Lacework (FortiCNAPP)
Integrate Query with Lacework (Fortinent FortiCNAPP) to surface details on hosts, vulnerabilities, alerts, and query audit, file, and user log information.
TL;DRTo integrate the Lacework (FortiCNAPP) Federated Search Connector with Query:
- Create an API Key and provide READ-only access to specific scopes.
- Configure a Lacework (FortiCNAPP) Connector in the Query console.
- Use Query to parallelize searches and surface details about cloud alerts, misconfigured resources, identities, and vulnerabilities for incident response (IR), threat hunting, investigations, and other security and observability use cases.
Overview
Lacework FortiCNAPP - formerly just known as Lacework - is a Cloud Native Application Protection Platform (CNAPP) born from the acquisition of Lacework by Fortinet in October 2024. Lacework was one of many Cloud Security Posture Management (CSPM) tools that expanded their capabilities into AppSec, Vulnerability Management, and IAM capabilities to expand into the CNAPP category. Lacework provides advanced cloud security capabilities and threat detection across major Cloud Service Providers (CSPs) and also offers the capability to query more data from covered hosts such as file data.
All federated searches have their searches and results expressed in the terms of the Query Data Model (QDM), which is based on the Open Cybersecurity Schema Framework (OCSF). Each API source is normalized into a specific QDM/OCSF Event Class to standardize and normalize the data for increased situational awareness, ease of aggregation of filtering, and easy pivoting.
API Name | QDM/OCSF Event Class | Entities/Observables |
|---|---|---|
Account Name Username | ||
Audit Logs (only Login events) | Account Name | |
CVE ID Hostname IP Address Resource UID | ||
Hostname IP Address Resource UID | ||
Group Name Resource UID Username User ID | ||
File Name File Hash Resource UID | ||
N/A - uses event-based search only |
Query integrates with Lacework (FortiCNAPP) by providing parallelizeable federated search and analytics capabilities directly to Lacework APIs without duplicating or otherwise durable storing data. Query handles translation of search intent into proper LQL or parameter-based queries routed to the proper APIs to fulfill your search all at once. Query also provides in-situ transformation of all data into the OCSF/QDM format to normalize all data points in similar ways to each other and across Connectors in Query Federated Search.
For instance, when using the Resource UID Entity that maps to the mid which can retrieve details on user, file, alert, and vulnerability data all at the same time. You can further correlate and collate this data with similar search predicates such as using the Hostname Entity to also search across DNS, HTTP, and DHCP log data stored in Snowflake or Amazon S3 (via Athena) or look across other security and IT observability tools to provide your analysts a single view of all related evidence to an asset or entity.
Some details on searchesQuery will attempt to reuse the access token generated from your API creds as to not overly consumed your Requests in a rolling hourly period, if you blow out your API quota, Query will return an HTTP 429.
Query implements virtualized filters on certain data points that do not support a direct LQL or API filter operation, this may lead to slightly longer search terms as we must overfetch and further match on your filters.
Query supports streaming of data by returning normalized data back to the application immediately and yielding them even while the rest of the operation is still ongoing. Consider using more specific queries to speed up processing time of the overall search.
Prerequisites
To connect Lacework (FortiCNAPP) with Query Federated Search you'll need to
- Create an API Key using the steps detailed in this document. Consider using a Service User.
- Provide READ scopes to via the
Account power userService User group or provide READ-only access to the following scopes- Alerts
- Vulnerabilities
- Identities
- General
- Audit Logs
To learn how to configure a Lacework (FortiCNAPP) Connector, proceed to the next section.
On NHI securityNHI - or, Non-Human Identities - such as your Lacework (FortiCNAPP) API keys are extremely sensitive. Query securely stores the Client Secret in a dedicated AWS Secrets Manager Secret per Connector per Tenant.
While this requires you to configure Connectors per Lacework (FortiCNAPP) tenant and continue to enter in your credentials, every copy is stored as securely as each other with minimum necessary permissions that only allows the specific piece of serverless infrastructure to retrieve the secret, it is never cached or persisted outside of the Secret.
Setting up the Lacework (FortiCNAPP) Connector
Use the following steps to create a new Query Federated Search Connector for Lacework (FortiCNAPP).
-
Navigate to the Connectors page, select Add Connector, and selectLacework (FortiCNAPP) from the
Cloud Infrastructure and Securitycategory as shown below (FIG. 1). You can also search for Lacework (FortiCNAPP) using the search bar in the Add Connector page.
