CISA Known Exploited Vulnerabilities (KEV) Catalog
Integrate Query with the CISA KEV Catalog to automatically retrieve enriched vulnerability details of CVEs in the KEV by their CVE ID or CWE ID. The CVE data is further enriched by the Mitre AWG CVE API.
TL;DRTo integrate the CISA KEV Catalog Connector with Query:
- Configure a CISA KEV Connector.
- Use Query Search to parallelize searches and surface details about CVEs and CWEs on the CISA KEV Catalog for incident response (IR), threat hunting, investigations, and other security and observability enrichment use cases.
Overview
The United States Cyber and Infrastructure Security Agency (CISA) Known Exploited Vulnerabilities (KEV) Catalog is a collection of Common Vulnerability and Enumerations (CVEs) that are observed to have been actively exploitable by a variety of threat actors by CISA. Each of these vulnerabilities contain basic information such as commentary from CISA, reporting details, and a naming convention. The concept of the KEV Catalog is to use these vulnerabilities as an input to your vulnerability and patch management program's prioritization workflow(s).
To provide more useable details as enrichment to each CVE listed in the KEV, Query additionally enriches the final normalized record with metadata about the CVE from Mitre's AWG CVE API. This ensures that potentially important metadata such as the descriptions, titles, Common Platforms and Enumerations (CPEs), semantic version data for impacted software packages, potential remediation detail, and scoring (e.g., CVSS 3.1 and CVSS 4.0) details are provided.
All federated searches have their searches and results expressed in the terms of the Query Data Model (QDM), which is based on the Open Cybersecurity Schema Framework (OCSF). Each API source is normalized into a specific QDM/OCSF Event Class to standardize and normalize the data for increased situational awareness, ease of aggregation of filtering, and easy pivoting.
API Name | QDM/OCSF Event Class | Entities/Observables |
|---|---|---|
CVE ID |
By searching for CVEs or CWEs with Query, if a match is found in the KEV, the fully enriched record from the combination of both data sources will be returned as a collated record. The intended usage is if you are searching for a specific CVE or CWE within Query Federated Search - either prompted by an external tool, or as a pivot - if there is a match in the KEV Catalog, that detail will be brought back. Analysts can then examine the metadata and make decisions around countermeasures, patching, remediation, and otherwise.
Some details on searchesThe CISA KEV only contains a modicum of details; a name & short description from CISA, CVE ID, and CWE ID(s). To bring forward CVE-specific details as well as Common Packages & Enumerations (CPE), semantic version details, publish details, and other metadata the Mitre AWG CVE API is used and that data is combined into the final normalized Event Class.
This is ONLY done if the CVE is in the KEV Catalog, if there is not a match, this enrichment will not happen automatically.
Prerequisites
To connect a CISA KEV Catalog Connector with Query Federated Search you do not need to do any additional steps. You can change the base URLs if you have your own proxy or source of the data as long as the downstream endpoints and schema are the exact same, otherwise errors will be thrown and you'll be very sad!
To learn how to configure a CISA KEV Catalog Connector, proceed to the next section.
Setting up the CISA KEV Catalog Connector
Use the following steps to create a new Query Federated Search Connector for the CISA KEV Catalog.
-
Navigate to the Connectors page, select Add Connector, and selectCISA Known Exploitable Vulnerabilities (KEV) Catalog from the
Threat Intelligence and Enrichmentcategory as shown below (FIG. 1). You can also search for CISA Known Exploitable Vulnerabilities (KEV) Catalog using the search bar in the Add Connector page.
FIG. 1 - Locating the CISA KEV Catalog Connector in the Query Federated Search connectors page
-
In the Configure Connector tab, add the following detail as shown below (FIG. 2):
-
Connector Alias Name: The human-readable name you want to give to this connector, you can provide the name...
-
Default Login: Leave the default value:
Default Login. -
KEV API: The CISA KEV Catalog URL, leave the default value unless you know what you are doing.
