Tégo
Integrate with the Tégo Security Threat Feed API
TL;DRTo integrate the Tégo Cyber Threat Feed API with Query:
- Retrieve a License Key from your Tégo Account Representative.
- Add a connection source in Query using your License Key.
- Use Query Search to surface cyber threat intelligence, geolocation, and reputation information about Hostnames, Domains, IP Addresses and File Hashes.
Overview
Tégo Cyber is a threat intelligence and threat hunting automation platform that provides integrations into Splunk ES, Databricks, and Amazon Security Lake and also vends information on Indicators of Compromise (IOCs) via their Threat Feed API.
Query integrates with the Tégo Threat Feed API and normalizes analyst comments, reputation information, geolocation and ASN information, and other pertinent details for certain entities such as IP Addresses, Hostnames, Domains, and file Hashes (e.g., SHA-1, SHA-256, MD5, etc.) in the Query Federated Search platform.
Prerequisites
You must retrieve a License Key from your Tégo account representatives to configure this Connector within the Query platform.
Use the following steps to create a new Query Federated Search Connector for Tégo.
-
Navigate to the Connections page, select Add Connections, and selectTégo from the Threat Intelligence & Enrichment category as shown below you can speed this up by typing
Tegointo the search bar.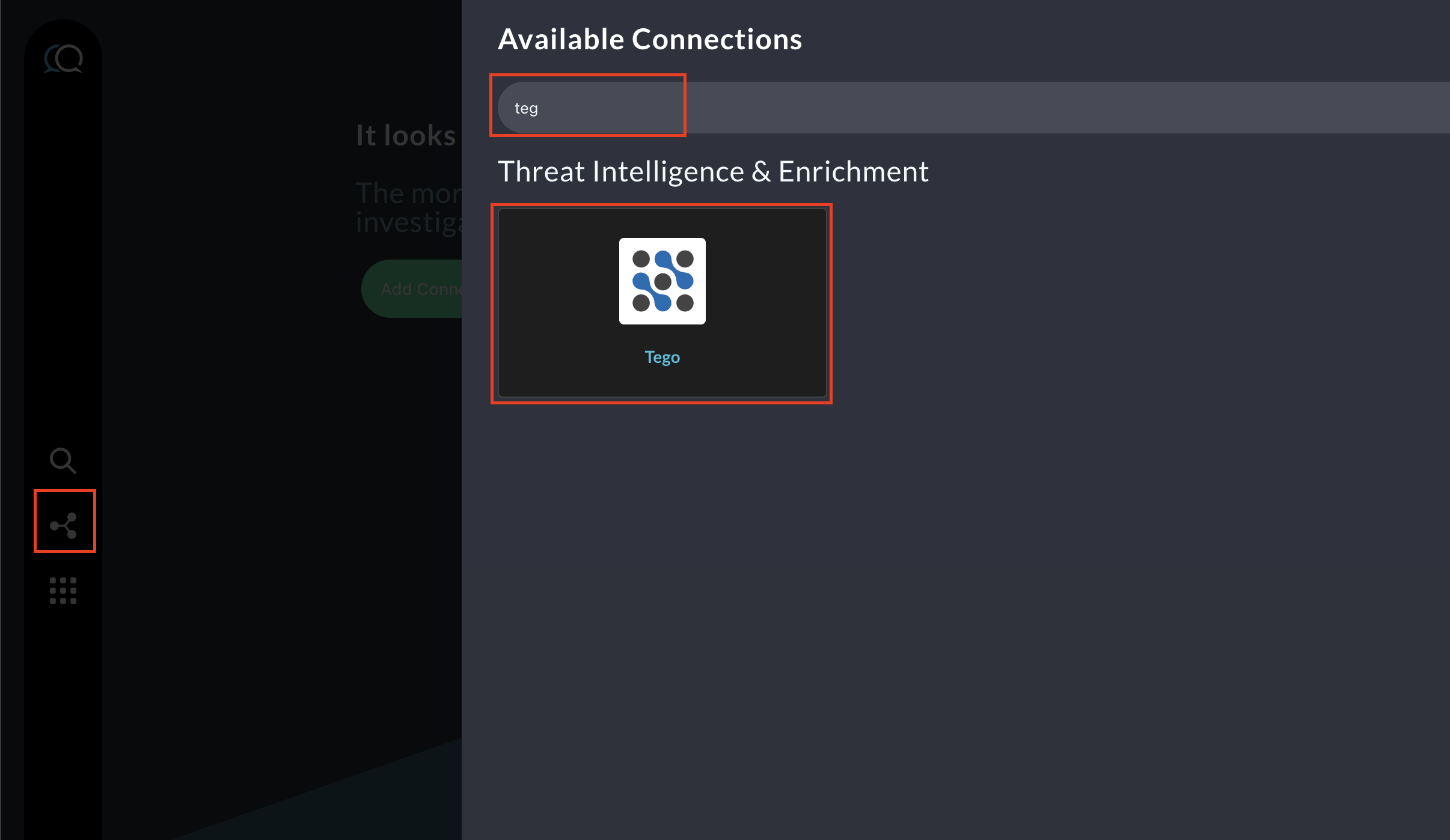
-
In the Configure Connector tab, add the following detail:
- Name: The human-readable name you want to give to this connector, you can name it whatever you want, but you can use this to delineate across different License Keys.
