SentinelOne Singularity Platform
Integrate with the SentinelOne Singularity Platform capabilities
TL;DRTo integrate SentinelOne with Query:
- Create a Service User with Account-level Viewer access and generate an API Key.
- Add a connection source in Query using your SentinelOne Instance URL and Service User API Key.
- Use Query Search to surface information about Events, Agents (Sentinels), and Users within the SentinelOne Singularity Platform.
Overview
SentinelOne is an Extended Detection & Response (XDR) and Endpoint Protection Platform (EPP) that provides AI-based and signature-based protection across Windows, Linux, MacOS, and Kubernetes clusters in addition to network horizontal discovery (via SentinelOne Ranger), and provides a built in security lake platform and powerful query language for surfacing telemetry data about Sentinels deployed into your Account among other features.
As of 1 NOV 2023, Query integrates with SentinelOne to surface details about Sentinels (A.K.A. agents or sensors), Users within the SentinelOne Singularity Platform itself, and Events generated by Sentinels for malicious or suspicious activities found on your endpoints and servers. In the future, integrations into the SingularityXDR via Deep Visibility, the Activity Stream, Rangers, and other parts of the platform will be integrated into Query's Federated Search capabilities.
For information on the capabilities supported within the SentinelOne Singularity Platform as well as the types of Entities, Events, and Objects you are able to search from it within the Query Federated Search Platform refer to the Querying from the SentinelOne Singularity Platform section below. Using the Query Federated Search Platform with SentinelOne Singularity Platform and other Connectors enables analysts to quickly Orient, Decide and Act on data as it comes back. For instance, when investigating an active Incident coming from SentinelOne you can search the File Hash or Filename within the Query Federated Search Platform and quickly retrieve relevant normalized security findings, any information on the file hash from Threat Intelligence & Enrichment platforms, and potentially application and network logs and other security findings related to these artifacts.
