CrowdStrike Falcon NextGen SIEM
Integrate Query with any CrowdStrike Falcon NextGen SIEM (formerly known as Falcon LogScale and Humio) Repository
TL;DRTo integrate CrowdStrike Falcon NextGen SIEM with Query:
- Create an API Token with
Data read accesspermissions.- Identify your instance URL and any Repositories you wish you to onboard.
- Map the data in your Repositories into the Query Data Model using the Configure Schema workflow
- Use Query Search to parallelize searches and surface details about any data stored in LogScale for incident response (IR), threat hunting, investigations, and other security and observability use cases.
Overview
CrowdStrike Falcon NextGen SIEM - also known as LogScale Cloud, and formerly Humio - is a CrowdStrike-managed log storage platform that handles the end-to-end tasks of ingesting, storing, querying, and visualizing log data. The various ingested data sources are organized into one or more Repositories which can either be built using a specific schema from a specific source or can co-mingle multiple different schemas and datasources. LogScale makes it easy to organize EDR telemetry from CrowdStrike Falcon and Falcon Data Replicator (FDR), as well as several other log sources, either manually via the various Ingest mechanisms or using third-party tools such as Cribl Stream.
Query's entire data model is built around the Open Cybersecurity Schema Framework (OCSF) - named the Query Data Model (QDM) - which expresses all search intents with OCSF/QDM concepts such as Entities/Observables used to represent facts and indicators whereas Event Classes represent things that have happened and are normalized against network, application, file system, identity, and 1st party security findings.
Query integrates with CrowdStrike Falcon NextGen SIEM by providing a full-featured 1:1 query translation, query planning, and parallelized query execution engine on top of the native LogScale Search APIs. After providing the instance URL, API Token, and Repository you can model nearly any data point within your Repositories against the OCSF/QDM schema. Query will handle translation into the Falcon Query Language (FQL) - formerly known as Liquid Query Language (LQL) - based on your search intent, handle the entire query lifecycle, and return results to you in a normalized and standardized schema. The benefits are:
- Cheaper and faster searches by not utilizing cross-Repo searches, and searching only the Repos you require to be searched for the details you want.
- Your analysts no longer need to become experts in FQL and can instead focus on triage, escalations, and remediation.
- Only the data required for analysis, investigations, incident response, or otherwise is retrieved.
Some details on searchesCurrently (as of 27 FEB 2025) Query Federated Search does not support array operators or mapping data stored in arrays. However, depending on your Ingestion rules, Arrays may be flattened automatically.
Prerequisites
To connect a CrowdStrike Falcon NextGen SIEM Repository with Query Federated Search you'll need to
-
Create a Repository API Token with
Data read accesspermissions as detailed in the LogScale documentation as shown below (FIG. 1). Consider creating the API Token with the GraphQL API to provide access to multiple different Repositories if you have a large quantity of them to simplify connectivity.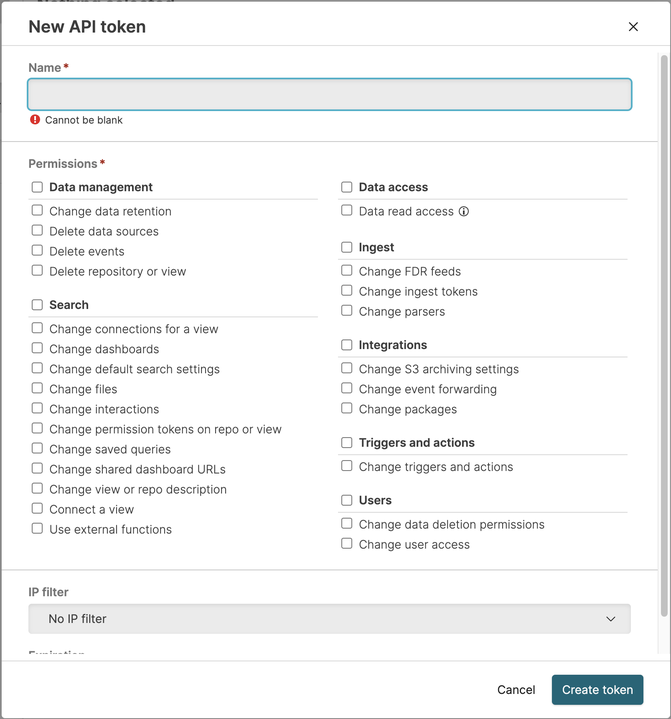
FIG. 1 - Creating an API Token for LogScale in the UI
-
Retrieve the URL of your LogScale tenant, such as
https://{company_name}.logscale.us-1.crowdstrike.com. Do not include/api/v1/or any other path at the end. -
Retrieve one or more Repository names from the Repositories and views tab of the LogScale UI, such as shown below (FIG. 2).
