CrowdStrike Falcon Identity Protection
Integrate CrowdStrike Falcon Identity Protection with the Query Security Data Mesh to retrieve details about identity protection sensors and zero trust assessments.
TL;DRTo integrate CrowdStrike Falcon Identity Protection with the Query Security Data Mesh:
- Create an API Client with the
Identity Protection EntitiesandZero Trust AssessmentREAD scopes.- Configure a CrowdStrike Falcon Identity Protection Connector with your Client ID, Client Secret, and (optionally) API endpoint base URL.
- Use the CrowdStrike Falcon Identity Protection Connector for the Query Security Data Mesh to search for non-compliant or risky sensors, as well as hosts with poor Zero Trust Assessment scores to support Identity Threat Detection, Incident Response, and Threat Hunting use cases.
Overview
The CrowdStrike Falcon platform is a multi-domain Endpoint Protection Platform (EPP) that includes Identity Threat Detection and Response (ITDR) capabilities through its Falcon Identity Protection module. CrowdStrike Falcon Identity Protection helps organizations protect their identity infrastructure by monitoring sensors and conducting zero trust assessments across their environment.
The Query Security Data Mesh integrates with CrowdStrike Falcon Identity Protection APIs to enable security teams to query and investigate identity protection sensors and zero trust assessment data. The Query Security Data Mesh utilizes the FalconPy official SDK to securely access data, submit searches, and normalize the results. Federated search allows customers to support Identity Threat Detection, Incident Response, Threat Hunting, and other security tasks that require Falcon Identity Protection data. This is all done without duplicating or retaining data in another system.
Other CrowdStrike IntegrationsQuery offers additional CrowdStrike integrations to complement your Identity Protection deployment:
- CrowdStrike Falcon Connector - Comprehensive integration with Falcon EDR APIs including alerts, detects, incidents, hosts, and user management
- CrowdStrike Falcon Spotlight - Dedicated vulnerability management integration for Spotlight vulnerability data
Additionally, Query has an open source project named Query Open Pipeline for CrowdStrike FDR that will extract, transform, and load ~200 FDR events into OCSF 1.2.0 for ingestion into Amazon Security Lake.
Finally, we also have an integrate with the CrowdStrike Falcon Next Gen SIEM (NGS) for more dynamic data sources stored in NGS Repositories.
All federated searches have their searches and results expressed in the terms of the Query Data Model (QDM), which is based on the Open Cybersecurity Schema Framework (OCSF). Each API source is normalized into a specific QDM/OCSF Event Class to standardize and normalize the data for increased situational awareness, ease of aggregation of filtering, and easy pivoting. Each Event Class also supports searching by Entities, which are based on OCSF Observables for quick broad searches for common indicators and notables within your data.
API Name | QDM/OCSF Event Class | Supported Entities |
|---|---|---|
Identity Protection (Sensors) | IP Address Hostname Resource ID | |
Zero Trust Assessment (Assessments) | Hostname Resource ID |
Executing federated searches with Query allows you to pull all relevant Identity Protection data for your search criteria back in a parallelized, normalized, and standardized format without ever moving or duplicating the data into another data repository.
For instance, searching for a specific IP Address or Hostname Entity in Query will allow you to pull all relevant Identity Protection sensor records and Zero Trust Assessment data. You can also perform specific searches such as retrieving sensors with poor compliance scores, identifying hosts with failed zero trust assessments, or correlating identity protection events with data from other security tools.
Searching for a specific Resource ID (based on aid) allows you to retrieve all relevant Identity Protection sensor data and Zero Trust Assessments for that host, enabling your analysts to perform quicker triage and allowing hunters to further pivot across to other Query Security Data Mesh Connectors such as raw process, network, or identity logs in CrowdStrike Falcon LogScale, Azure Log Analytics, Entra ID, or other integrated platforms.
Prerequisites
To create an API Client to integrate CrowdStrike Falcon Identity Protection with the Query Security Data Mesh, see the following steps.
- Login to your CrowdStrike Falcon console, you will require an account with permission to create API keys.
