Carbon Black Cloud
Integrate Query Federated Security with Carbon Black Cloud to search about details on Alerts, Host Vulnerabilities, Process Events, Observations, and Machine Inventory
TL;DRTo integrate Carbon Black Cloud with Query Federated Security:
- Create an API Access Level with minimum necessary permissions and use it to create a new API Key.
- Gather your Instance URL and Org Key for use in configuration.
- Create and save a Carbon Black Cloud Connector in the Query Federated Security platform.
- Use Query Federated Security to parallelize searches and surface details about alerts, devices, observations, processes, and vulnerabilities for incident response (IR), threat hunting, investigations, and other security and observability use cases.
Overview
Carbon Black Cloud by Broadcom (formerly known as VMWare Carbon Black and Carbon Black EDR) is an enterprise Endpoint Detection & Response (EDR) suite that also offerings Extended Detection & Response (XDR), Vulnerability Management (TVM), and Container Security solutions within the platform. Carbon Black provides protection to MacOS, Linux, and Windows hosts across VMWare eSXI, Hyper-V, public cloud (e.g., AWS, GCP, Azure), and on-premises solutions and unlocks additional capabilities with the proper licenses. Carbon Black also provides API-native mechanisms to expose raw telemetry in addition to inventory and alerting data centrally, making it a great choice for SecOps teams to use.
All federated searches have their searches and results expressed in the terms of the Query Data Model (QDM), which is based on the Open Cybersecurity Schema Framework (OCSF). Each API source is normalized into a specific QDM/OCSF Event Class to standardize and normalize the data for increased situational awareness, ease of aggregation of filtering, and easy pivoting.
API Name | QDM/OCSF Event Class | Entities/Observables |
|---|---|---|
Email Address | ||
Command Line | ||
File Hash | ||
File Hash | ||
File Hash | ||
CVE ID |
Query Federated Security provides a Connector to Carbon Black Cloud allowing you to transparently interact with a variety of APIs that contain important data and metadata for incident responders, investigators, threat hunters, triage teams, audit teams, and more. Query uses API Keys to authenticate to the Carbon Black Cloud APIs and provides full translation of the native Lucene filters used by Carbon Black to ensure that the right information comes back to you. For instance, searching for a Resource Name Entity in Query Federated Security will automatically craft Lucene filters across the various APIs in parallel for the following raw data key-value pairs:
- Devices:
name,ad_distinguished_name,appliance_name,auto_scaling_group_name,cluster_name,vcenter_name,vm_name, andcloud_provider_resource_group - Alerts:
device_name - Observations:
device_name - Process Search:
device_name - Host Vulnerabilities:
affected_assets[]
From there, any matches on your conditions (e.g., case sensitive equality search, or "starts with" searches) will match on the raw data in Carbon Black. This data is automatically normalized into the aforementioned OCSF Event Classes with full data normalization and context and this data is streamed and collated back to the Query Federated Security UI (or within Splunk using our Splunk App, or otherwise using our FSQL API) showing all of the data. This helps to close the OODA loop and allows the full context of a specific Device (as in this example) to be shown. Instead of pivoting across 5 different tabs in Carbon Black, or joining across multiple indexes or tables in a SIEM or Data Lake, Query Federated Security provides all of the data you need without ever duplicating or persisting it.
Some details on searchesTo use the full range of capabilities provided by Query Federated Security, you must have the following licenses activated:
- Endpoint Standard
- Enterprise EDR
- Vulnerability Management for Endpoints
Query Federated Search does not support any other APIs from the other license tiers.
Prerequisites
To connect a Carbon Black Cloud Connector with Query Federated Security you'll need to retrieve your Carbon Black Cloud instance URL and Org Key. Additionally, you'll need to create an API Access Level to use to create an API Key with minimum necessary permissions.
-
To retrieve your instance URL, when you log into your Carbon Black Cloud instance, simply copy the value from your browser. You only need the root of the URL such as
https://defense-prod01.superdeploy.net -
To retrieve your Org Key navigate to the Settings tab on the left-hand navigation pane and select General, the Org Key is on the upper left-hand side of the screen as shown below (FIG. 1).
