Azure Log Analytics
Integrate with Azure Log Analytics Workspace tables to search them on demand without writing KQL.
TL;DRTo integrate Microsoft Sentinel with Query:
- Create an App Registration (Enterprise Application) with a Client Secret.
- Grant the App Registration Service Principal the
Log Analytics ReaderIAM Role in your Azure Subscription(s).- Onboard one or more tables from your Log Analytics Workspace.
- Use Query Search to parallelize searches and surface details from any Azure Log Analytics table (e.g., from Microsoft Sentinel) for incident response (IR), threat hunting, investigations, and other security and observability use cases.
Overview
Azure Log Analytics is a time-series wide-column NoSQL-like logging service within the Azure Monitor ecosystem. Each workspace contains multiple tables organized into separated columns with multiple rows, defined by a set schema of columns that contains structured and semi-structured logging and event data. Logs and other data can be read from these tables using the Kusto Query Language (KQL) to perform detailed analyses or simple searches, and anything in between.
Azure Log Analytics Workspace tables can be populated by various means, such as the following.
- Microsoft Sentinel via Data connectors (e.g.,
AzureActivity) - Defender XDR (e.g.,
DeviceNetworkEvents) - Azure Monitor Agent (AMA) or Windows Monitoring Agent (WMA) (e.g.,
EventorOperation) - Custom ingest via Azure Monitor API or Azure Data Explorer (ADX) (e.g.,
my_cool_custom_logs_CL)
Query's entire data model is built around the Open Cybersecurity Schema Framework (OCSF) - named the Query Data Model (QDM) - which expresses all search intents with OCSF/QDM concepts such as Entities/Observables used to represent facts and indicators whereas Event Classes represent things that have happened and are normalized against network, application, file system, identity, and 1st party security findings.
Using the Query Data Model as a lingua franca (or, a "decoder ring"), all of your Query Builder searches are automatically translated into KQL downstream, freeing your team from needing to master another query language. Likewise, constraining the searches to the Query Data Model ensures that you cannot submit unsafe or notional queries which can expose unintended data or greatly increased costs downstream. Likewise, the query planner and execution engine in Query Federated Search parallelizes all searches. This allows you to avoid using the expensive join operator and instead returns all matching results to use similar to a SQL windowing function.
Teams use Azure Log Analytics primarily to interface with tables created by Microsoft Sentinel Data connectors as well as Defender XDR tables that contain sensor-level information about network activity, logins, processes, registry keys, and more. Additionally, teams use legacy and new AMAs and WMAs to collect important application, observability, and/or security relevant data directly from machines managed by Defender for Endpoint and/or Microsoft Azure VMs and DaaS. With Query, you can quickly search across all onboarded tables to support threat hunting activities, to find evidence to support investigations and incident response, or to perform audits of your compliance configurations.
Some details on searchesDue to the unpredictable and unbounded nature of the
dynamicdata type, Query does not support unnesting this data type.dynamiccolumns are instead cast as a string andcontainsoperators are used to provide an emulation of quantifier support.Up to 5000 results are provided per table, you can opt-in to Streaming and Pagination support to increase this limit which can raise costs and increase the time it takes to retrieve queries.
Only one table can be modeled at a time in Configure Schema.
Prerequisites
You must have Global Administrator permissions for your Entra ID tenant and Owner permissions for your Azure Subscription to be able to create an App Registration, generate Client Credentials, and grant the App Registration Service Principal proper roles in your Subscription to integrate with LAW tables.
Create an Application Registration & Grant an Azure Role
-
In the Microsoft Azure portal navigate to Microsoft Entra ID -> Add -> App Registration as shown below.