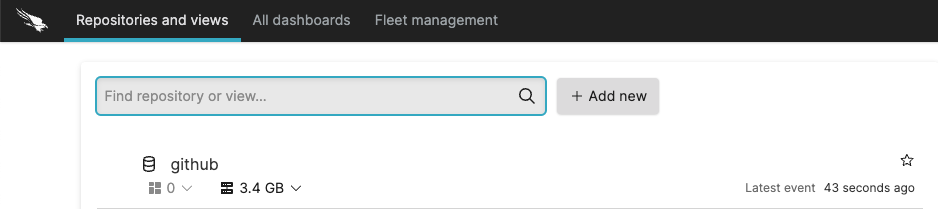
FIG. 2 - Retrieve a Repository name from the LogScale UI
To learn how to configure a CrowdStrike Falcon LogScale Connector, proceed to the next section.
On NHI securityNHI - or, Non-Human Identities - such as your Repository API Tokens are extremely sensitive. Query securely stores the Client Secret in a dedicated AWS Secrets Manager Secret per Connector per Tenant. For added security, contact your Customer Success Manager or sales team to get the IP address ranges for the Query Federated Search platform to add as an additional IP filter.
While this requires you to configure Connectors per Repository and continue to enter in your credentials, every copy is stored as securely as each other with minimum necessary permissions that only allows the specific piece of serverless infrastructure to retrieve the secret, it is never cached or persisted outside of the Secret.
Setting up the CrowdStrike Falcon LogScale Connector
Use the following steps to create a new Query Federated Search Connector for CrowdStrike Falcon LogScale.
-
Navigate to the Connectors page, select Add Connector, and selectCrowdStrike Falcon LogScale from the
SIEM and Log Managementcategory as shown below (FIG. 3). You can also search for CrowdStrike Falcon LogScale using the search bar in the Add Connector page.
FIG. 3 - Locating the CrowdStrike Falcon LogScale Connector
-
In the Configure Connector tab, add the following detail as shown below (FIG. 4):
-
Connector Alias Name: The human-readable name you want to give to this connector, you can provide the name pertaining to your Repository, or in the case that your Repository has multiple data points you can identify the Repository and specific mappings or other useful information for analysts and end-users.
-
Default Login: Leave the default value:
Default Login. -
Falcon LogScale Instance URL: The URL of your LogScale instance, copied in Step 2 of the Prerequisites section.
-
Repository Name: The name of the Repository you wish to model data for and search, copied in Step 3 of the Prerequisites section.
-
API Token: The API token with permissions to search your Repository, copied in Step 1 of the Prerequisites section.