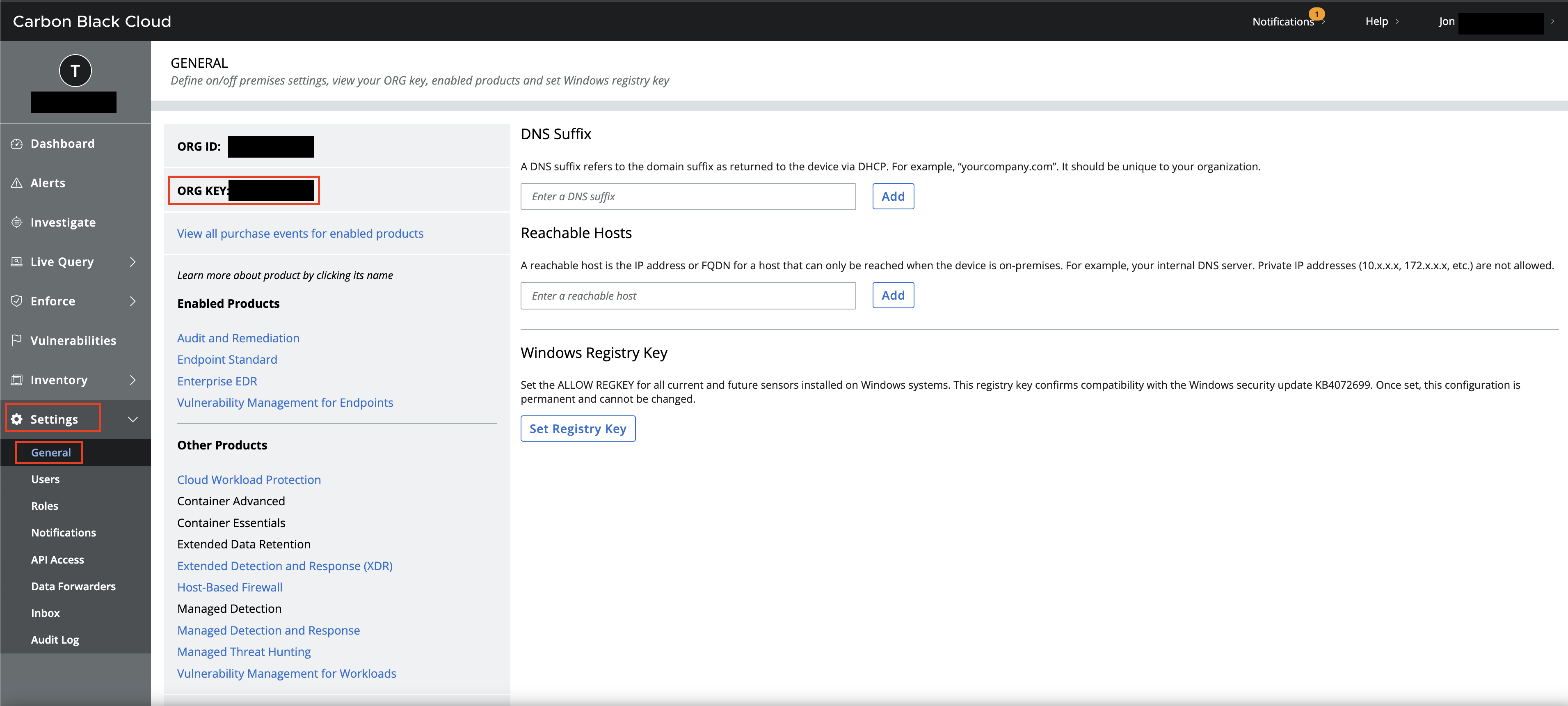
FIG. 1 - Retrieving the Carbon Black Cloud Org Key
-
To create an API Access Level navigate to Settings -> API Access and select the Access Levels tab, and select Add Access Level as shown below (FIG. 2).