Prerequisites
The SentinelOne integration relies on using an API Key from a Service User as is recommended by SentinelOne. Use the following steps to create a Service User and generate an API Key.
- Login to your SentinelOne tenant with an Administrator (Admin) user.
- In the left-hand navigation pane select Settings, select Users from the tabs along the top of the screen, and choose Service Users in the menu underneath the Settings tab as shown below.
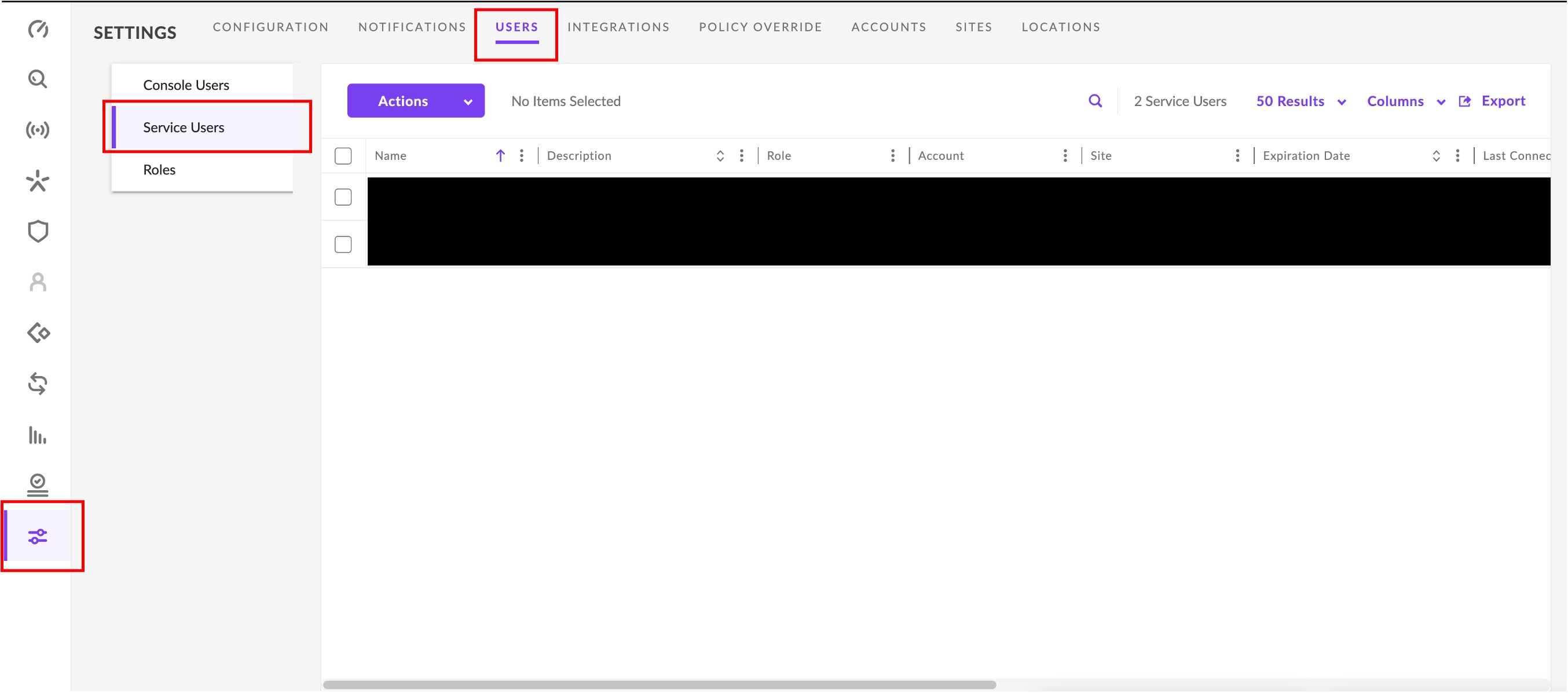
- In the Actions menu select Create New Service User.
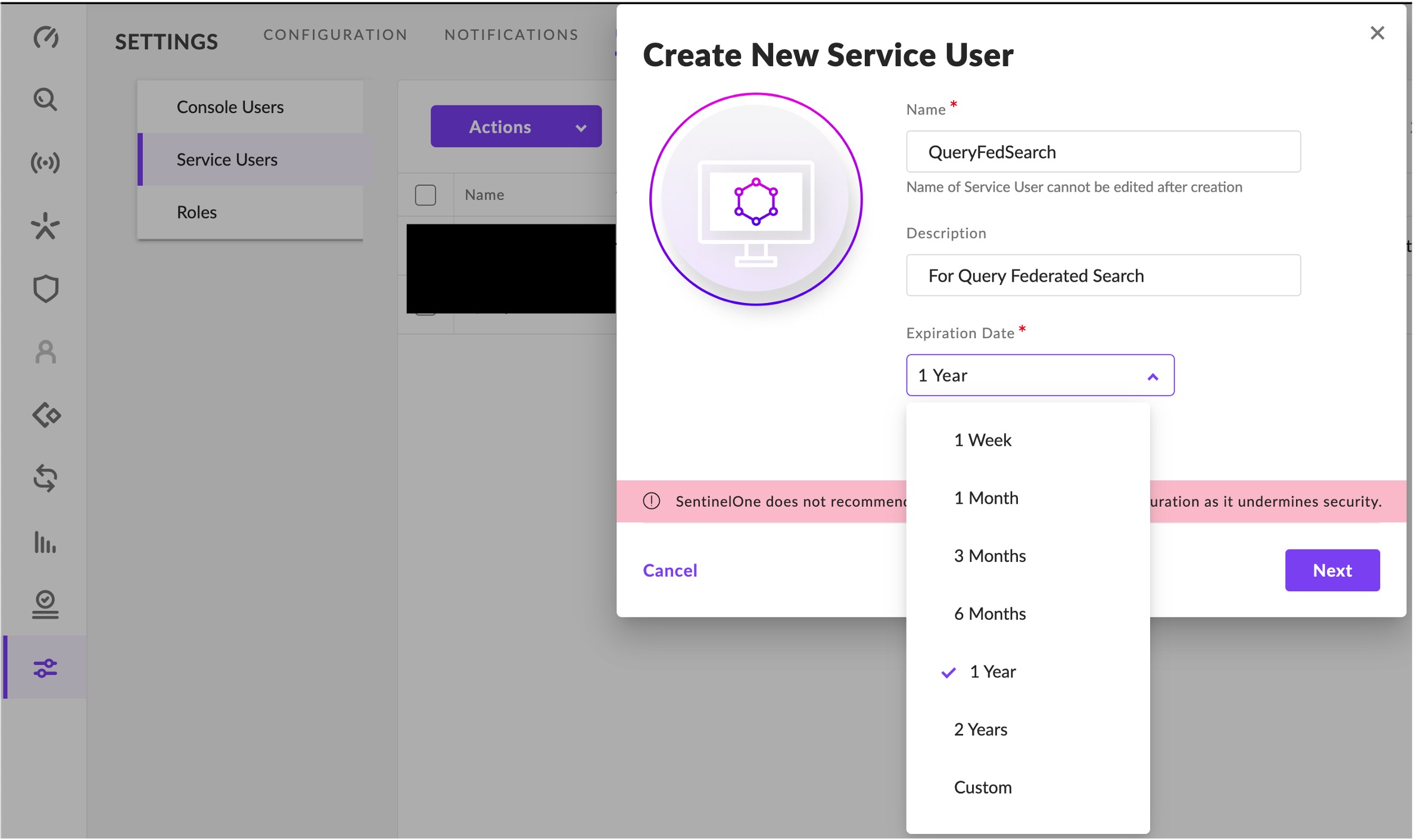
- Enter a Name, an optional Description (e.g.,
Service User for Query Federated Search), and select an Expiration Date for your credentials, SentinelOne recommends setting 1-month or less time boxes as shown below.
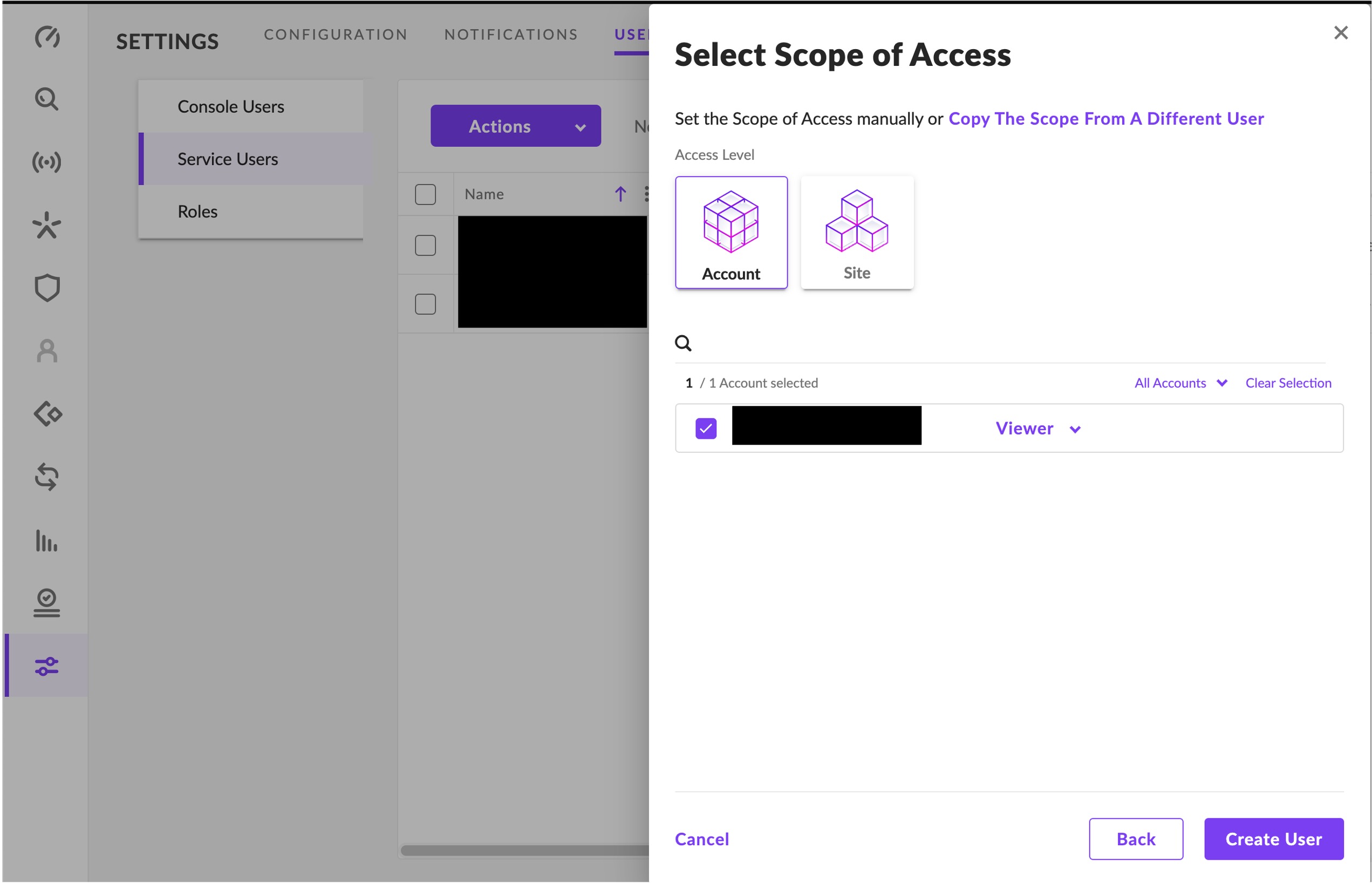
- In the Select Scope of Access menu choose