- In the dropdown navigation menu in the upper-left of your Console, select Support and Resources --> API clients and keys as shown below (FIG. 1).
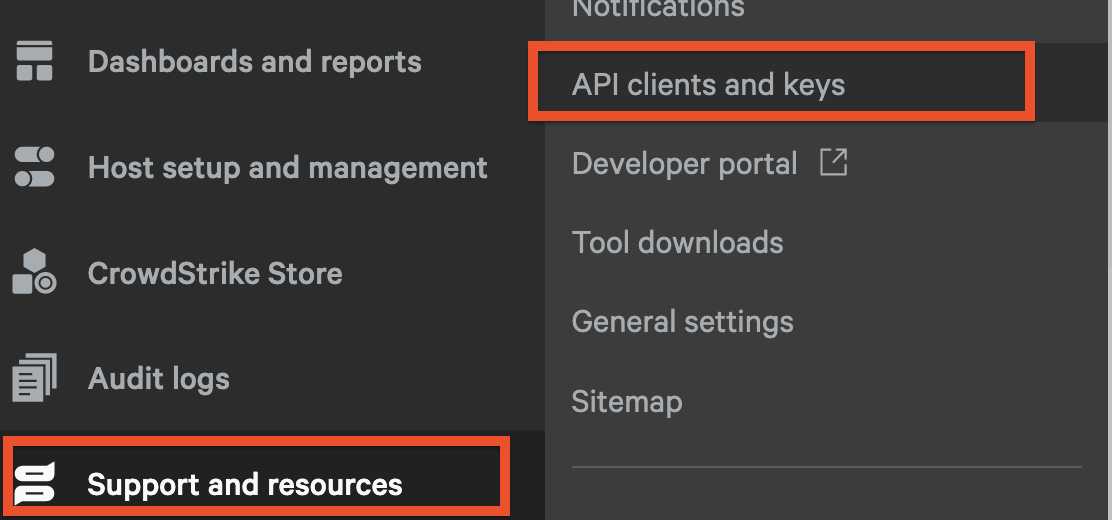
FIG. 1 - API Clients and Keys menu in the CrowdStrike Falcon console
-
Next, select Create API client in the upper right corner as shown below (FIG. 2).
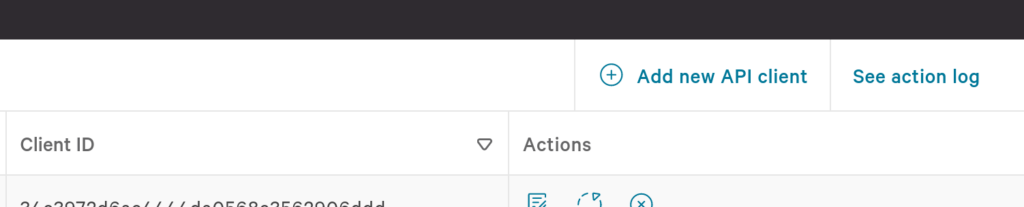
FIG. 2 - Create a new CrowdStrike API Client
-
Enter a Client name, an optional Description and add the following Scopes as shown below (FIG. 3).