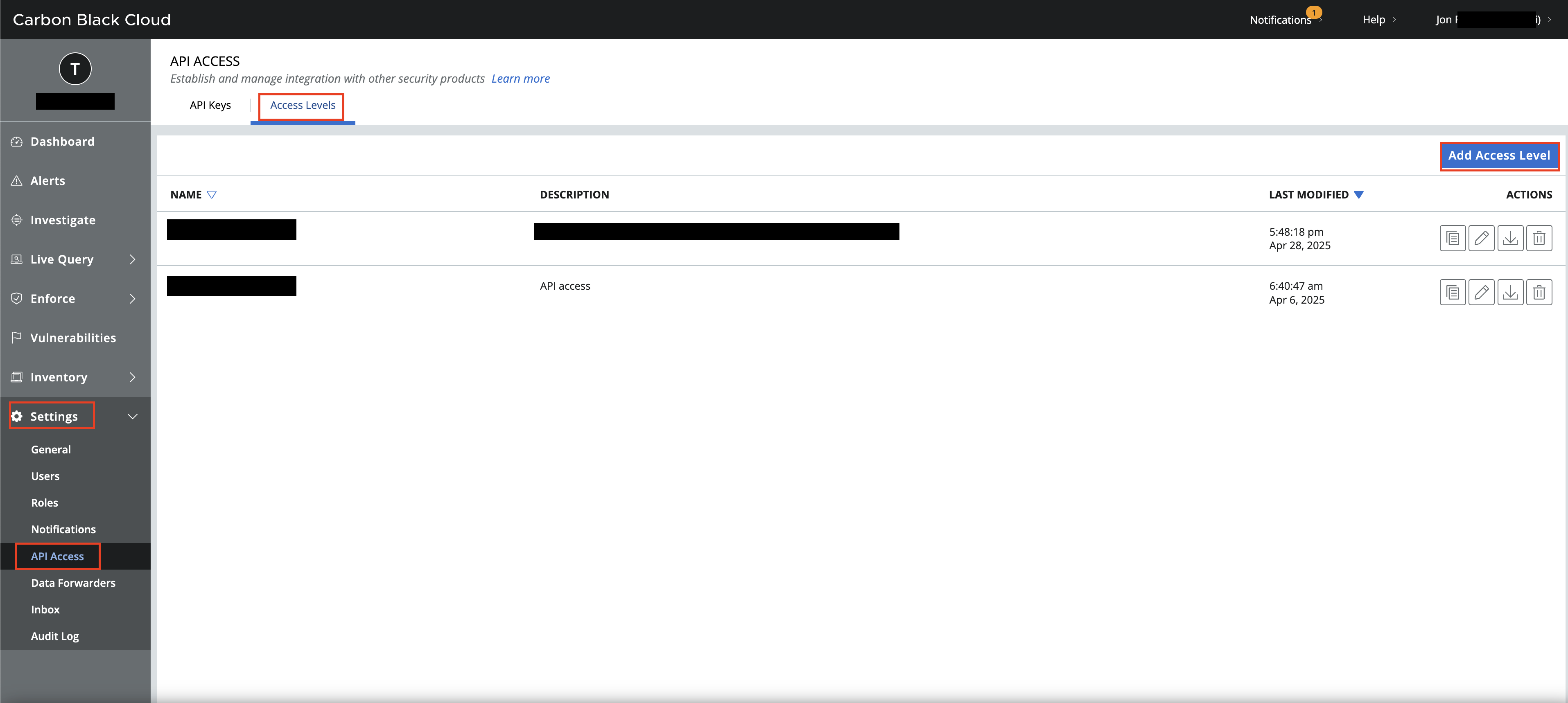
FIG. 2 - Creating an API Access Level
-
Provide a Name (such as
QueryFederatedSecurityAccess) and a Description. Then add the following .Notation Name scopes with the following CRUD permissions, and select Save as shown below (FIG. 3):-
org.alerts: READ -
org.audits: READ -
jobs.status: READ -
device: READ -
livequery.manage: CREATE, READ (this is required for the Process Search and Observations APIs) -
org.search.events: CREATE, READ (this is required for the Process Search and Observations APIs) -
vulnerabilityAssessment.data: READ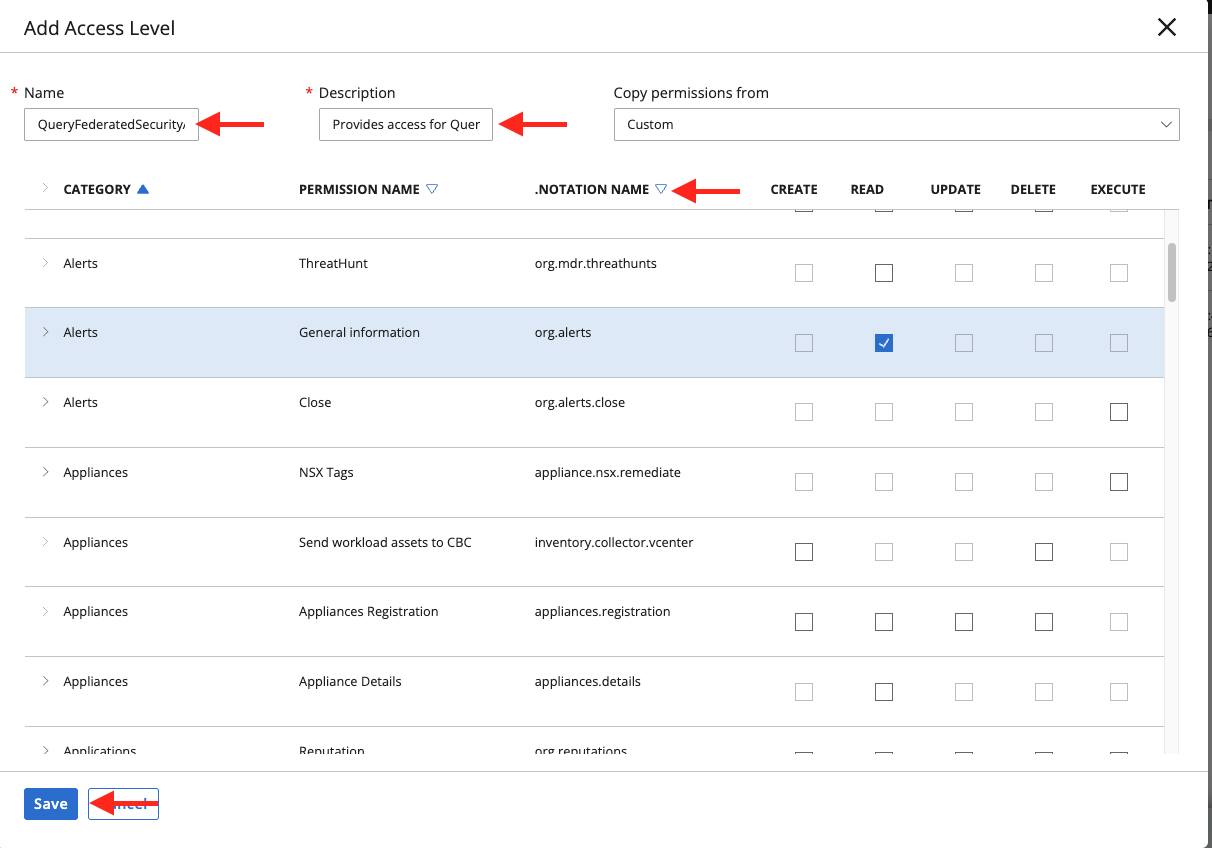
FIG. 3 - Finalized configuration of an API Access Level
-
-
