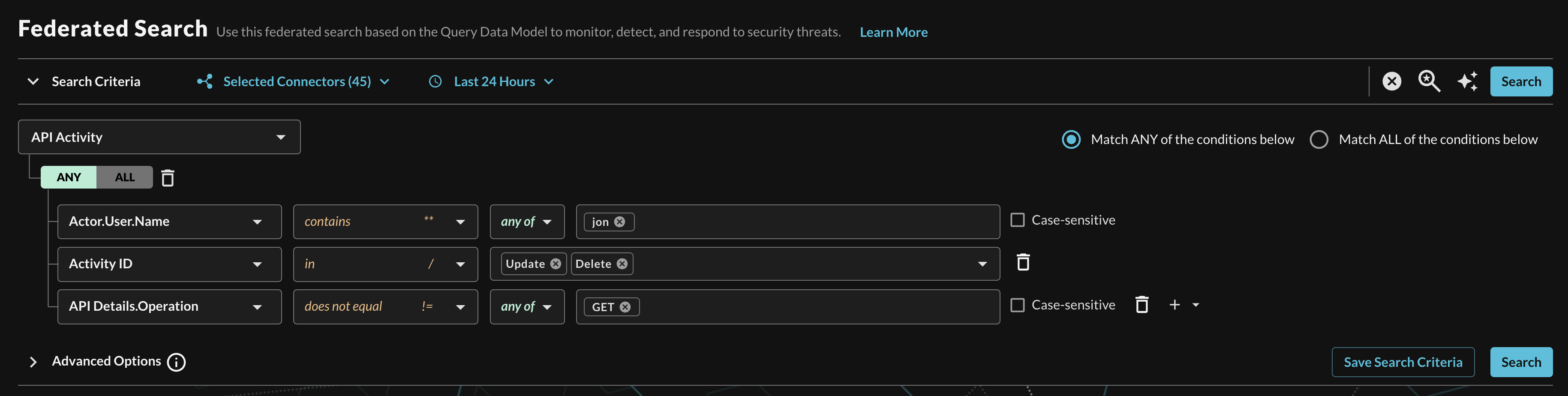
FIG. 13 - Selecting multiple conditional filters
Resources
Troubleshooting Tips
- Ensure that the Project Number or Project ID that you have configured is the same Project where your Google SecOps Tenant is located.
- Ensure that you copied the correct Customer ID or Instance ID.
- Ensure that your Service Account is in the correct Project, is not deleted, and has the proper roles to access the Chronicle API.
- Ensure that the name of your Feed is correct.
If you have exhausted the above Troubleshooting list, please contact your designated Query Sales Engineer or Customer Success Manager. If you are using a free tenant, please contact Query Customer Success via the Support email in the Help section, or via Intercom within your tenant.
Updated 4 months ago