- Default Login: Leave this the default Value (e.g.,
Default Login) - Tego License: Enter you License Key here, this value is handled like a secret and is securely vaulted in the Query Federated Search Platform's Privileged Identity Management (PIM) vault in our backend.
-
Select Test Connection from the bottom-right of the connection pane to ensure that your License Key is valid and you can pull information from the Threat Feed API.
-
Finally, select Save to store and activate the Connector.
You will now see Tégo added as an available Platform within the Query Search and Query Summary Insights UI, the "platform" term is synonymous with Connector.
Querying the Tégo Threat Feed API Connector
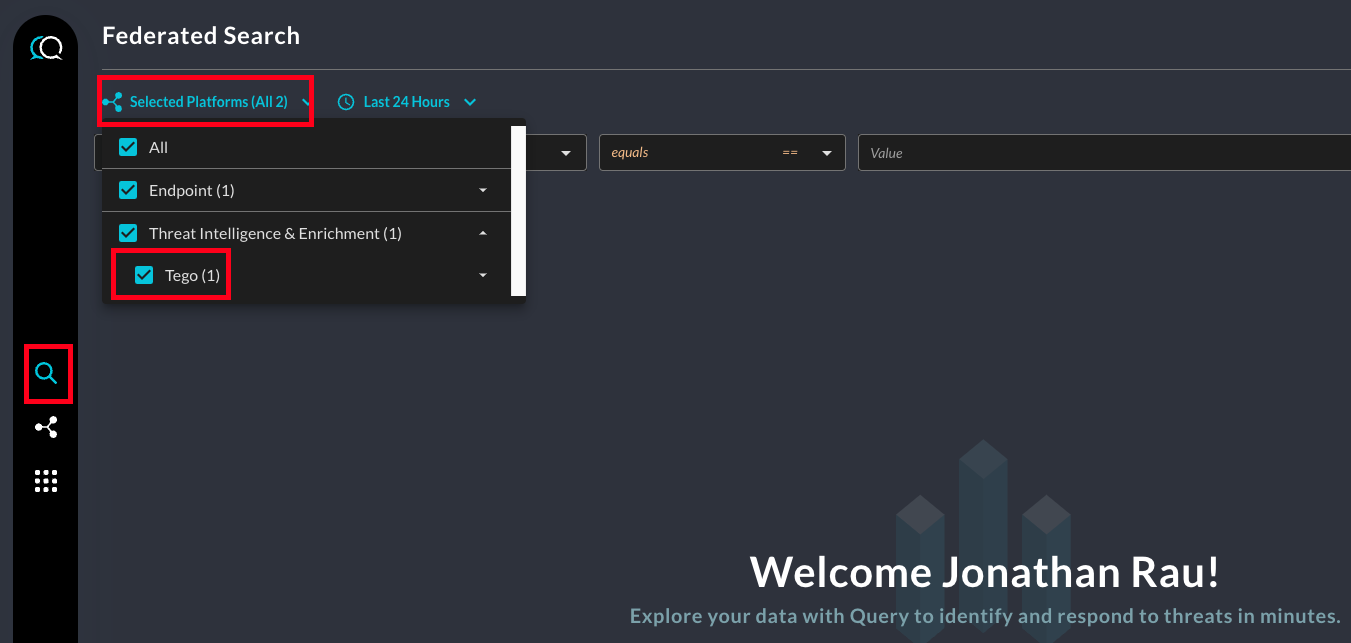
Within the Query Search UI, all Platforms (A.K.A Connectors) are enabled by default, to check that Tégo is enabled, navigate to the Threat Intelligence & Enrichment section of the Platforms dropdown and ensure that Tégo is selected (denoted by a checkbox) before running your searches as shown below.
As of 1 NOV 2023, the following Entities, Events and Objects are supported by Query for Tégo. For more information about this terminology, refer to the Normalization and the Query Data Model (QDM) section of the docs or check out our QDM Schema website. If results are not returned it means that Tégo currently does not have any entries in their backend for the specific IOC or entity of interest.
Entities
- Hostname (NOTE: This entity currently maps to Domain Names for searching from Tégo)
- Domain Name (e.g.,
amazon.com) - IP Address (Public IPv4, e.g.
205.251.242.103) - File Hash (MD5, SHA1, SHA256, e.g.
f4dd44bc19c19056794d29151a5b1bb76afd502388622e24c863a8494af147dd)
Objects
- Domain Intelligence
- IP Intelligence
- Threat Intelligence (for Hashes)
- Reputation
- Location
Resources
For more information on the Tégo Cyber Threat Feed API, see here.
Updated 4 months ago