Accountfor the Access Level and ensure that you provideViewerpermissions. Finally, select Create User as shown below.
- After optionally re-authenticating with your MFA code (only if prompted!) ensure that you copy your API Token or you will have to repeat steps 2-5 again!
Adding a connection source
Use the following steps to create a new Query Federated Search Connector for the SentinelOne Singularity Platform.
-
Navigate to the Connections page, select Add Connections, and selectSentinelOne from the Endpoint category as shown below you can speed this up by typing
SentinelOneinto the search bar.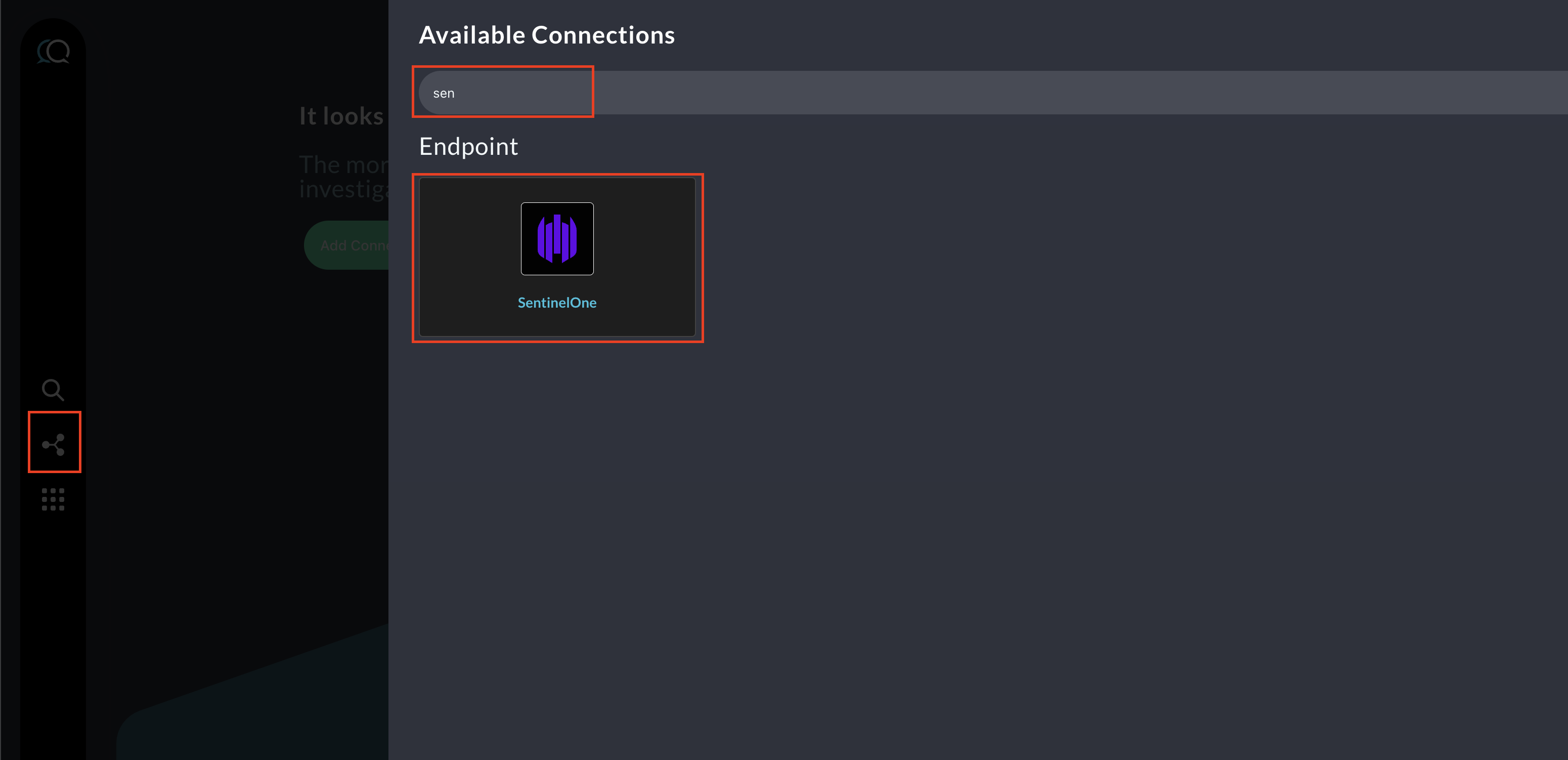
-
In the General tab, add the following detail:
- Name: The human-readable name you want to give to this connector, you can name it whatever you want, but you can use this to delineate across different APIs or Instances, especially if you're a part of a Managed Security Services Provider (MSSP).
- Platform Instance: Leave the default value (e.g.,
SentinelOne). - Instance URL: The FQDN of your SentinelOne Singularity Platform tenant (e.g.,
https://[YOUR-TENANT-ID].sentinelone.net - Service User API Key: Enter the Account-wide Scoped Service User API key you created in the previous section here, this value is handled like a secret and is securely vaulted in the Query Federated Search Platform's Privileged Identity Management (PIM) vault in our backend.
-
Select Test Connection from the top-right of the connection pane to ensure that your API Key is valid for your Instance and you can pull information from the SentinelOne APIs.
-
Finally, select Save to store and activate the Connector.
You will now see SentinelOne added as a new Platform within the Query Search UI, the "platform" term is synonymous with "connector" and "integration".
Querying from the SentinelOne Singularity Platform Connector
Within the Query Search UI, all Platforms (A.K.A Connectors) are enabled by default, to check that SentinelOne is enabled, navigate to the Endpoint section of the Platforms dropdown and ensure that SentinelOne is selected (denoted by a checkbox) before running your searches as shown below.