Identity Protection Entities(Read)Zero Trust Assessment(Read)
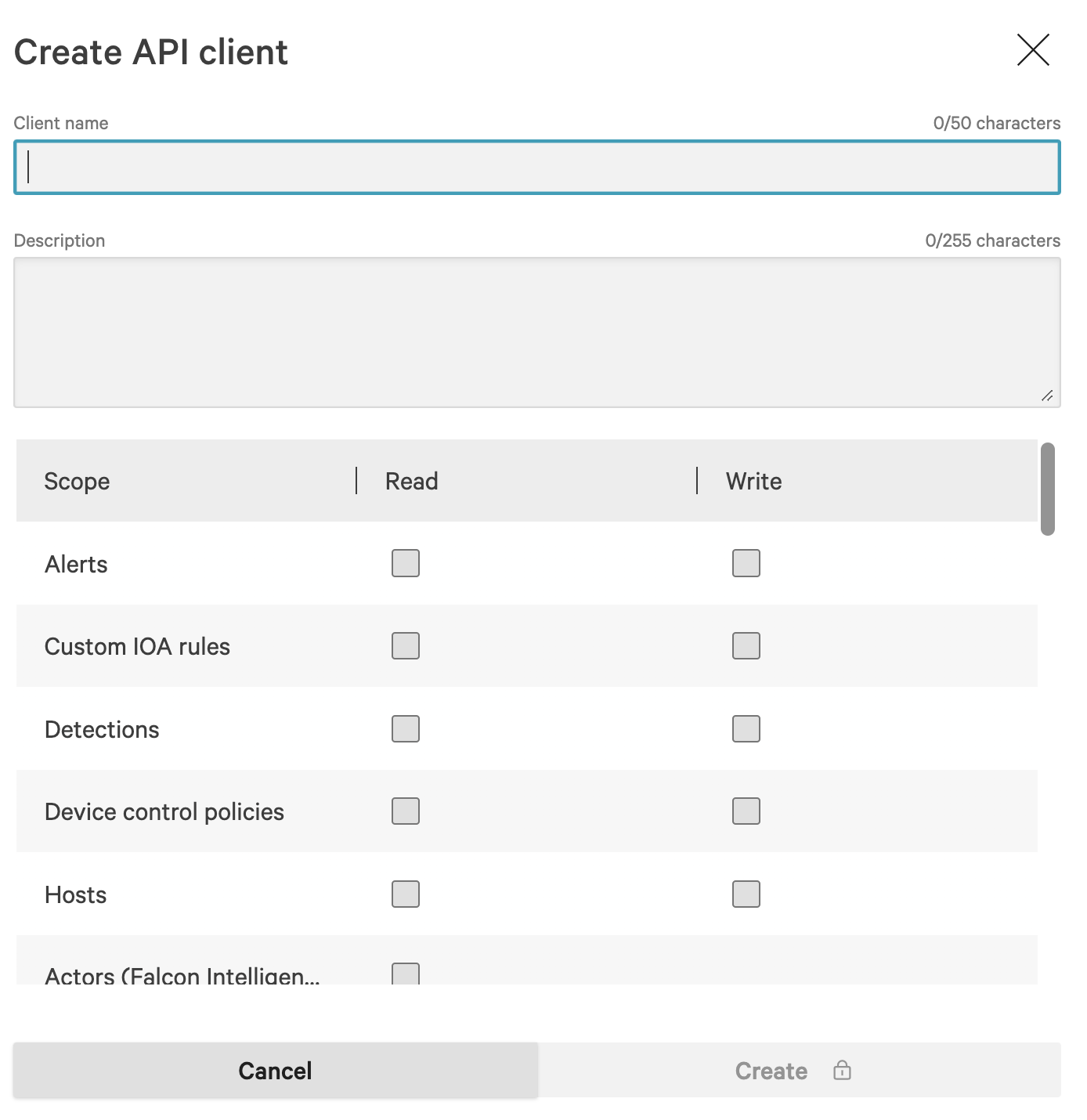
FIG. 3 - API Client configuration wizard
-
When complete, select Save and copy the Client ID and Secret to configure your Query Security Data Mesh Connector in the next section, as shown below (FIG. 4).
