Query Splunk App
Query empowers Splunk users with more data from outside of Splunk
TL;DR About the Query Splunk AppThe Query Federated Search for Splunk app expands the data reach of Splunk so users can search a wide range of distributed data sources that have not been ingested into Splunk.
Splunk users can search directly from Splunk's dashboard or Search box using the
queryaicommand, and the results will include data from all repositories connected to Query with a Platform Connector. Leveraging Query Federated Search, you can also investigate events and entities and/or run federated detections.The Query Splunk app is installed by a Splunk Administrator, in coordination with a Query Platform administrator.
What Is Query Federated Search for Splunk?
Your organization likely uses the industry-leading Splunk platform for observing security data. And you almost certainly have lots more security-related data that's not in Splunk. With Query, you can overcome that limitation: after a Splunk administrator installs the Query Federated Search app in Splunk, you can search Query-connected remote data even when it does not exist in the Splunk index.
The queryai command brings federated search results right into the Splunk UI, ready to leverage further with the Splunk Search Processing Language ( SPL). You can use your queryai search results in SPL searches, reporting, and dashboards. This powerful capability bypasses any need to index the data in Splunk.
In this way, Query Federated Search for Splunk lets you access, search, and use all of your cybersecurity data directly from the Splunk console or dashboard - no matter the data repository’s vendor, technology, or location.
If you are hungry for even more data, Administrators can connect Query to additional data sources in minutes.
Query Search Results in Splunk
To help you visualize, if you were to run a search from Splunk to fetch everything related to an IP address, your result set would include all associated events, devices, user information, and any other related records contained in your Query platform integrations.
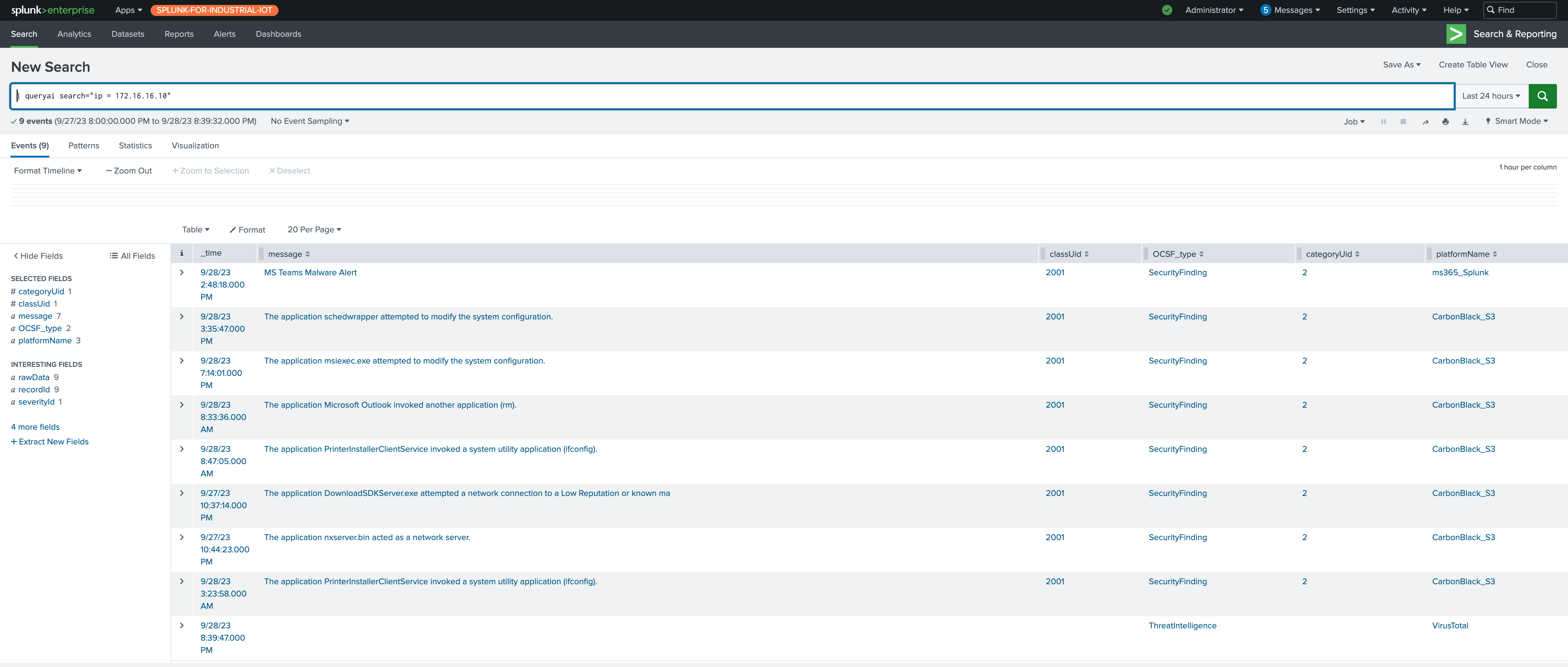
Event and Entity Investigation Views
With the power of Federated Search, you can investigate events and entities without having to centralize data. Use the out-of-box views for investigation or customize to create your own dashboards -- all in Splunk console.