From the same page, navigate to the API Keys tab and select Add API Key. Provide a Name (such as
QueryFederatedSecurityConnector), Description, and select the Custom Access Level you created in Step 4. To add another layer of network security, reach out to your Query CSM or SE for our Production IP range(s) to add as Authorized IP Addresses. Once complete, select Save as shown below (FIG. 4).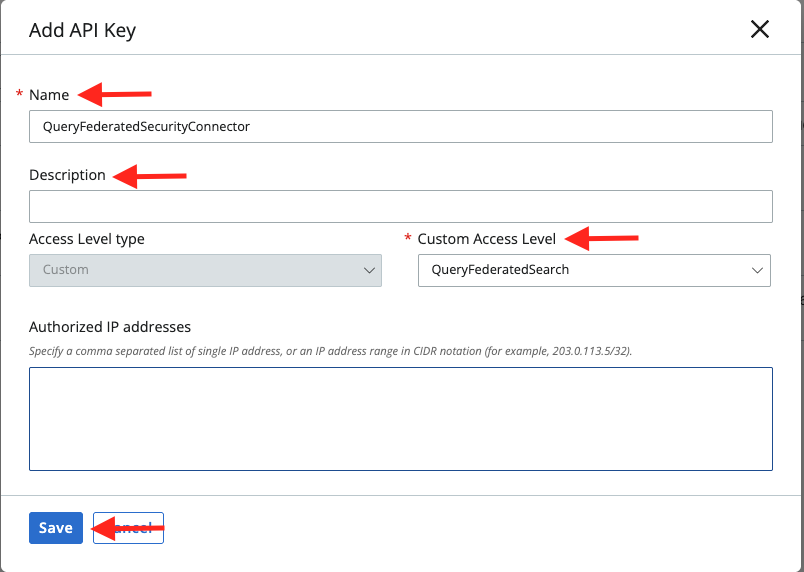
FIG. 4 - Configuring an API Key
-
Once complete you will receive a popup window (as shown below in FIG. 5) that contains the API ID and API Secret Key, copy these values and securely store them in a password management tool or PIM/PAM tool to save for later configuration.