-
CVE AWG Mitre API: The Mitre AWG CVE API endpoint, leave the default value unless you know what you are doing.
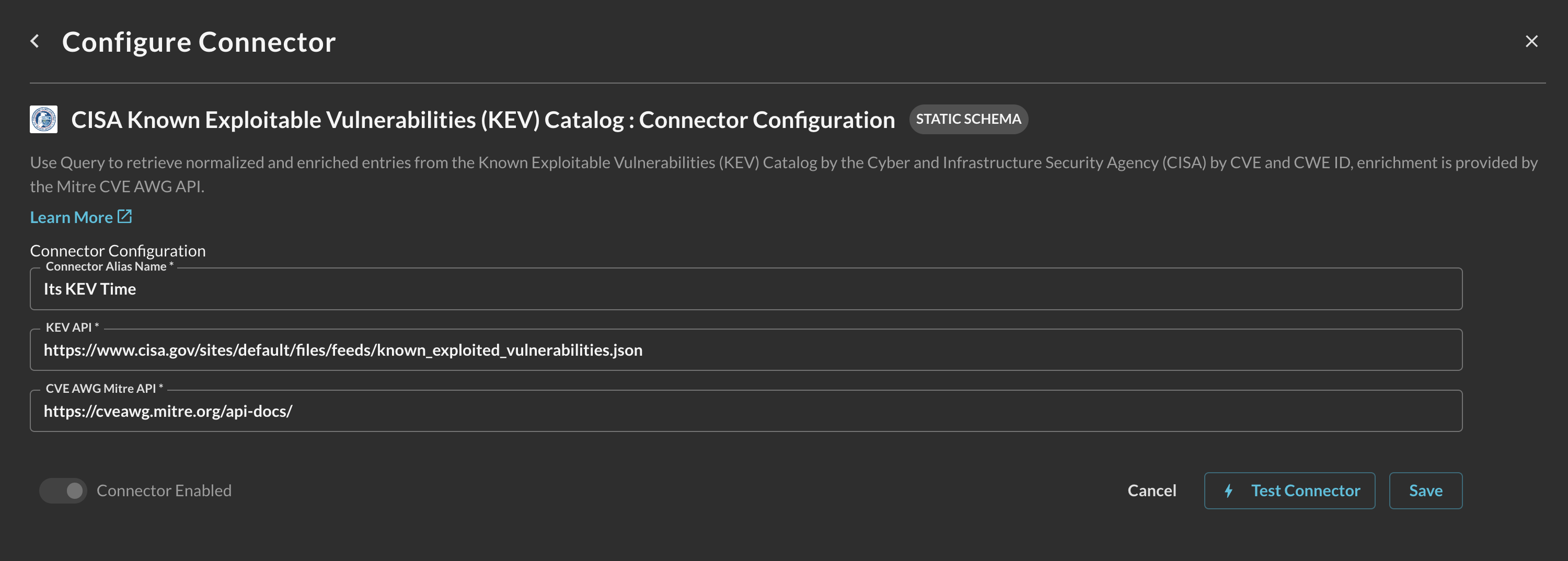
FIG. 2 - Configuring the CISA KEV Catalog Connector
-
-
Select Save to save and activate the Connector.
-
Finally, select Test Connection from the bottom-right of the connection pane to ensure that connectivity to the KEV Catalog and Mitre AWG CVE API endpoints can be established.
You will now see CISA KEV Catalog added as an available Connector within the Query Search and Query Summary Insights UI.
Querying CISA KEV Catalog Connectors
Within the Query Search UI, all Connectors are enabled by default. To check that your specified Connector(s) for INTEGRATION are enabled, navigate to the Threat Intelligence and Enrichment section of the Selected Connectors dropdown and ensure that your specified CISA KEV Catalog Connector(s) are are selected (denoted by a checkbox) before running your searches as shown below (FIG. 3).