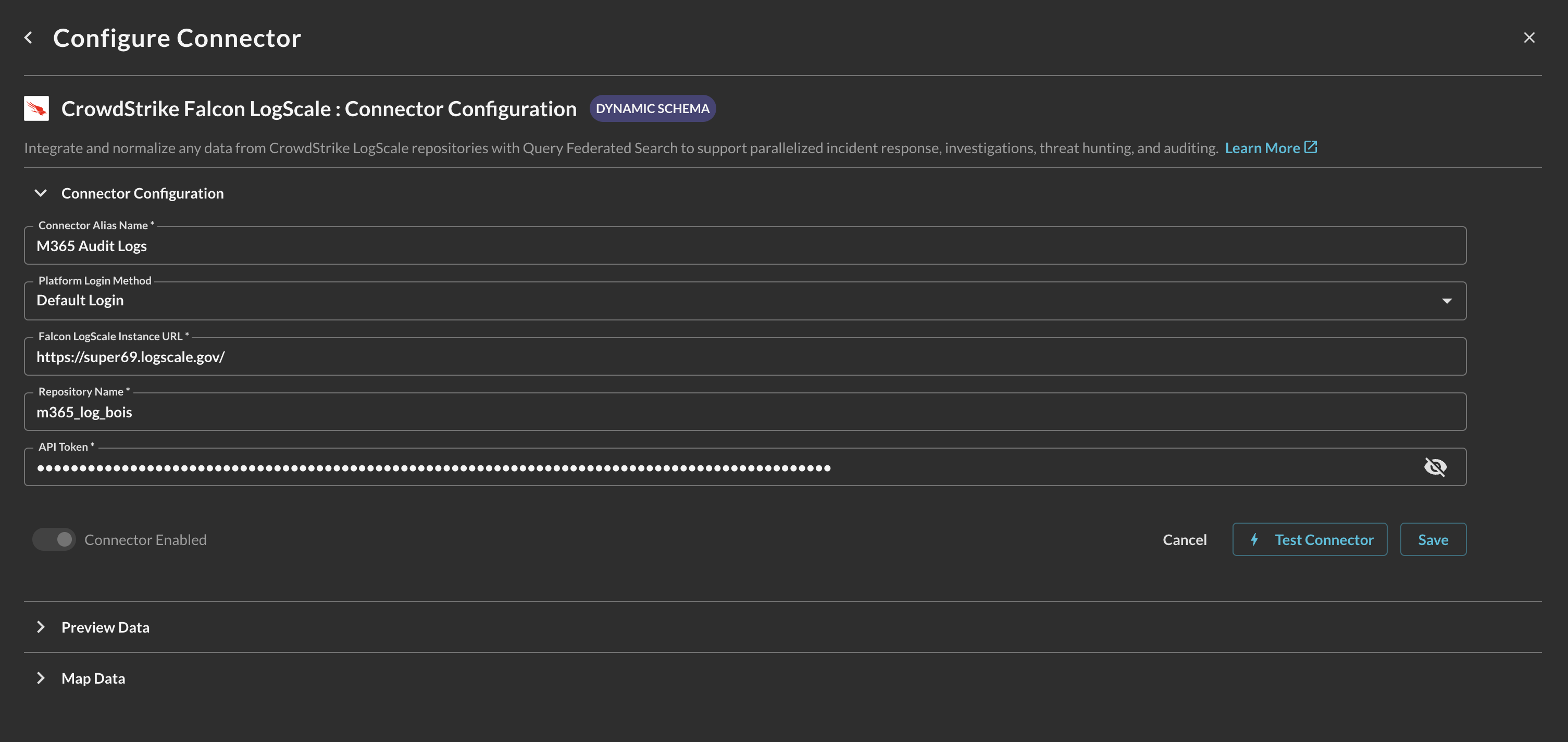
FIG. 4 - Entering the parameters for the CrowdStrike Falcon LogScale Connector
-
-
Select Save to save and activate the Connector.
-
Select Test Connection from the bottom-right of the connection pane to ensure that your URL and Repository name are correct, and that your API Token and permissions are valid, and that at least 1 result can be returned from your Repository in the last 7 days.
-
Finally, proceed to the Preview Data section to begin the Configure Schema process. Refer to the hyperlink to learn how to use the Configure Schema no-code workflow, it is HIGHLY recommended for first time users.
You will now see CrowdStrike Falcon LogScale added as an available Connector within the Query Search and Query Summary Insights UI.
Querying CrowdStrike Falcon LogScale Connectors
Within the Query Search UI, all Connectors are enabled by default. To check that your specified Connector(s) for CrowdStrike Falcon LogScale are enabled, navigate to the SIEM and Log Management section of the Selected Connectors dropdown and ensure that your specified CrowdStrike Falcon LogScale Connector(s) are are selected (denoted by a checkbox) before running your searches as shown below (FIG. 5).