FIG. 1 - Locating the Lacework (FortiCNAPP) Integration
-
In the Configure Connector tab, add the following detail as shown below (FIG. 2):
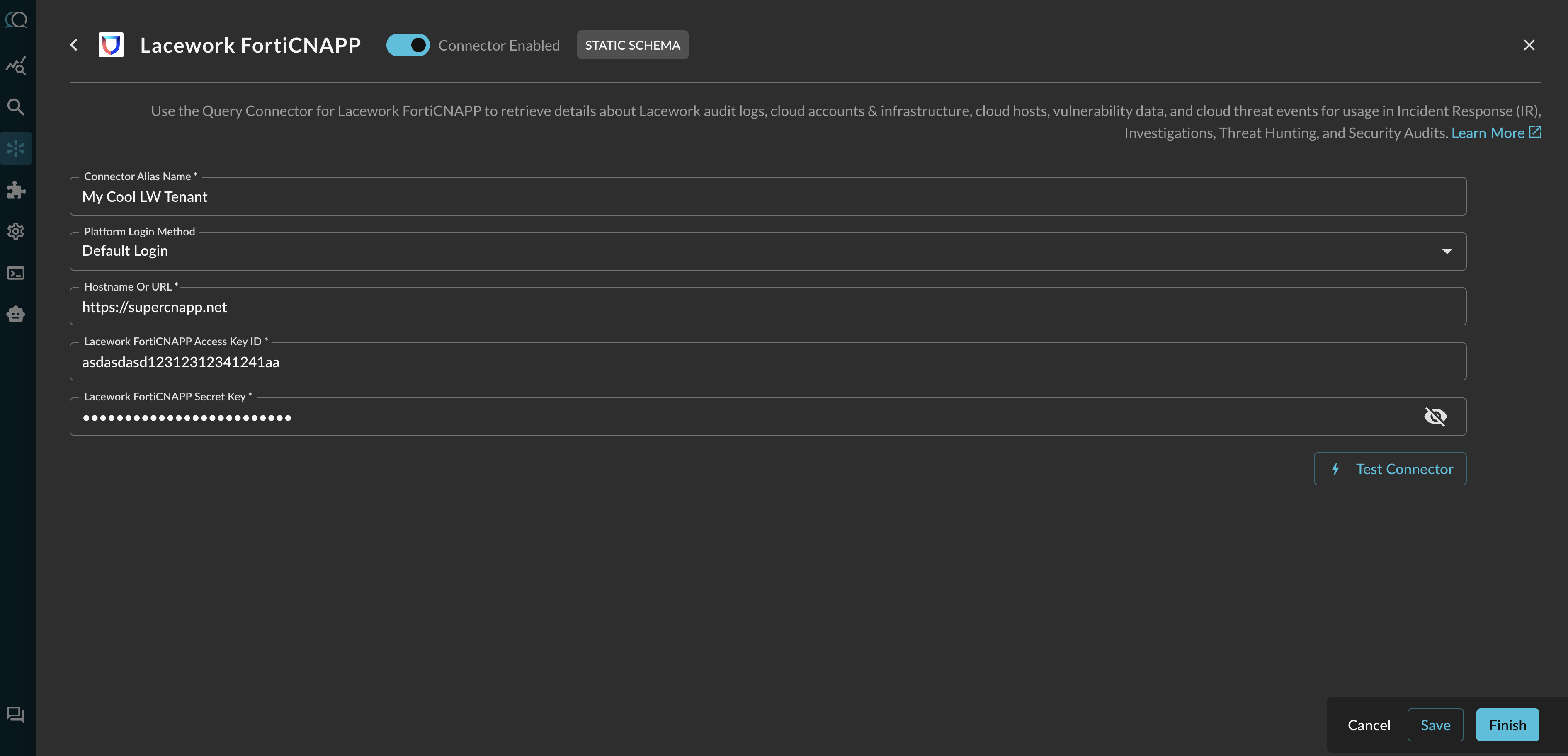
FIG. 2 - Configuring Lacework (FortiCNAPP) Connector parameters
- Connector Alias Name: The human-readable name you want to give to this connector, such as the names of the your tenants if you have multiple on behalf of a MSSP or PE portfolio.
- Default Login: Leave the default value:
Default Login. - Hostname or URL: The hostname or URL of your Lacework tenant.
- Lacework FortiCNAPP Access Key ID: Your API Token access key ID.
- Lacework FortiCNAPP Secret Key: Your API Token secret key value.
-
Select Save to save and activate the Connector.
-
Select Test Connection from the bottom-right of the connection pane to ensure that you have the proper scopes to all APIs as well as licenses to the integrations and that your API client and URL/hostname are valid.
You will now see Lacework (FortiCNAPP) added as an available Connector within the Query Search and Query Summary Insights UI.
Querying Lacework (FortiCNAPP) Connectors
Within the Query Search UI, all Connectors are enabled by default. To check that your specified Connector(s) for Lacework (FortiCNAPP) are enabled, navigate to the Cloud Infrastructure and Security section of the Selected Connectors dropdown and ensure that your specified Lacework (FortiCNAPP) Connector(s) are are selected (denoted by a checkbox) before running your searches as shown below (FIG. 3).
Resources
Troubleshooting Steps
- Ensure that you provided the correct URL or Hostname.
- Ensure that your API Token is valid, and that you provided the correct Access Key ID and Secret to the correct parameter in the configuration parameters.
- Ensure that you are properly licensed for all features, the Connector will still function but may return a greater amount of errors.
If you have exhausted the above Troubleshooting list, please contact your designated Query Sales Engineer or Customer Success Manager. If you are using a free tenant, please contact Query Customer Success via the Support email in the Help section, or via Intercom within your tenant.
Updated 4 months ago