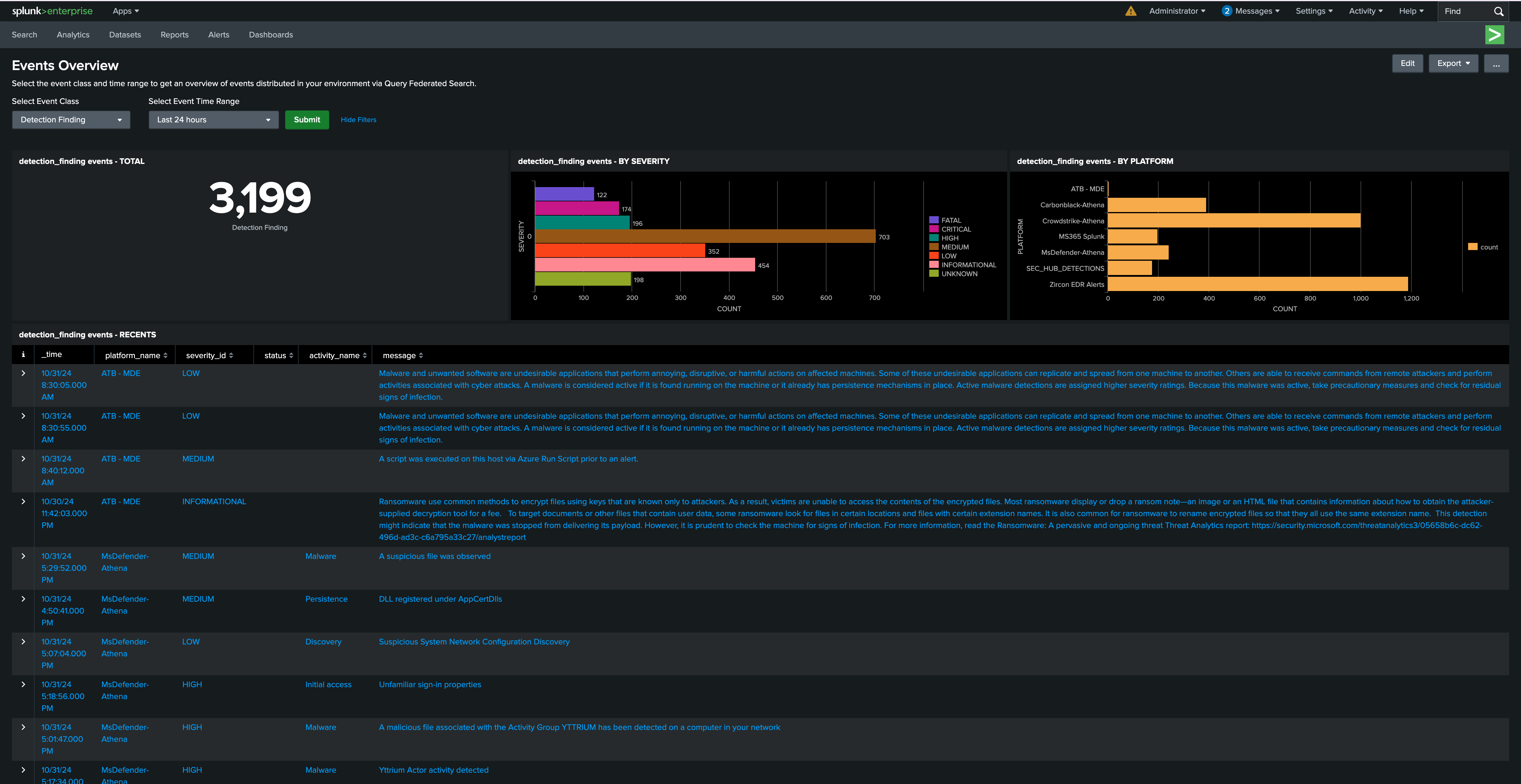
Federated Detections
Federated detections gives the ability to trigger detections without centralization of data in Splunk. You can write your custom detection or adapt detections content from public sources like Splunk's Threat Research, to run detections over your distributed data sources without needing to move or centralize data.