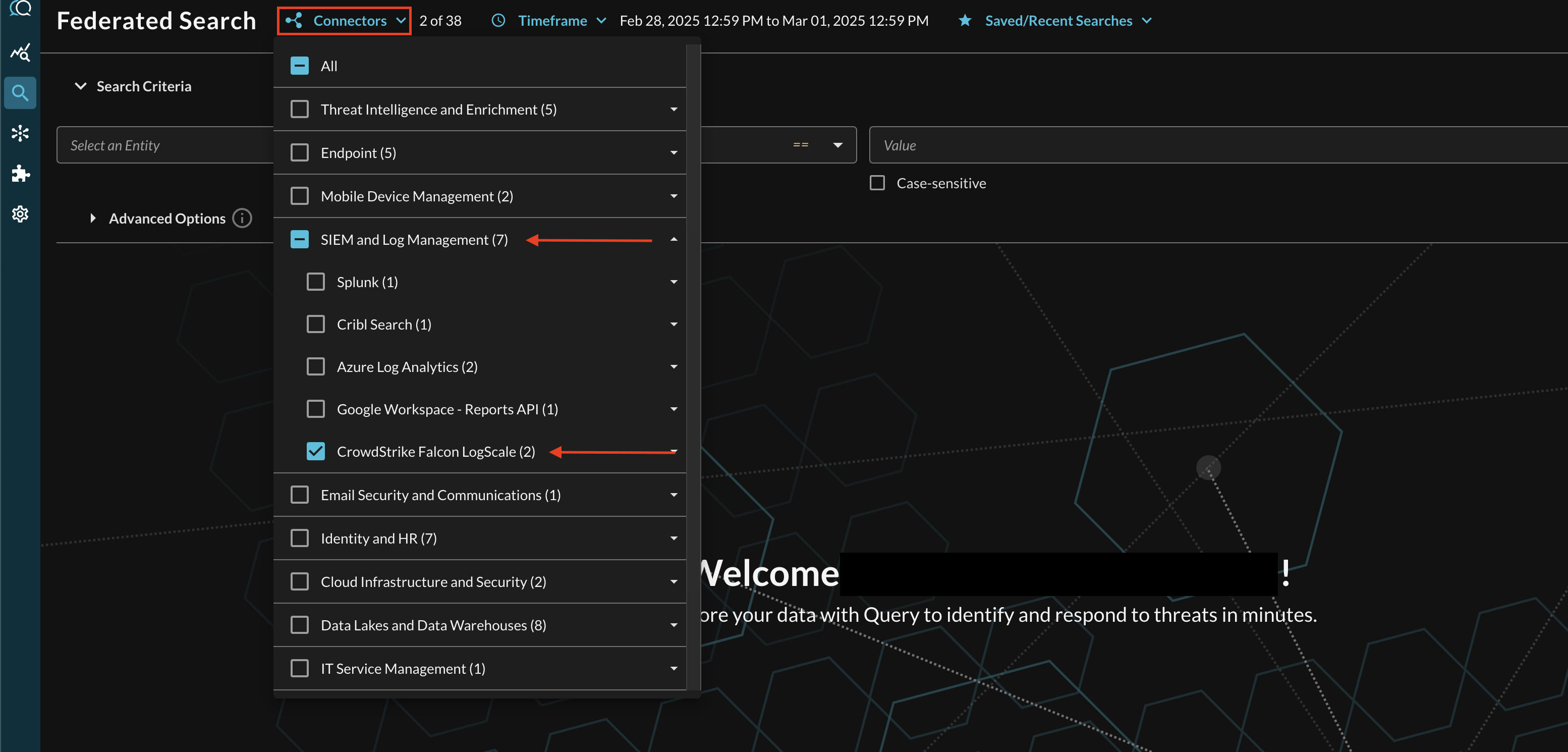
FIG. 5 - Selecting CrowdStrike Falcon LogScale Connector(s)
The Entities (Observables) and Events you will be able to search determine on how you mapped your data in Configure Schema against a given CrowdStrike Falcon LogScale Repository. For more information about the QDM/OCSF schema itself refer to the About the Query Data Model section of the Query docs, you can also view the Categories, Events, and Objects themselves.
Entity-based Search
To conduct an Entity-based search, ensure that all of the data points you will be searching for are mapped within the Configure Schema wizard as demonstrated in the previous section.
In the Federated Search console, select the search dropdown, ensure the Entities radio button is selected and search for your desired Entity as shown below (FIG. 6). For instance, you can search for stuffstuffstuff, these can be further correlated against other different Query Connectors.