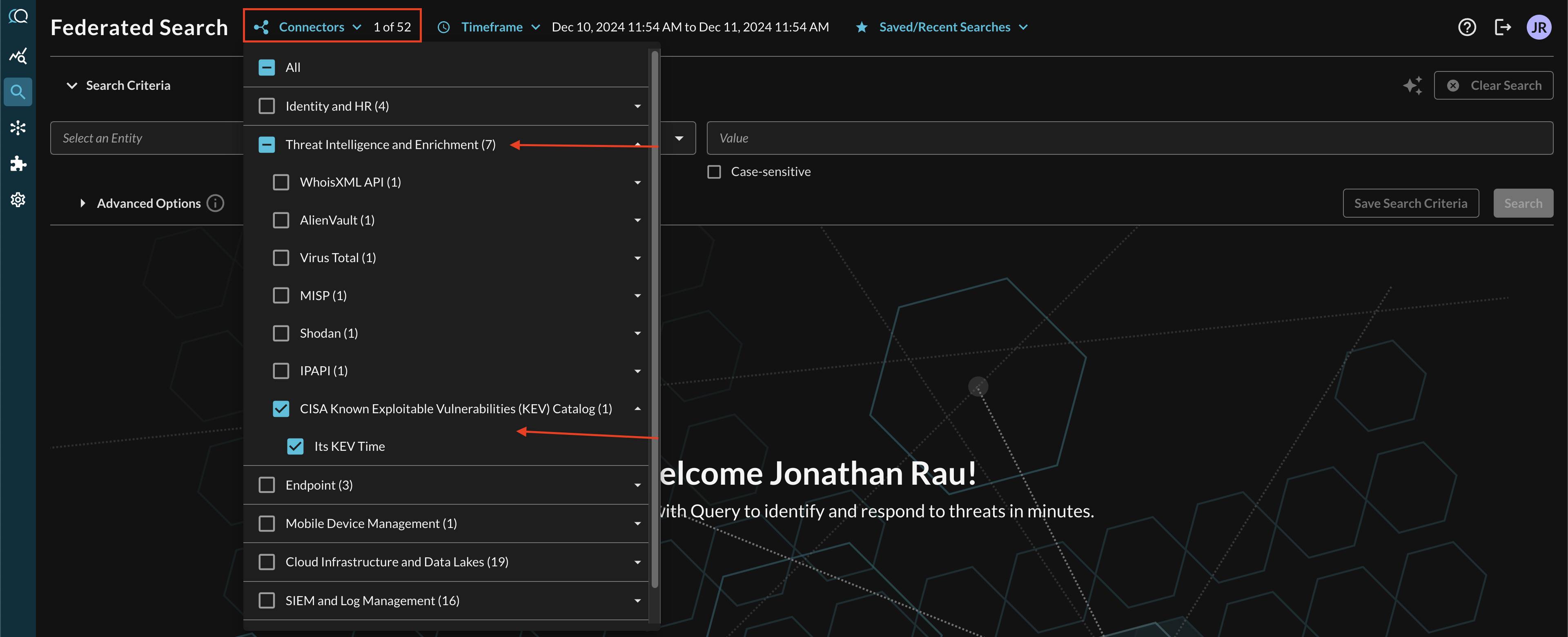
FIG. 3 - Selecting the CISA KEV Catalog Connector in Query Federated Search
Entity-based Search
The CISA KEV Catalog Connector is a static schema Connector which means that all normalization and search translation is completely defined by the Query team. Refer back to the Introduction section and refer to the table to learn which Entities map against the CISA KEV Catalog Connector.
In the Federated Search console, select the search dropdown, ensure the Entities radio button is selected and search for your desired Entity as shown below (FIG. 4). For instance, you can search by CVE or CWE ID(s), these can be further correlated against other different Query Connectors that also contain CVE or CWE information, such as Amazon Inspector data in Amazon Security Lake, or vulnerabilities reported by Microsoft Defender for Endpoint.