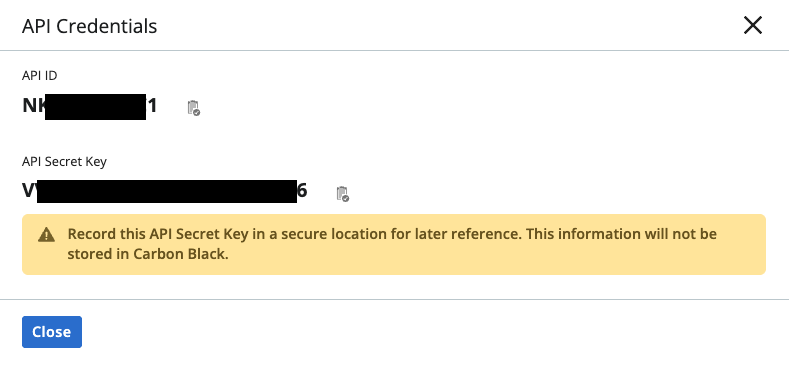
FIG. 5 - Carbon Black API Credentials pop-up
To learn how to configure a Carbon Black Cloud Connector, proceed to the next section.
On NHI securityNHI - or, Non-Human Identities - such as your Carbon Black Cloud API keys are extremely sensitive, especially with the amount of read and write permissions required. Query securely stores the Client Secret in a dedicated AWS Secrets Manager Secret per Connector per Tenant.
While this requires you to configure Connectors per Carbon Black instance (e.g., if you're in a multi-division company or part of a MSSP) and continue to enter in your credentials, every copy is stored as securely as each other with minimum necessary permissions that only allows the specific piece of serverless infrastructure to retrieve the secret, it is never cached or persisted outside of the Secret.
Setting up the Carbon Black Cloud Connector
Use the following steps to create a new Query Federated Security Connector for Carbon Black Cloud.
-
Navigate to the Connectors page, select Add Connector, and selectCarbon Black Cloud from the
Endpointcategory as shown below (FIG. 6). You can also search for Carbon Black Cloud using the search bar in the Add Connector page.
FIG. 6 - Locating the Carbon Black Cloud Connector
-
In the Configure Connector tab, add the following detail as shown below (FIG. 7):
-
Connector Alias Name: The human-readable name you want to give to this connector, you can provide the name of your tenant, or a name of a customer if you are a MSSP or MDR provider.
-
Default Login: Leave the default value:
Default Login. -
Base URL: Your Carbon Black Cloud instance URL, copied in Step 1 of the Prerequisites section.
-
Org Key: Your Carbon Black Cloud Org Key, copied in Step 2 of the Prerequisites section.
-
API Secret: The secret key portion of your API key, copied in Step 6 of the Prerequisites section.
-
API ID: The API key ID, copied in Step 6 of the Prerequisites section.