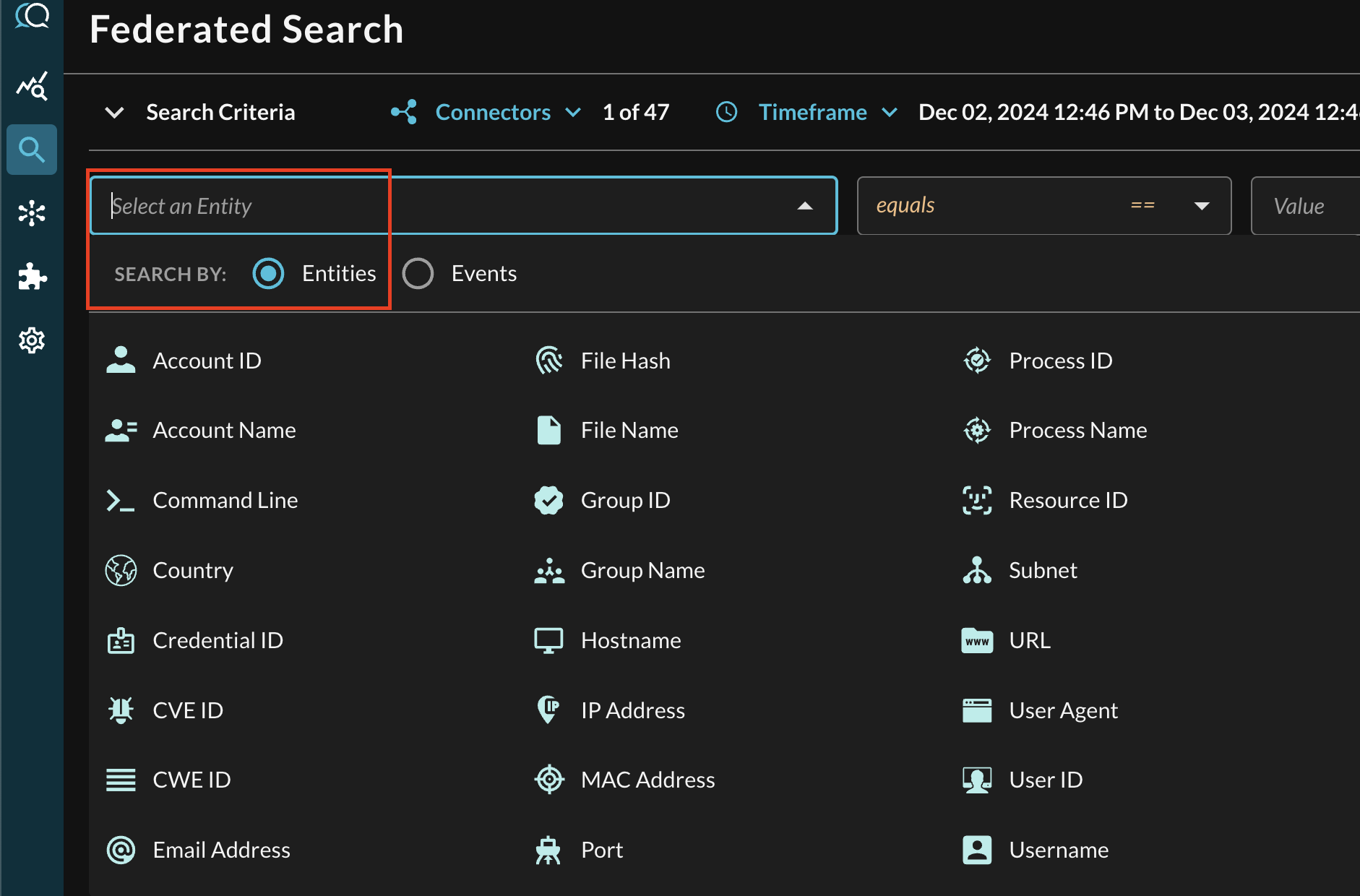
FIG. 6 - Entity-based searching with Query Federated Search
After selecting an Entity, most allow you to specify an Operator. This allows you to perform simple equality searches or to perform more generalized searches using Contains, Starts With, or Ends With Operators. These are mapped against appropriate CONNECTOR operators.
When you search for multiple values that may be present across different Connectors, the Query Federated Search query planner inspects the Configure Schema metadata to ensure searches are sent to the appropriate Connectors, this operates more as a collated window function within Query and not as an expensive SQL join.
Additionally, you can specify case-sensitivity for the entire search criteria. An example of a multi-value CVE search that uses the equals operator and toggled case-sensitivity is shown below (FIG. 7).