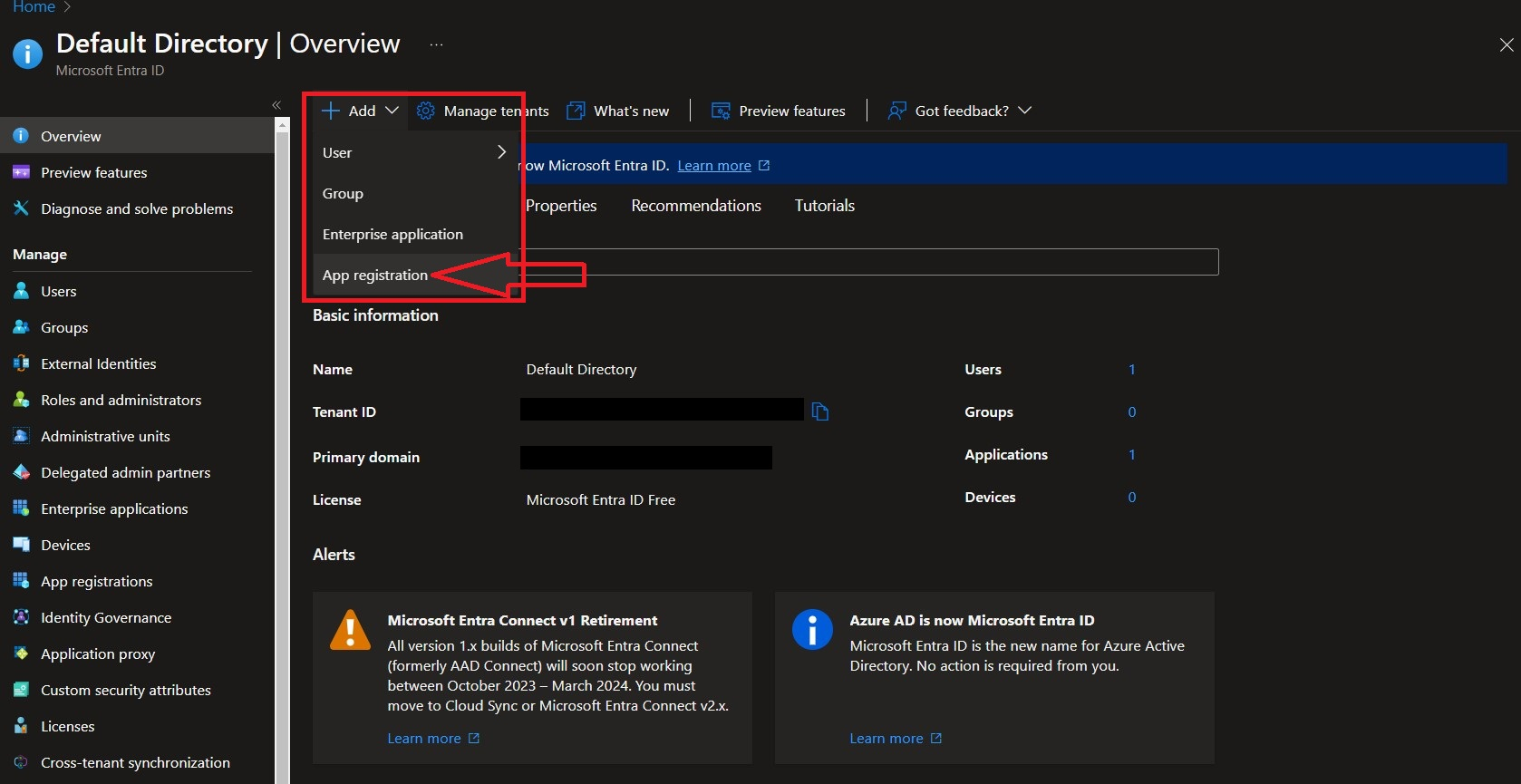
-
Populate a Name for the application, leave the Supported account types option as the default (
Accounts in this organizational directory only (Default Directory only - Single tenant)) then select Register as shown below.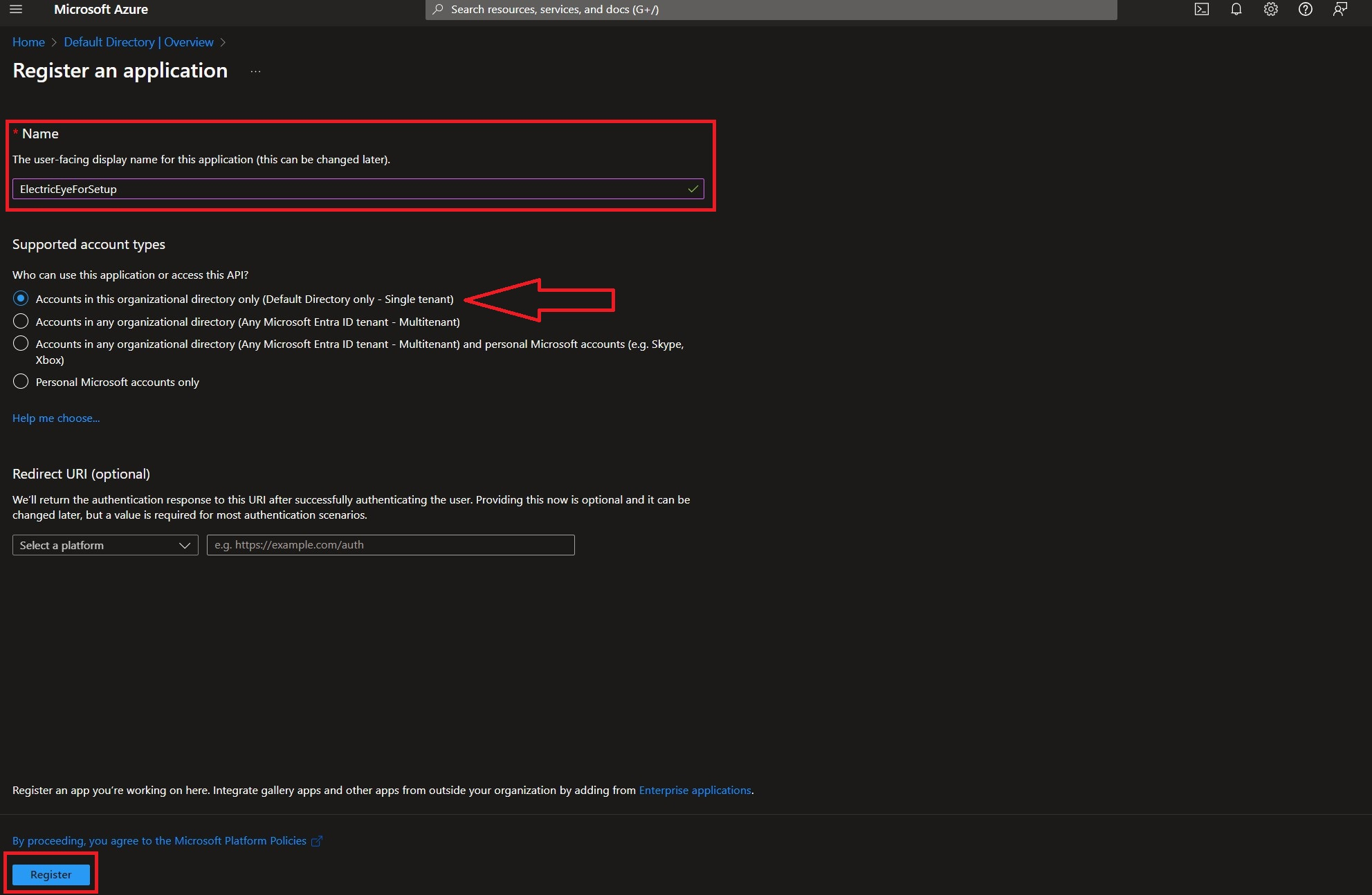
-
By default you will be taken to the Overview screen of your new application. Navigate to Certificates & Secrets -> Client Secrets -> New client secret. Enter a Description, choose an Expires date from the selector, and finally choose Add as shown below.