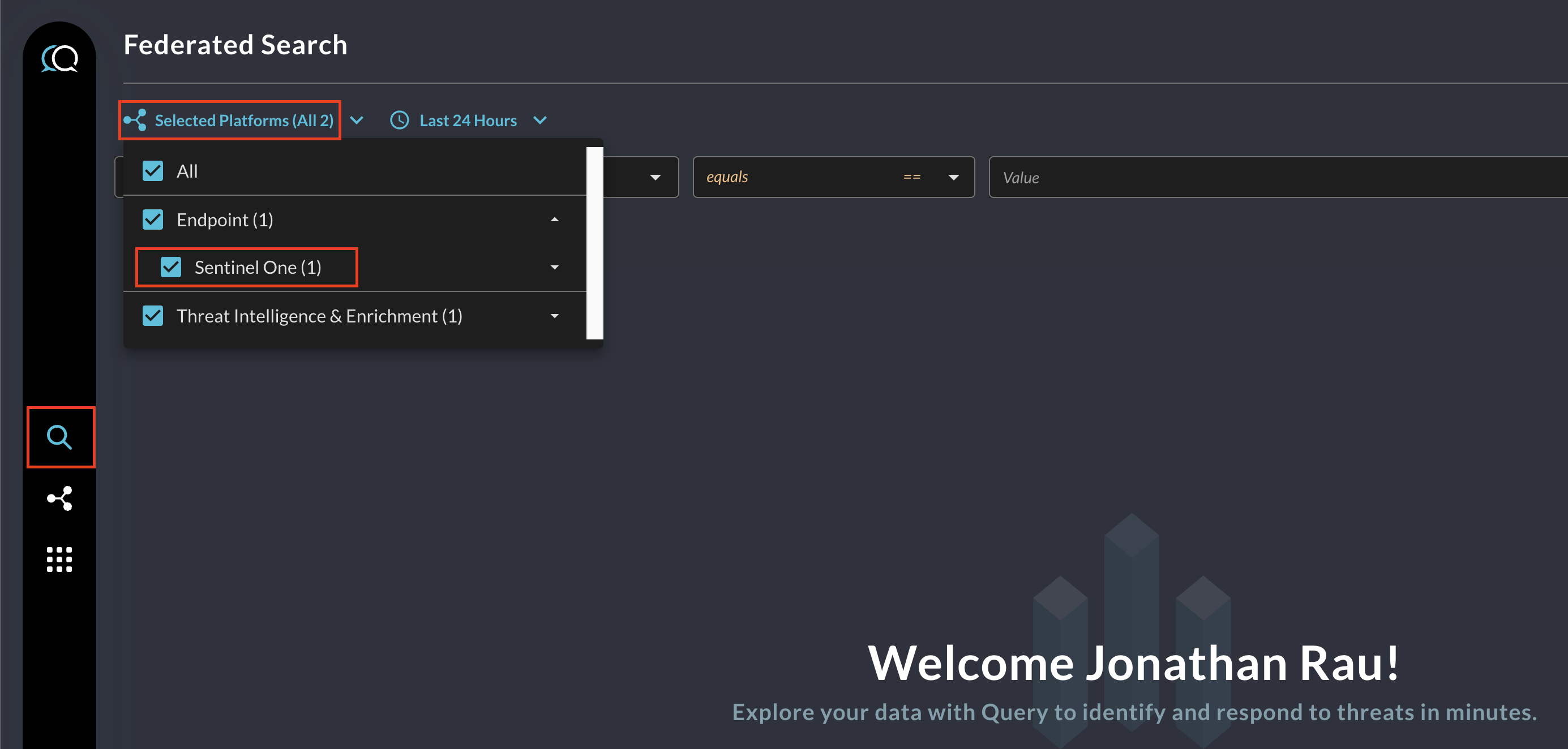
As of 1 NOV 2023, The Query Federated Search Platform supports retrieving the following information from SentinelOne Singularity Platform.
- Sentinels (A.K.A Agents/Devices)
- Threats
- Users
The following Entities, Events and Objects are supported by Query for those data points. For more information about this terminology, refer to the Normalization and the Query Data Model (QDM) section of the docs or check out our QDM Schema website.
Entities
- IP Address (e.g., IP Address EQ
192.168.1.1, IP Address CONTAINS192.168.) - Hostname (e.g., Hostname EQ
ip-192-168.1.1, Hostnames CONTAINScontoso) - Hash (from Threats, e.g., File Hash EQ
8a91e75242801e2687fa7c0892f042fdc5906593) - File Name (from Threats, e.g., Filename EQ
EquationGroup.zip, Filename CONTAINS.go) - Email Address (from Users, e.g., Email Address EQ
[email protected], Email Address CONTAINScontoso.org) - Username (from Users, e.g., Username EQ
Son Sam, Username CONTAINSsam)
Events
security_finding (2001)(Soon to be deprecated)
Objects
osdevicenetwork_interfacemalwarefindingandfinding_info(Deprecated)usergroup
Resources
For more information on SentinelOne Singularity for Endpoint, see here.
Updated 4 months ago