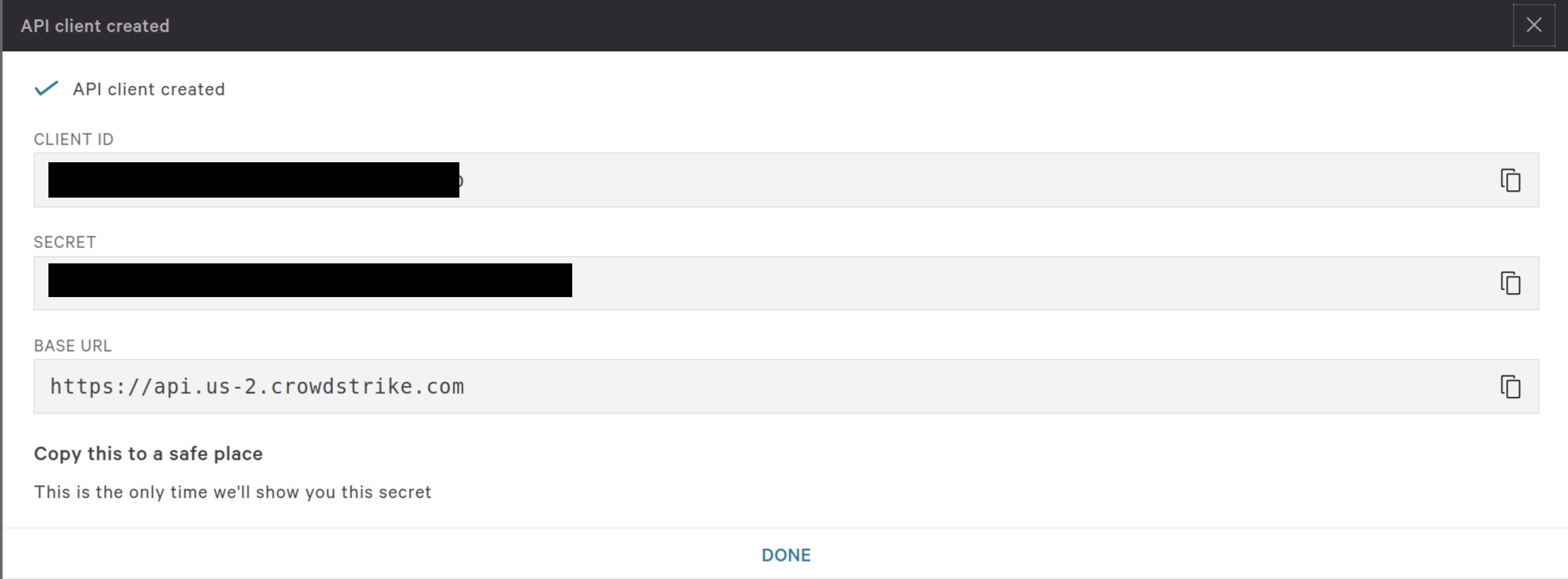
FIG. 4 - Copying the Client ID, Secret, and Base URL from the CrowdStrike API Client
Optionally, but not required, you can provide a specific API base URL if you have a us.gov or eu tenant for instance. This is not required, as all connectivity with FalconPy defaults to a generic base URL and is discovered from your client credentials.
On NHI securityNHI - or, Non-Human Identities - such as your CrowdStrike API Client credentials are extremely sensitive, even with limited read Scopes. Query securely stores the Client Secret in a dedicated AWS Secrets Manager Secret per Connector per Tenant.
Every Secret is stored as securely as each other with minimum necessary permissions that only allows the specific piece of serverless infrastructure to retrieve the secret, it is never cached or persisted outside of the Secret.
Configure the CrowdStrike Falcon Identity Protection Connector
Use the following steps to create a new Query Security Data Mesh Connector for CrowdStrike Falcon Identity Protection.
-
Navigate to the Connectors page, select Add Connector, and select CrowdStrike Falcon from the Endpoint category as shown below (FIG. 5). Alternatively you can use the search bar to find the Connector.

FIG. 5 - Adding the CrowdStrike Falcon Connector
-
In the Configure Connector section, add the following detail as shown below (FIG. 6):
-
Connector Alias Name: The human-readable name you want to give to this connector, such as "CrowdStrike Identity Protection" or a tenant-specific name, especially if you setup multiple connectors to support a MDR/MSSP offering or have multiple subsidiaries or tenants.
-
Default Login: Leave the default value:
Default Login. -
Falcon API Client ID: The ID for your Falcon API Client, copied in Step 5 of the Prerequisites section.
-
Falcon Secret Access Key: The Client Secret of your Falcon API Client, copied in Step 5 of the Prerequisites section.
-
Falcon API Base URL: (OPTIONAL STEP) the region-specific base URL of your Falcon API.