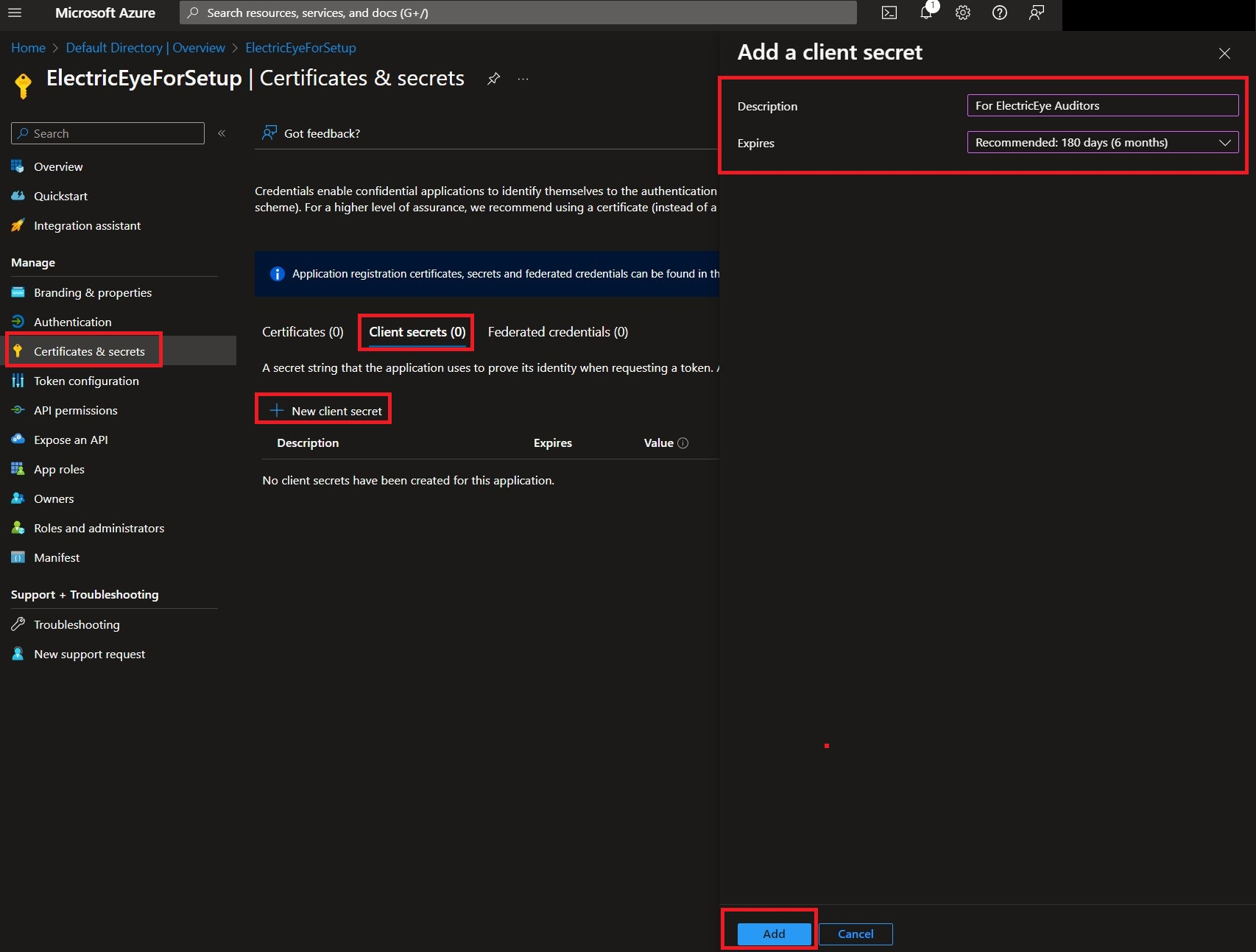
-
WARNING! Before navigating away copy the Value entry and save it somewhere secure, this is the Client Secret Value required to perform authentication into your Azure Subscriptions. If you did not copy it, no big deal, just delete the Client Secret and create another - but remember to copy the Value that time.
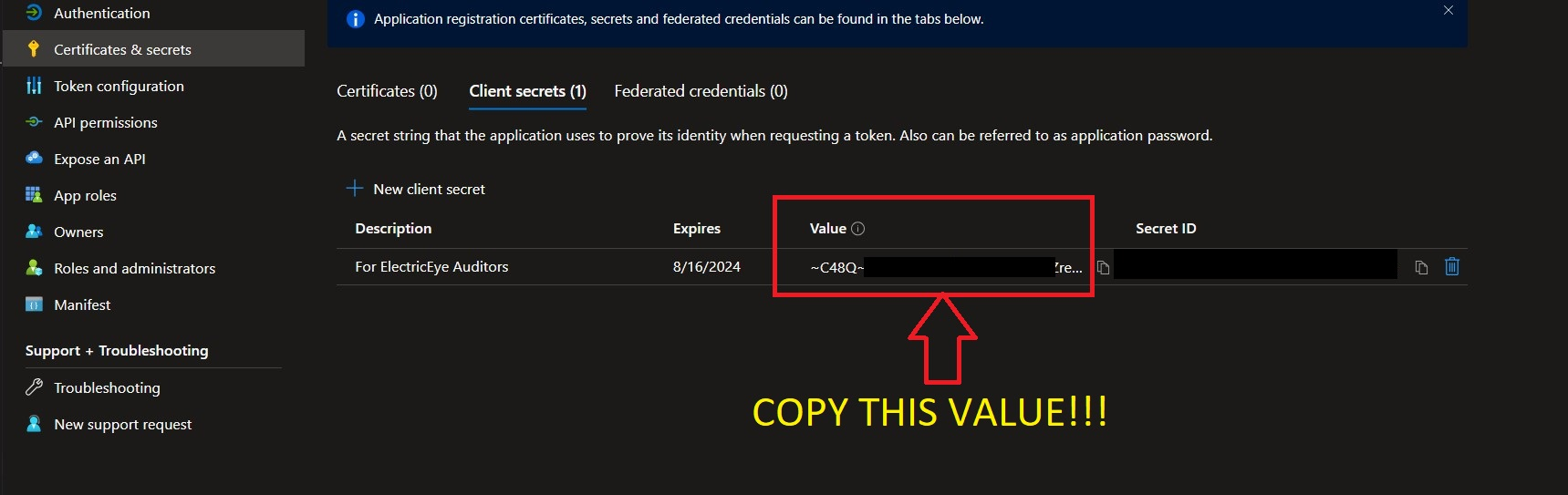
-
Navigate to the Overview screen and copy the values for the Application (client) ID and Directory (tenant ID) as shown below. The App ID and Tenant ID are also required to perform authentication into your Azure subscription.