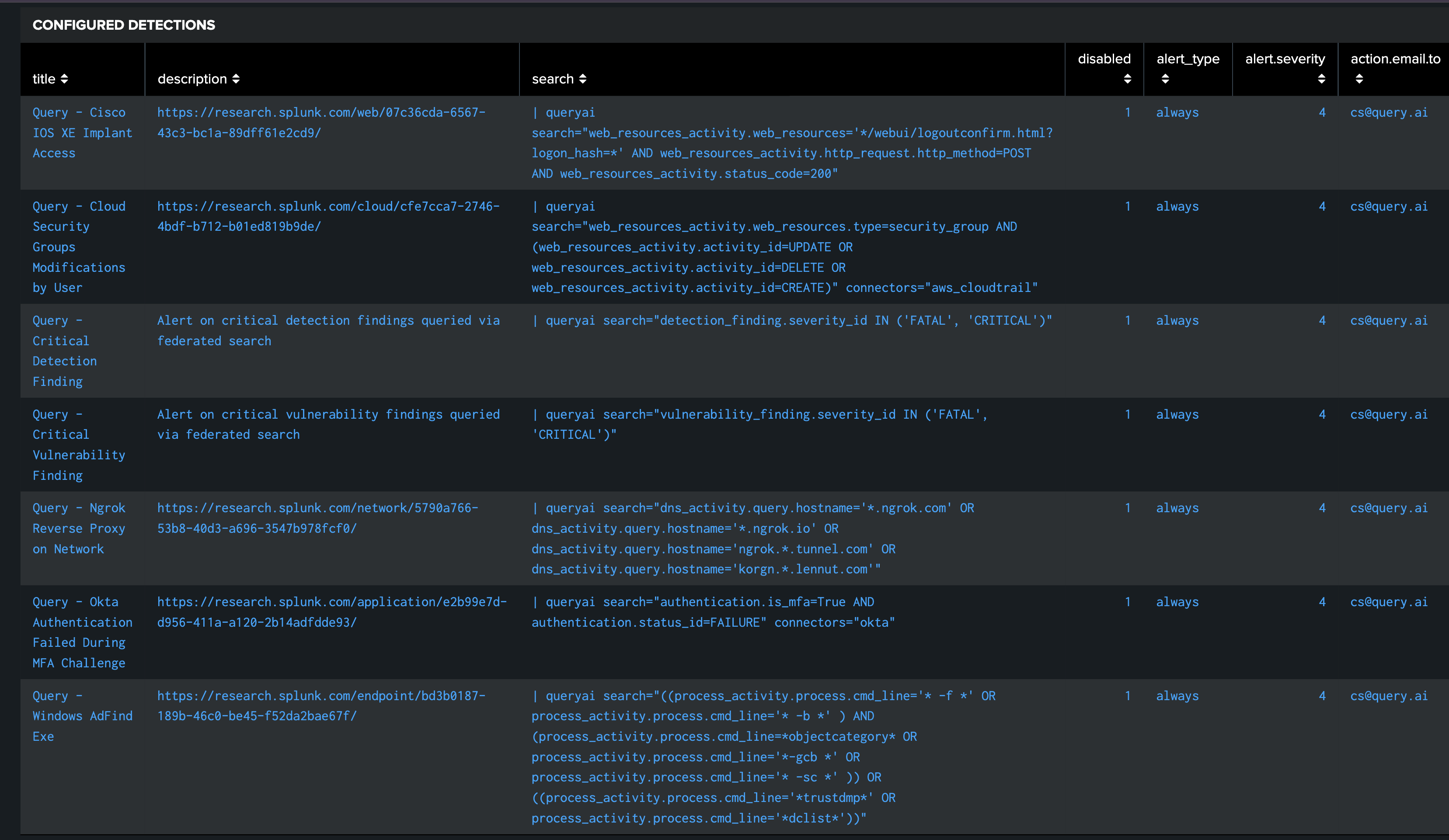
How the Query Splunk App Works
Click here to see the Query architecture page, which offers a diagram showing how your searches from Splunk are run against Query-connected repositories by acting as a client to Query.
Updated 4 months ago
Read on for more about how to Search with the Query Splunk app, or if it's not yet configured, how to set it up.