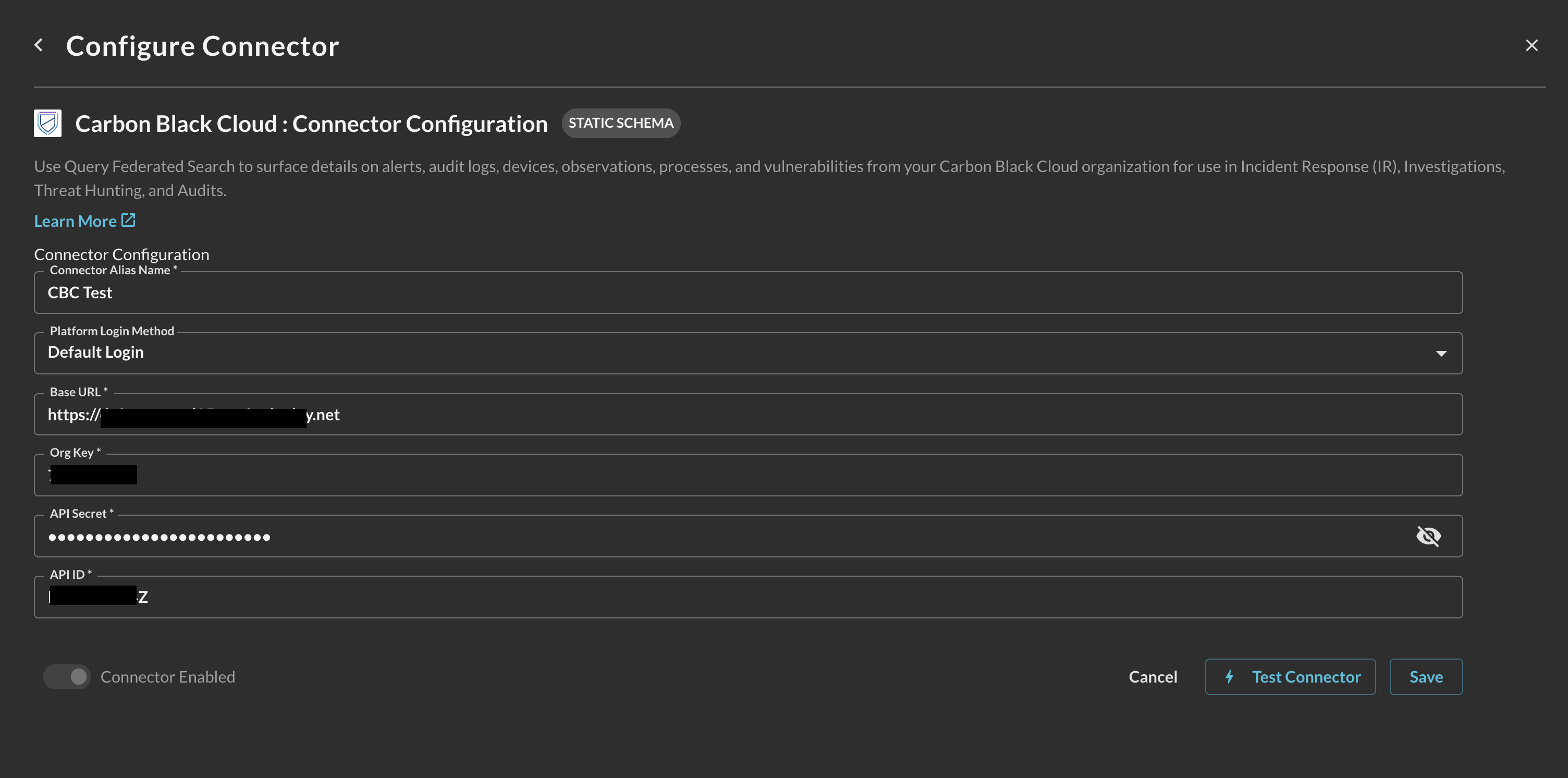
FIG. 7 - Configuring the Carbon Black Cloud Connector
-
-
Select Save to save and activate the Connector.
-
Select Test Connection from the bottom-right of the connection pane to ensure that your instance URL, Org Key, and API credentials are all valid and that you have the required permissions to hit every single API endpoint.
You will now see Carbon Black Cloud added as an available Connector within the Query Search and Query Summary Insights UI.
Querying Carbon Black Cloud Connectors
Within the Query Search UI, all Connectors are enabled by default. To check that your specified Connector(s) for Carbon Black Cloud are enabled, navigate to the Endpoint section of the Selected Connectors dropdown and ensure that your specified Carbon Black Cloud Connector(s) are are selected (denoted by a checkbox) before running your searches as shown below (FIG. 8).
Entity-based Search
The Carbon Black Cloud Connector is a static schema Connector which means that all normalization and search translation is completely defined by the Query team. Refer back to the Introduction section and refer to the table to learn which Entities map against which Carbon Black Cloud. For instance, the Devices API supports a vast majority of potential mappings into Entities whereas Vulnerabilities for Hosts only support a handful. For a more complete mapping of what key-value pairs map to what Entity specifically, please reach out to your Query CSM or SE.