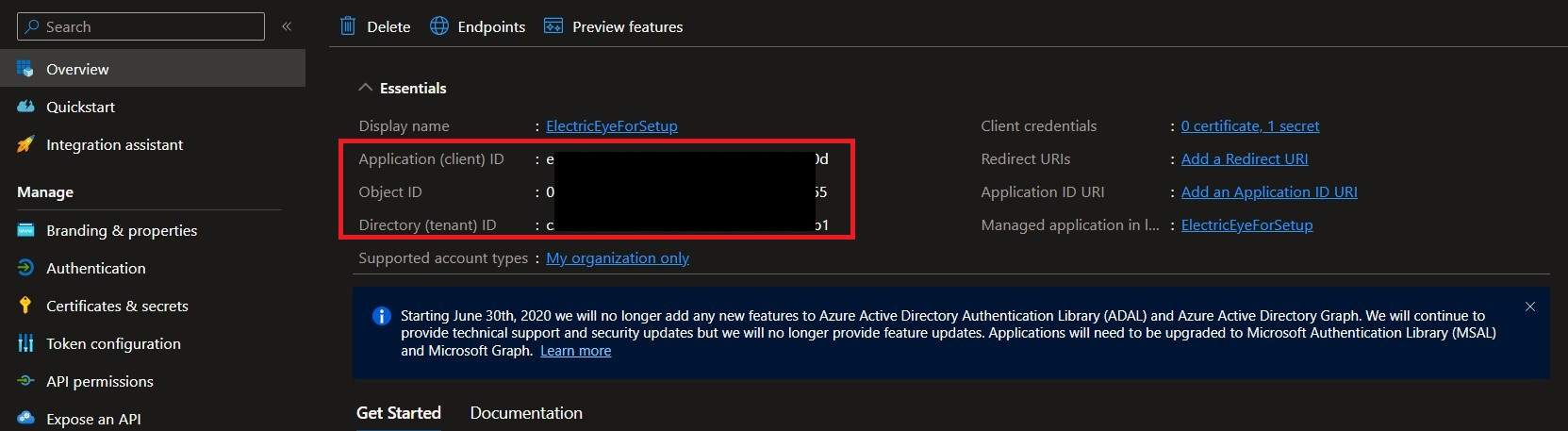
-
-
Before moving to the next section, copy the Tenant ID, App (Client) ID, and the App Secret Value as these are required for the Query Connectors to configure access.
Retrieve Log Analytics Workspace and Resource Group information
In addition to the App Registration information, you will need to retrieve your Log Analytics Workspace ID and the name of the table(s) you wish to connect.
-
Navigate to the Microsoft Azure portal -> Log Analytics workspaces -> your Microsoft Sentinel's Workspace name -> Overview
-
Copy the value of Workspace ID as shown below.