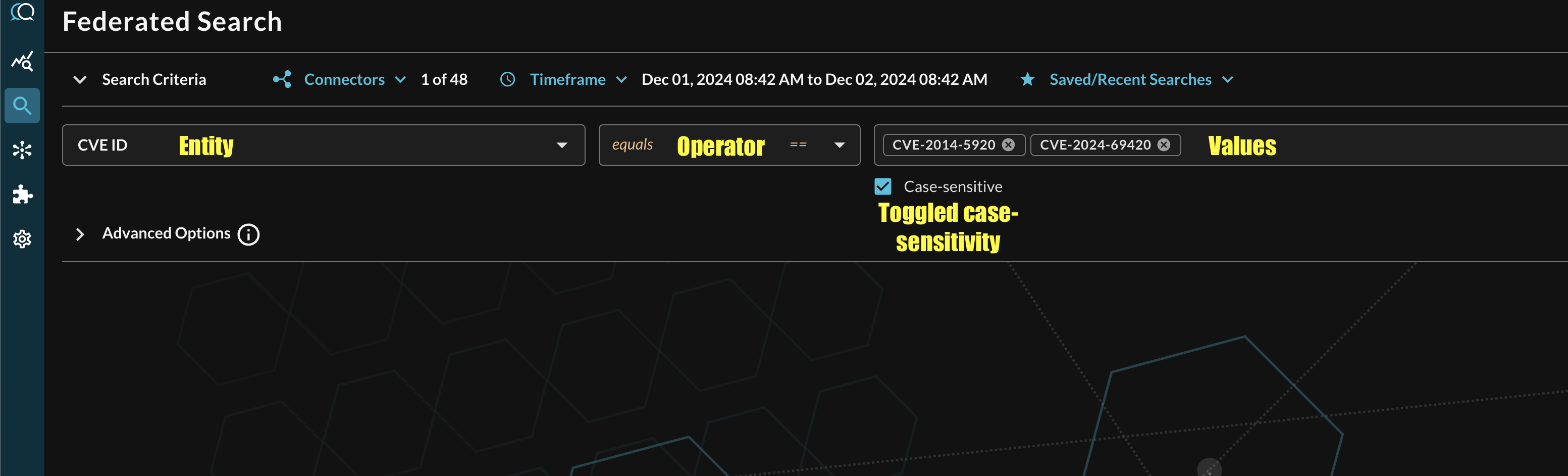
FIG. 7 - Orientation for Entity-based search in Query Federated Search
Event-based Search
To conduct an Event-based search, ensure that all of the data points you will be searching for are mapped within the Configure Schema wizard as demonstrated in the mapping section. Within the Federated Search console, only mapped Events per the Select Connectors are populated, unlike Entities which has every potential value shown in the list.
In the Federated Search console, select the search dropdown, ensure the Events radio button is selected and search for your desired Event as shown below (FIG. 8). For instance, you can search for all API Activity events which can be normalized from a ClickHouse dataset that contains audit log information, in addition you can also search across all Connectors normalized to API Activity such as AWS CloudTrail Management Events stored in AWS Security Lake, System Event logs in Okta, and Audit Events in Microsoft Intune.
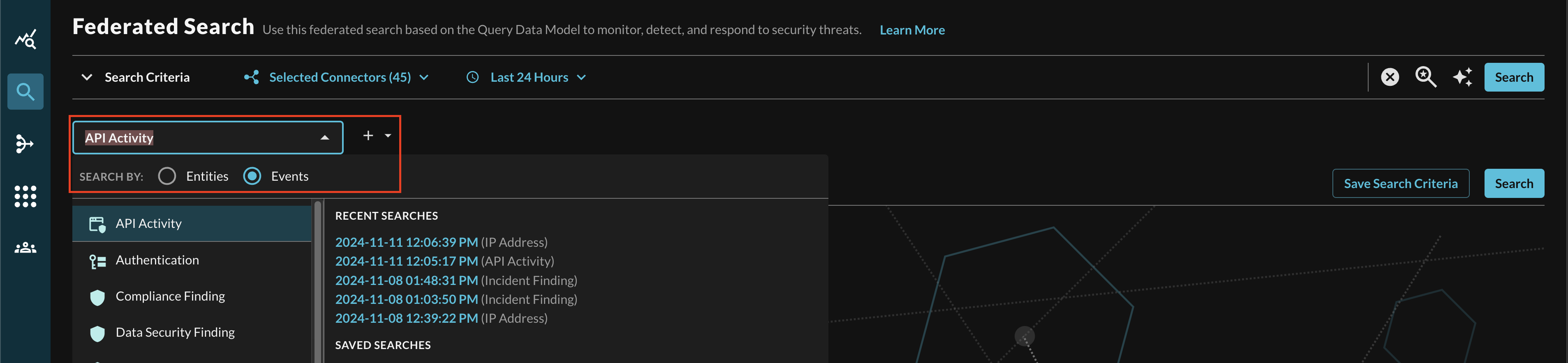
FIG. 8 - Searching for API Activity events with Query Federated Search
Searching from the Event will pull a sample (up to 1000) of all matching events per Connectors that are mapped to it. For more specific filtering within an Event, you can choose one or more conditions to refine a search. Selecting the plus-sign (+) dropdown next to the Event menu allows you to choose from any specific OCSF/QDM attribute in the event.