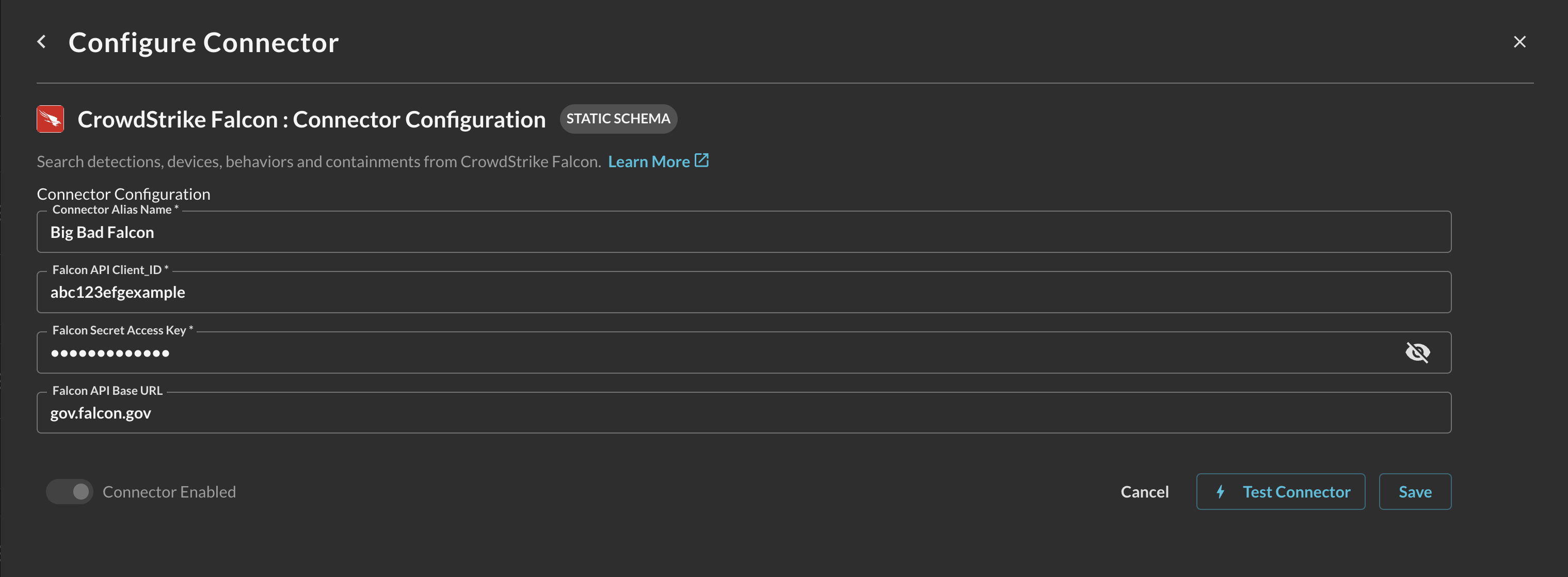
FIG. 6 - Configuration details for the CrowdStrike Falcon Identity Protection Connector
-
-
Select Save to save and activate the Connector.
-
Select Test Connection from the bottom-right of the connection pane to ensure that your API Client credentials are valid, that your base URL is valid, and that Query can successfully dispatch a search against the Identity Protection APIs.
You will now see CrowdStrike Falcon Identity Protection added as an available Connector within the Query Search and Query Summary Insights UI.
Querying CrowdStrike Falcon Identity Protection with the Query Security Data Mesh
Within the Query Search UI, all Connectors are enabled by default. To check that your specified Connector(s) for CrowdStrike Falcon Identity Protection are enabled, navigate to the Endpoint section of the Selected Connectors dropdown and ensure that your specified CrowdStrike Falcon Connector(s) are selected (denoted by a checkbox) before running your searches as shown below (FIG. 7).