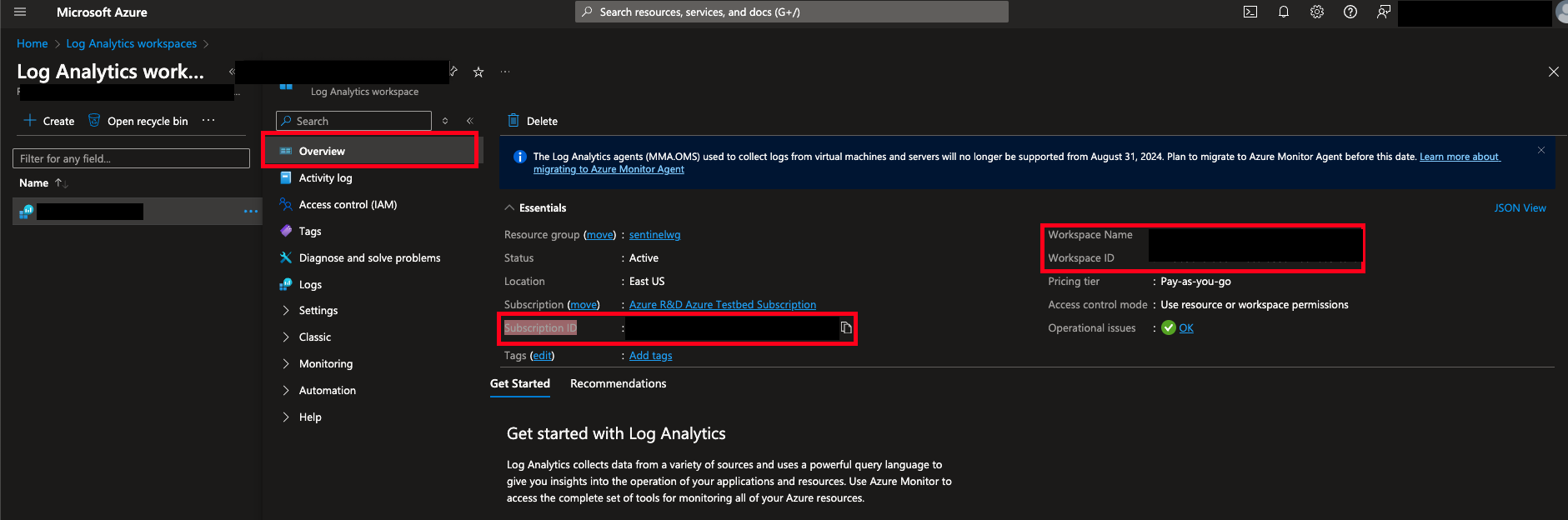
-
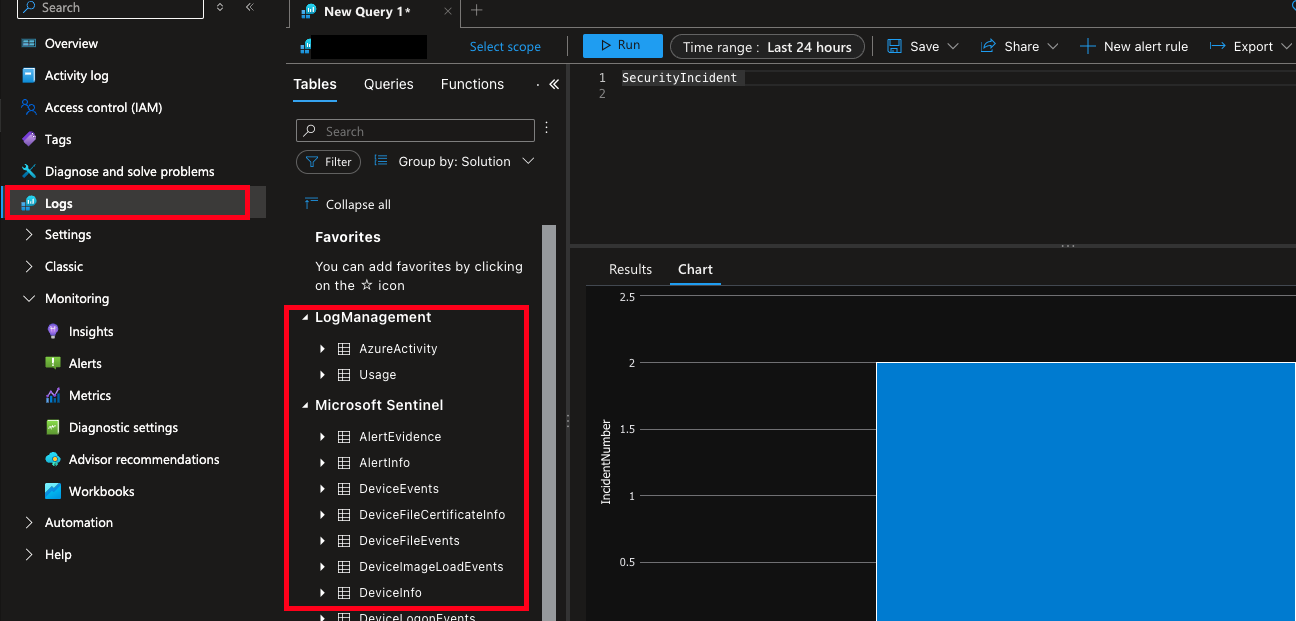
To retrieve table names, navigate to Logs and expand the various headers as shown below. These should correspond to active Microsoft Sentinel Connectors as well as any individual tables you have created within Azure Log Analytics.