For instance, when searching for API Activity events, you can specify a specific Username by filtering for Actor --> User --> Name (which is mapped in Configure Schema as actor.user.name) as shown below (FIG. 9). In this case, the actor Object contains information about the process and user who is acting on something, such as a user authenticating to a service or an admin user making a change to a setting or configuration.
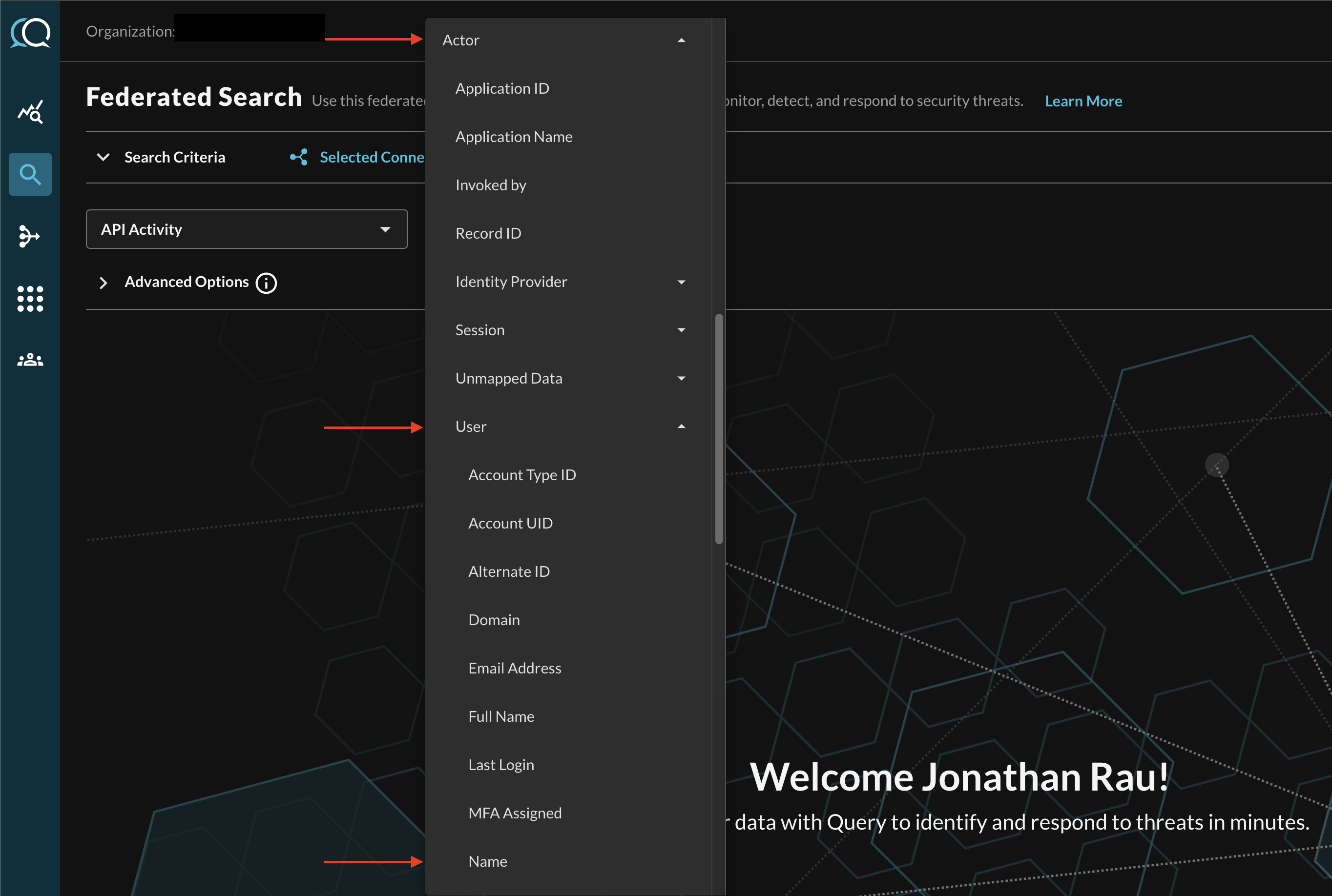
FIG. 9 - Filtering for specific Attributes within an Event Class Search
When adding two or more Conditions, you can further change the behavior by specifying ANY or ALL quantifiers over the filters for greater levels of specificity or more narrow-but-generalized searches, respectively, as shown below (FIG. 10).