In the Federated Search console, select the search dropdown, ensure the Entities radio button is selected and search for your desired Entity as shown below (FIG. 9). For instance, you can search for devices by hostname which can pull data from Processes, Observations, and Alerts or Vulnerabilities, these can be further correlated against other different Query Connectors.
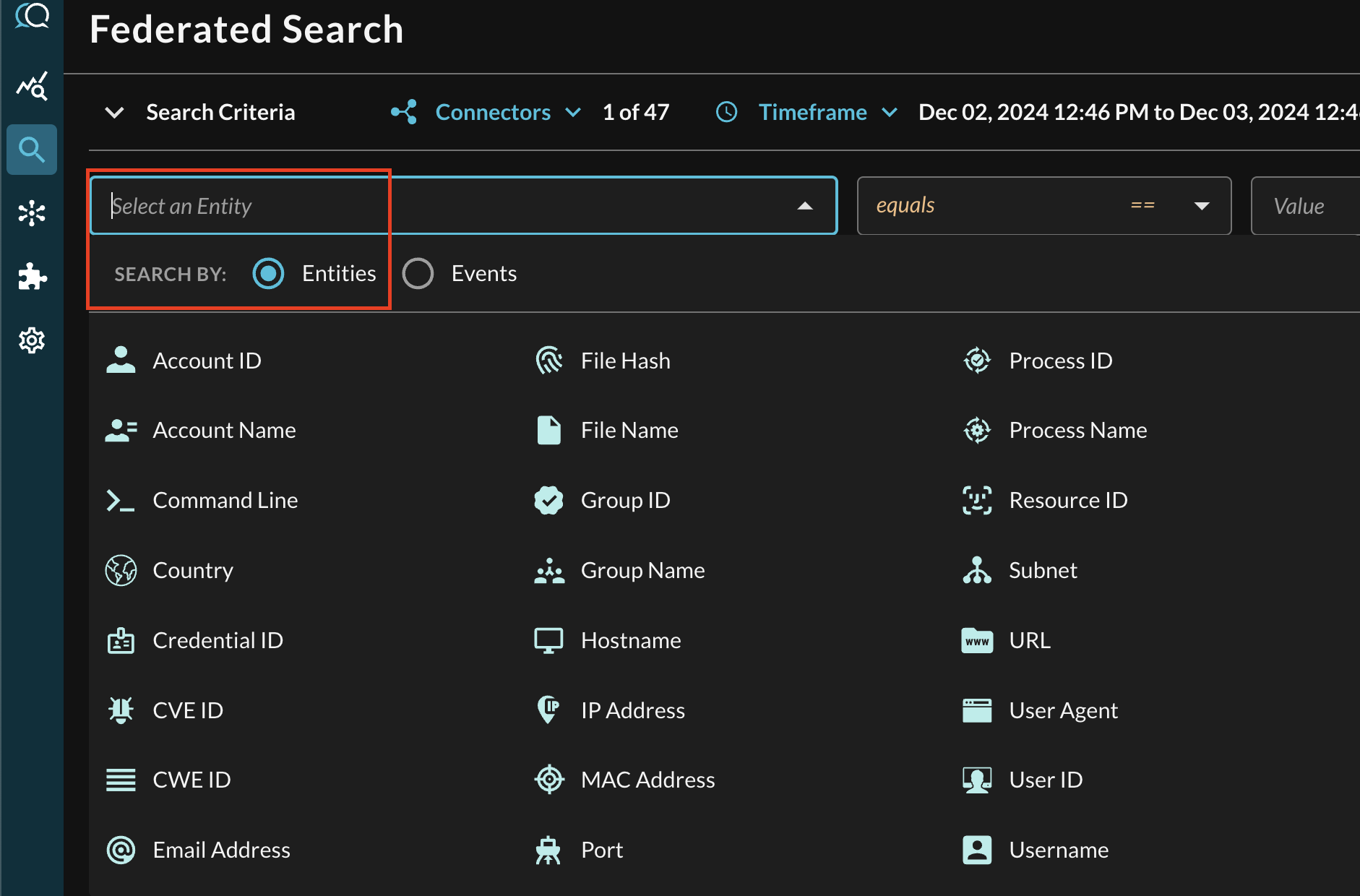
FIG. 9 - Entity-based searching with Query Federated Search
After selecting an Entity, most allow you to specify an Operator. This allows you to perform simple equality searches or to perform more generalized searches using Contains, Starts With, or Ends With Operators. These are mapped against appropriate Carbon Black Cloud Lucene filter operators.