In this section you learned how to create a new App Registration, grant it Azure Subscription IAM roles, and retrieve Azure LAW attributes. In the next section you will learn how to configure the Azure Log Analytics Connector.
Configuring Microsoft Sentinel Connectors
There are two types of Connectors available for Microsoft Sentinel, one solely for querying Incidents from Sentinel and another for querying LAW tables. The information you copied in the previous section will be use for both Connectors, no other permissions or external configuration is required.
Configure the Azure Log Analytics Connector
The Azure Log Analytics Connector uses the Microsoft Azure Azure Monitor Logs SDK to describe and introspect schema from Log Analytics Workspace tables, submit KQL queries, and retrieve results from the queries.
The Azure Log Analytics Connector is a dynamic schema platform configurations. Static schemas are platforms in which the Query team pre-configures the type of data normalization that happens and a dynamic schema platform gives the user control for mapping and normalizing data into the Query Data Model. '
For dynamic schemas, Query provides a no-code data mapping workflow to allow you to map your source data into the Query Data Model. For more information, see the Configure Schema and the Normalization and the Query Data Model sections, respectively.
Configure Schema LimitationsDue to limitations in the introspection and mapping process, you may only map one Log Analytics table per Connector. There are not any limits to the amount of Connectors you can create.
Use the following steps to create a new Query Federated Search Connector for Azure Log Analytics.
-
Navigate to the Connections page, select Add Connections, and selectAzure Log Analytics from the SIEM and Log Management category as shown below. Alternatively you can use the search bar to find the Connector.
-
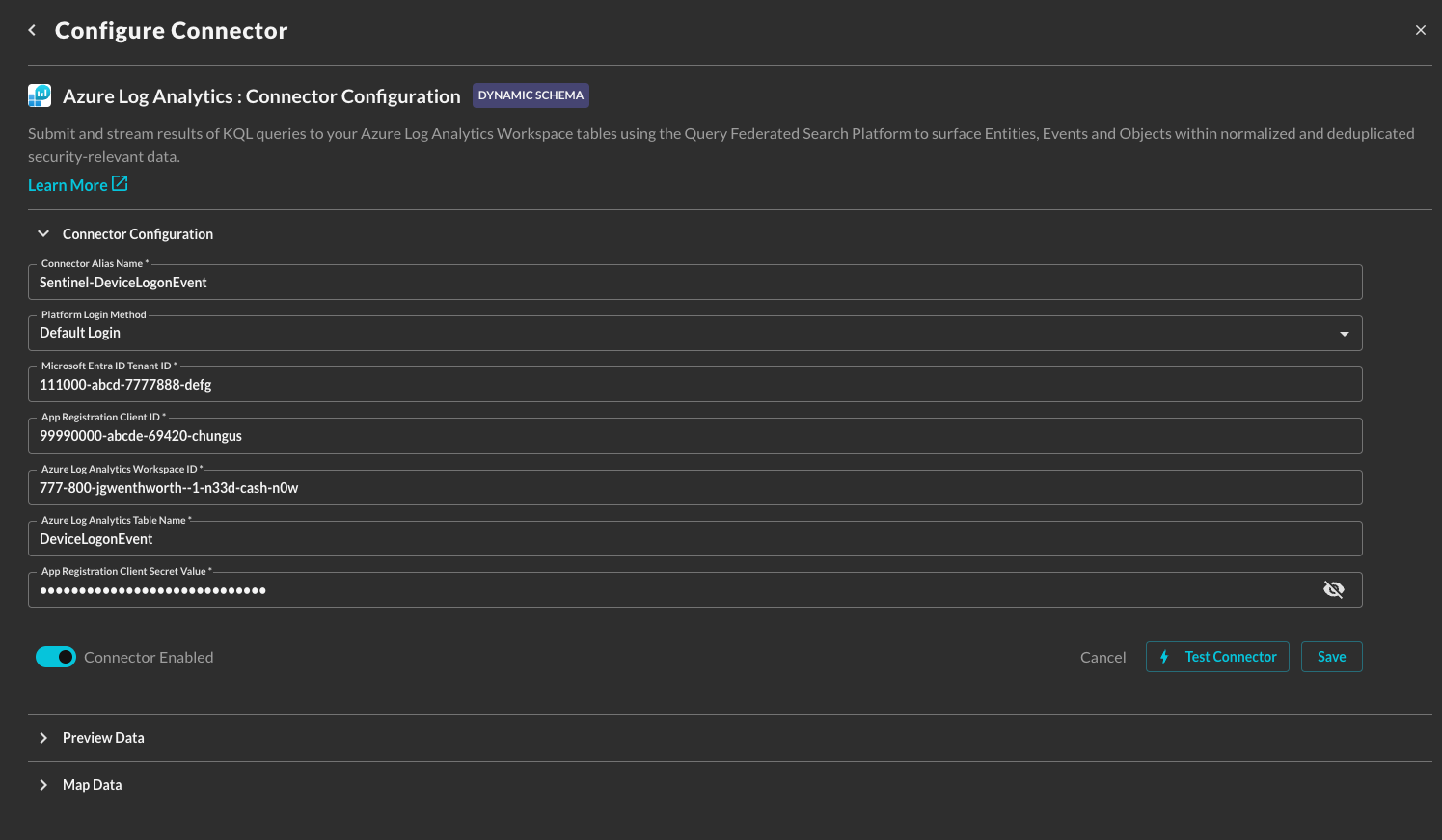
In the Connection Info section of the platform connector, provide the following details, select Save, and then Test Connection as shown below (FIG. 11).
- Connector Alias Name: The human-readable name you want to give to this connector, you can name it whatever you want, but you can use this to differentiate multiple Sentinel deployments across various Azure Subscriptions.
- Platform Login Method: Leave the default value:
Default Login. - Microsoft Entra ID Tenant ID : The Tenant ID (also known as the Directory ID) for the Microsoft Entra ID tenant associated with your Azure Subscription.
- App Registration Client ID : The Client ID (also know as the Application ID) for the Entra ID App Registration you created in the Prerequisites section.
- Azure Log Analytics Workspace ID : The ID of your Azure Log Analytics Workspace associated with your Microsoft Sentinel deployment.
- Azure Log Analytics Table Name : Name of the table in Azure Log Analytics - these tables do not need to be associated with Microsoft Sentinel to work.
- App Registration Client Secret Value : The Client Secret Value for the credentials you created for your App Registration.
-
Select Save to save and activate the Connector.
-
Select Test Connection from the bottom-right of the connection pane to ensure that your Enterprise Application credentials are valid and that you have the IAM permissions to access Log Analytics. Finally, your Log Analytics Workspace ID and tables are validated by attempting a
limit 1KQL query against it. -
Finally, proceed to the Preview Data section to begin the Configure Schema process. Refer to the hyperlink to learn how to use the Configure Schema no-code workflow, it is HIGHLY recommended for first time users.
After completing the Configure Schema workflow, you are ready to perform Federated Searches against your Log Analytics tables.
Querying the Microsoft Sentinel Connectors
After you have onboarded at least one Azure Log Analytics Connector, you are ready to begin searching. Within the Query Federated Search and Query Summary Insights UI, all Platforms are enabled by default.
To either ensure your Microsoft Sentinel Connectors are enabled, or to only query them specifically, navigate to the SIEM and Log Management section of the Selected Platforms dropdown menu and ensure the checkbox is (de)selected to match your desired search criteria, as shown below.
The Azure Log Analytics Connector allows you to search whatever you configured during the Configure Schema workflow.
For more information about this terminology, refer to the Normalization and the Query Data Model (QDM) section of the docs or check out our QDM Schema website.
Resources
For more information to help with troubleshooting or general information about Microsoft Sentinel and its related services, refer to the links below.
Updated 4 months ago