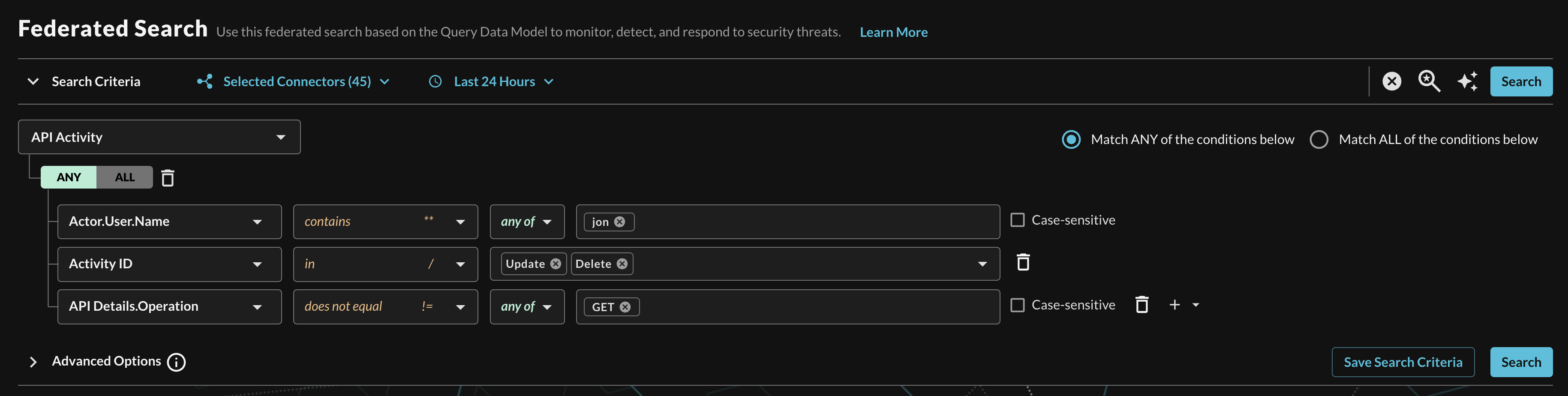
FIG. 10 - Selecting multiple conditional filters
Resources
Troubleshooting Steps
- Ensure that you have provided the correct URL, including the
https://but you did not include any trailing path such asapi/v1/at the end. - Ensure that your Repository name is created and there is data flowing into it within the last 7 days.
- Ensure that your API Token is valid and was created against your specific Repository. If you created the API Token with the GraphQL API, ensure that your Repository was added in scope.
- If you configured an IP Filter, double-check that the IP addresses are valid and match with what the Query CSM team provided.
- Ensure that the data is not only stored in a large array and that your Ingest rules flatten arrays. Query cannot support unnesting Arrays on your behalf.
If you have exhausted the above Troubleshooting list, please contact your designated Query Sales Engineer or Customer Success Manager. If you are using a free tenant, please contact Query Customer Success via the Support email in the Help section, or via Intercom within your tenant.
Updated 4 months ago