When you search for multiple values that may be present across different Connectors, the Query Federated Search query planner inspects the Configure Schema metadata to ensure searches are sent to the appropriate Connectors, this operates more as a collated window function within Query and not as an expensive SQL join.
Additionally, you can specify case-sensitivity for the entire search criteria. An example of a multi-value CVE search that uses the equals operator and toggled case-sensitivity is shown below (FIG. 10).
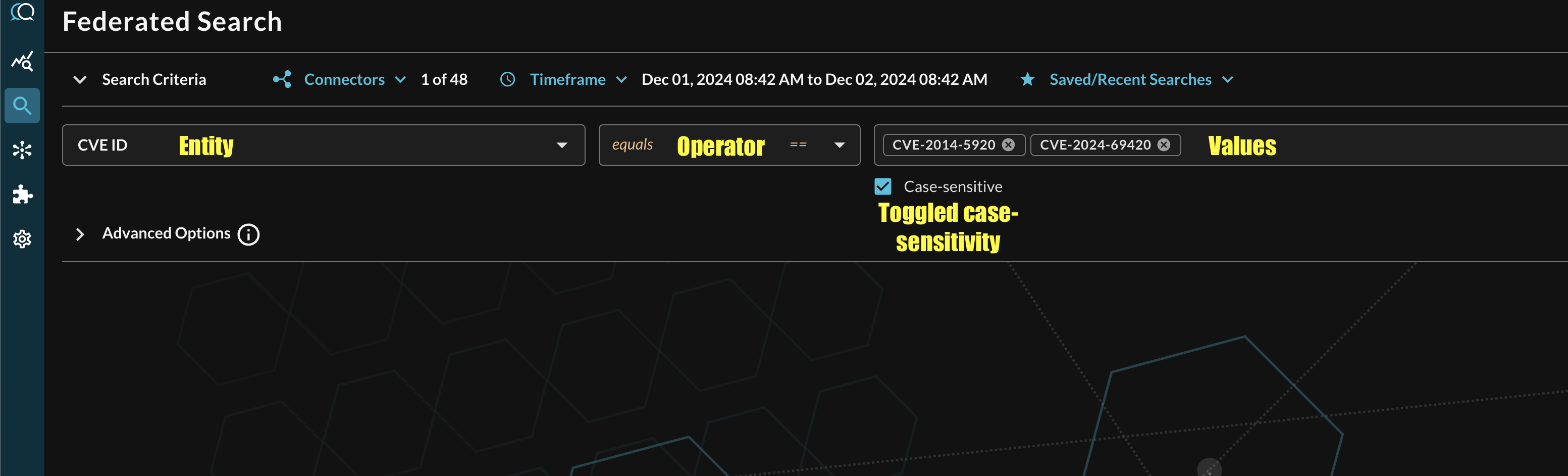
FIG. 10 - Orientation for Entity-based search in Query Federated Search
Event-based Search
Event-based searches allow you to broadly search across the entirety of results from a downstream API, or, search for very specific results based on filters. Refer back to the Introduction section and refer to the table to learn which Events map to the Carbon Black Cloud Connector.
Resources
Troubleshooting Steps
- Ensure that your Carbon Black Cloud URL is correct and not malformed.
- Ensure that you have the required licenses activated in your tenant.
- Ensure that you have vulnerabilities, alerts, or other activity for a given time period in your instance to compare search results against.
- Ensure that your API Access Level have the correct scopes.
- Ensure that your API Credentials (API ID & API Secret ID) were not malformed or expired, if needed, you can delete and recreate the API keys and simply override and save your Connector to update it. Old credentials will be purged from our system.
If you have exhausted the above Troubleshooting list, please contact your designated Query Sales Engineer or Customer Success Manager. If you are using a free tenant, please contact Query Customer Success via the Support email in the Help section, or via Intercom within your tenant.
Updated 3 months ago