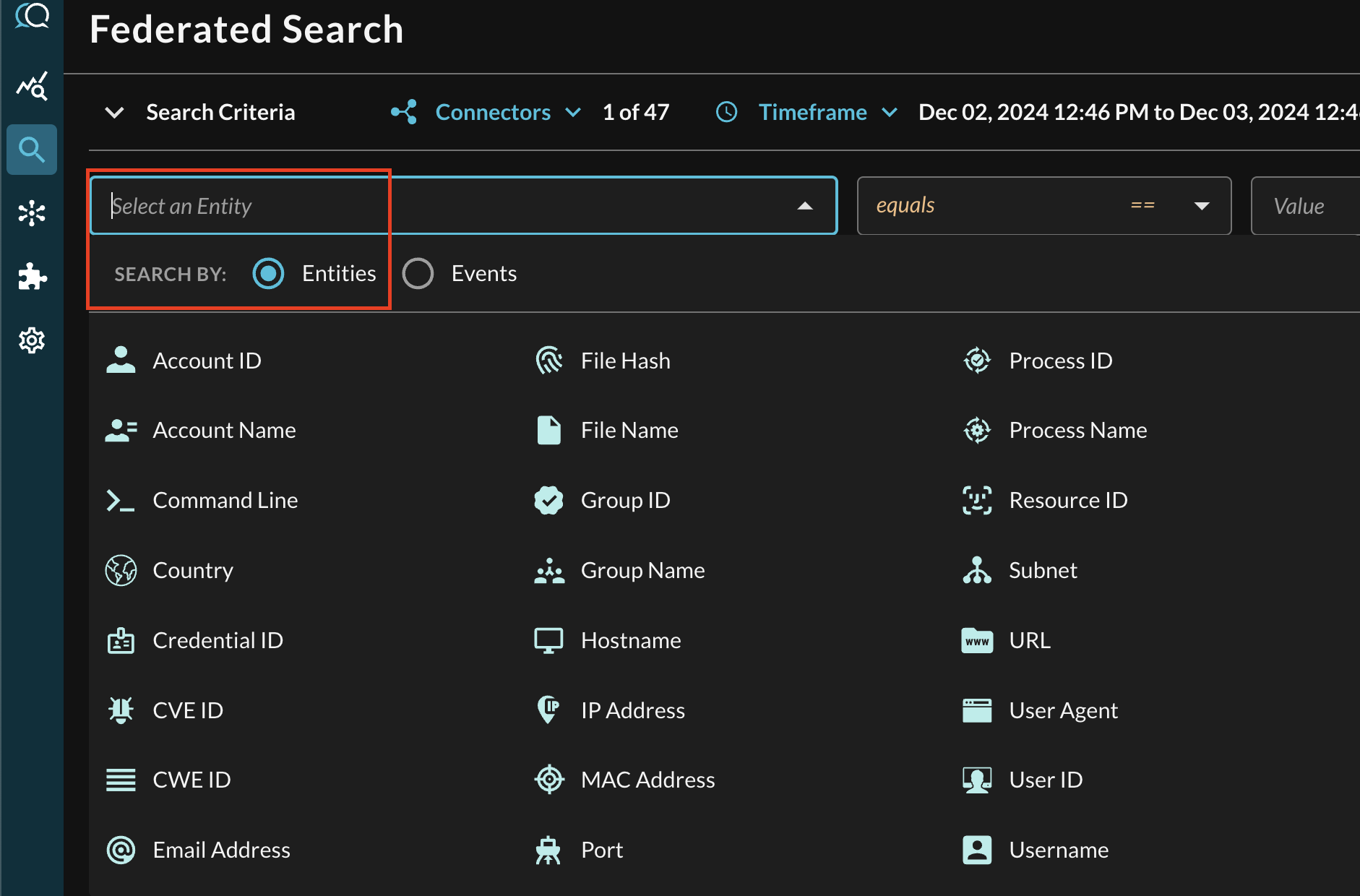
FIG. 4 - Entity-based searching with Query Federated Search
After selecting an Entity, most allow you to specify an Operator. This allows you to perform simple equality searches or to perform more generalized searches using Contains, Starts With, or Ends With Operators. Only the equality operator is supported for this Connector.