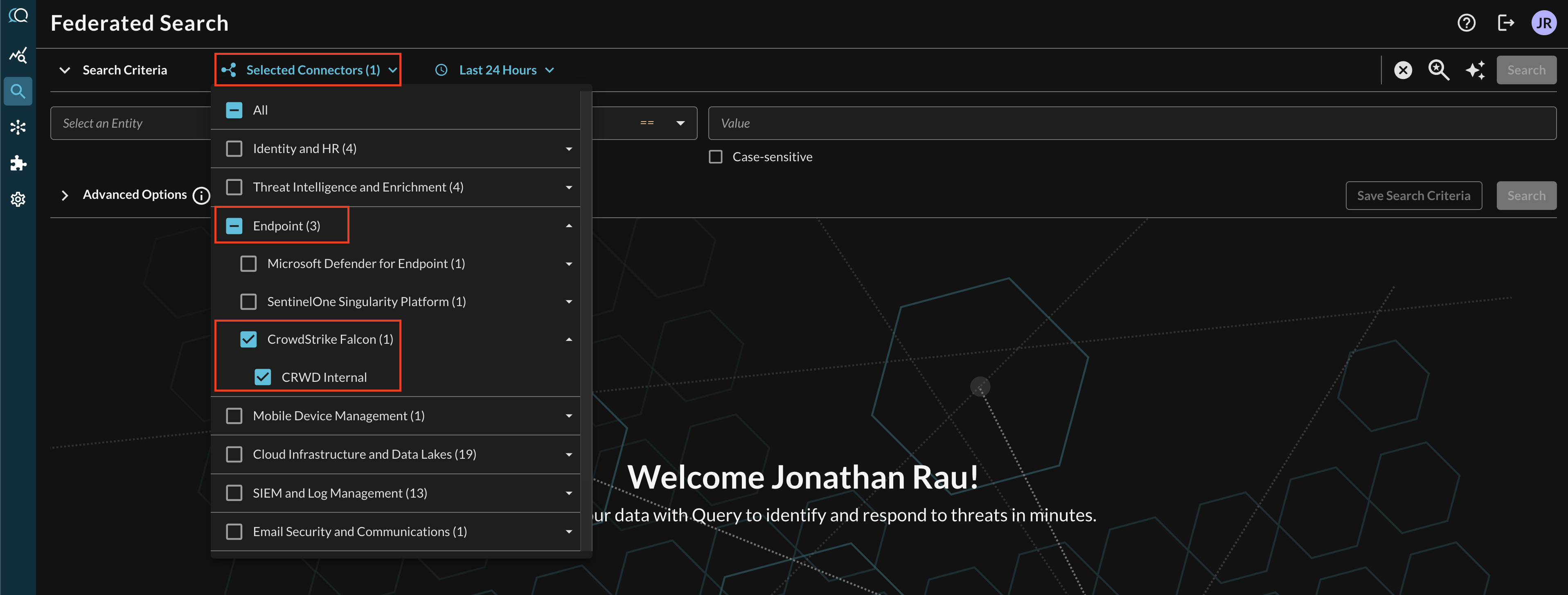
FIG. 7 - Enabling/Disabling the CrowdStrike Falcon Identity Protection Connector(s)
To learn more about searching with CrowdStrike Falcon Identity Protection in the Query Security Data Mesh, refer to the subsections below.
Resources
- CrowdStrike Developer Center
- How to create CrowdStrike API Client key?
- How to: regenerate API Client's secret Key
- API 403 Status Code
Troubleshooting Tips
- Ensure that you have added the required
Identity Protection EntitiesandZero Trust AssessmentScopes to your API Client. - Ensure that you have copied the correct Client ID and Secret, or that the API Client has not been deleted or had its credentials rotated.
- Ensure that you entered the Client ID and Secret in the proper parameters in the CrowdStrike Falcon Identity Protection Connector.
- Ensure that you have granted the correct READ Scopes as described in the prerequisites.
- Ensure that your CrowdStrike tenant has the proper Licenses to provide access to the Identity Protection APIs - HTTP Status Code 403 is supplied for both missing Scopes and Licensing.
- Ensure that if you provided a base URL, that it is a correct URL.
If you have exhausted the above Troubleshooting list, please contact your designated Query Sales Engineer or Customer Success Manager. If you are using a free tenant, please contact Query Customer Success via the Support email in the Help section, or via Intercom within your tenant.
Updated 3 months ago