When you search for multiple values that may be present across different Connectors, the Query Federated Search query planner inspects the Configure Schema metadata to ensure searches are sent to the appropriate Connectors, this operates more as a collated window function within Query and not as an expensive SQL join.
Additionally, you can specify case-sensitivity for the entire search criteria. An example of a multi-value CVE search that uses the equals operator and toggled case-sensitivity is shown below (FIG. 5).
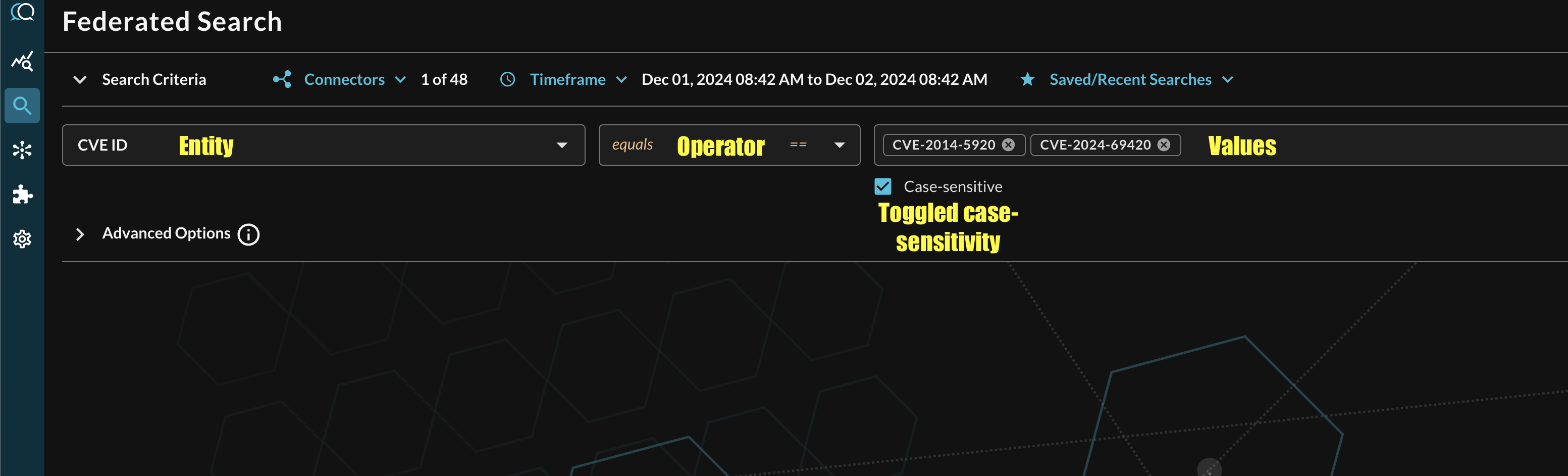
FIG. 5 - Orientation for Entity-based search in Query Federated Search
Event-based Search
Event-based searches allow you to broadly search across the entirety of results from a downstream API, or, search for very specific results based on filters. Refer back to the Introduction section and refer to the table to learn which Events map against the connector.
Due to having to start from a CVE ID or CWE ID, Event-based searches and advanced filters are not supported at this time.
Resources
Troubleshooting Steps
- Ensure that the URL endpoints were not changed, if they were, ensure that your mirror matches the same schema for the JSON file and endpoints.
- Ensure that the URLs are both up, we respect 429s, but we cannot handle 500-series HTTP errors.
If you have exhausted the above Troubleshooting list, please contact your designated Query Sales Engineer or Customer Success Manager. If you are using a free tenant, please contact Query Customer Success via the Support email in the Help section, or via Intercom within your tenant.
Updated 4 months ago